Cymulate Identifies Cyberattack Technique That Evades EDR Platforms
Cymulate, a cybersecurity posture assessment platform provider, shared a technique, dubbed Blindside, that enables malware to evade some endpoint detection and response (EDR) platforms and other monitoring/control systems.
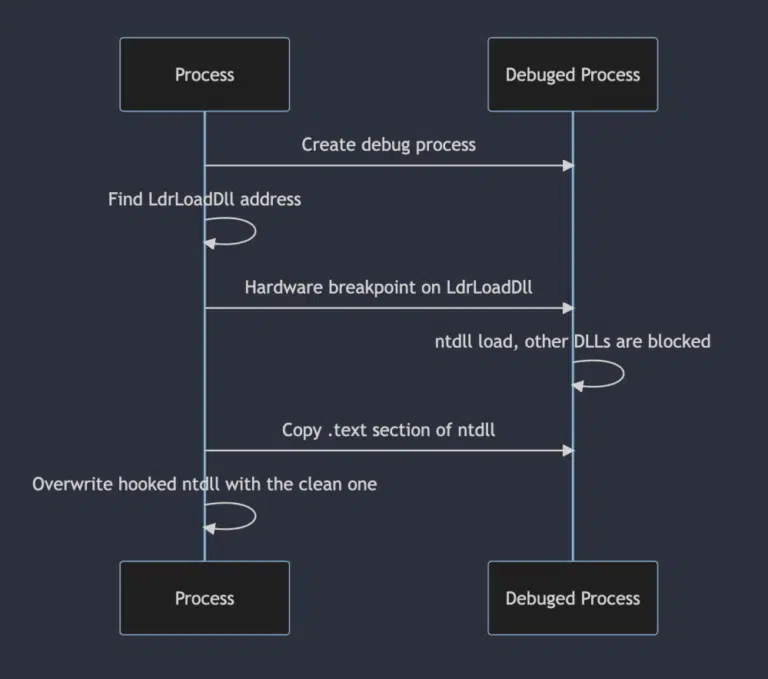
Mike DeNapoli, director of technical messaging at Cymulate, said company researchers discovered that by using breakpoints to inject commands to perform unexpected, unwanted or malicious operations, it becomes possible to create a clean version of an ntdll file that lacks the hooks that many EDR platforms rely on to identify these types of attacks. Once created, it’s possible to then copy the memory of the clean ntdll into an existing process in a way that unhooks all previously hooked syscalls, he noted.
The Blindside technique essentially leverages techniques used to debug software to instead execute arbitrary code. When a process is first created, ntdll.dll will automatically be loaded. The breakpoint blocks the loading of the additional dlls by hooking LdrLoadDLL to create a process with only the ntdll in a stand-alone, unhooked state.
Cybercriminals are getting more adept at techniques and sophisticated attacks that evade cybersecurity defenses. It’s critical for cybersecurity teams to regularly validate whether the cybersecurity platforms they have in place can detect new types of threats as they evolve, said DeNapoli. Unfortunately, too many cybersecurity teams deploy a platform in a set-it-and-forget-it mindset that leaves their organization less secure than they expect, he added.
Even if only a small percentage of cybercriminals have the skills required to develop these attacks, there is no shortage of mechanisms in place for them to share the code they create with other cybercriminals.
Cybersecurity will become more challenging in the months ahead as regulatory bodies such as the Securities and Exchange Commission (SEC) require organizations to disclose breaches and detail what steps they have taken to make their IT environments more secure, noted DeNapoli. As a result, organizations will no longer be able to ignore any shortcomings of the cybersecurity platforms they are employing, he added.
For better or worse, there’s no doubt that C-level executives are paying more attention to cybersecurity than ever. The challenge is many of them don’t have an appreciation for all the nuances involved. Throwing money at cybersecurity does not always have the impact expected as techniques and tactics evolve. Platforms that are being used today to successfully thwart attacks may need to be extended to address new classes of threats as they emerge.
In the meantime, it’s certain cybercriminals will continue to hone their skills. Cybercriminals are now organized in syndicates that enable them to specialize in various areas. As each of those teams advances their skillsets, it becomes more difficult for law enforcement officials to identify all the members of any given syndicate. As a result, cybersecurity winds up being a never-ending battle where it’s impossible to win every single engagement. Rather, the goal is to win as many battles as possible while minimizing the blast radius when things eventually go wrong.