Buran Ransomware Looks To Undercut the Competition
Recent research estimates that ransomware attacks against enterprises have increased year on year by approximately 500%. Given that Cyber Monday and Black Friday are within striking distance, a surge in ransomware infections should be not only expected but also actively defended against. One ransomware variant that can be expected to make its mark on the holiday season is a relatively new one named Buran.
Buran was discovered in May by security researcher nao_sec. Its operators were quick to choose a path that, if done correctly, would net them far more cash than if they distributed the ransomware themselves. By adopting a ransomware-as-a-service (RaaS) business model, the operators are looking to create an army of affiliates to distribute the ransomware, hopefully netting them a tidy sum of Bitcoin in the process. RaaS tends to operate by allowing affiliates to distribute the ransomware, while the creators of the ransomware take a percentage of the ransoms extorted by the affiliates.
VegaLocker
Analysis conducted by security researchers revealed that Buran is not an entirely new threat; rather, the code shares several artifacts with a previous ransomware family, Jumper or Jamper, which is itself an evolution of VegaLocker. Other similarities, such as how files are stored in the temporary folder and how the ransomware modifies the registry, were noted by researchers. However, these factors only indicate a relationship; one of the key pieces of evidence linking the above families to one another is how they all use the same methods to delete shadow copies, backups and the system backup.
One of the last known campaigns seen when VegaLocker was distributed occurred in late 2018 to April 2019. The ransomware was dropped as a payload after a malvertising campaign successfully compromised machines. VegaLocker was not the only payload—the campaign also looked to spread banking trojans and spyware. Later ransomware payloads distributed by the malvertising campaign were believed to be Buran; however, they were later proved to be VegaLocker, its grandfather of sorts. This may have been the ransomware’s swan song, only to make way for operators dedicating their time to Buran. This also lends credence to the idea of Buran being an evolution of VegaLocker.
Buran
Buran is advertised on underground forums as a stable strain of malware that boasts an offline cryptographic component, 24/7 support, global and session keys and no third-party dependencies such as libraries. For the most part, the researchers agree with the advert. They further discovered that the ransomware is capable of scanning for local drives and network paths. Buran also can encrypt files without changing the file extension, remove recovery points, delete logs and delete backup catalogs. It also is capable of deleting itself.
Screenshot of files encrypted by Buran ransomware:
Where the operators of Buran may have fibbed a little is that they state that the ransomware is compatible with all versions of Windows. The research found this not to be the case, as Windows XP appears to be immune. As with Sodinokibi, another popular ransomware offered as a RaaS, the RIG exploit kit appears to be the current preferred method of distribution. In particular, the ransomware takes advantage of CVE-2018-8174 to allow for the initial compromise of machines. The vulnerability also goes by the name Windows VBScript Engine Remote Code Execution Vulnerability and is classified as a remote code execution vulnerability that allows malicious code to be executed by abusing the way VBScript engine handles objects in memory. The vulnerability affects Windows 7, Windows Server 2012 R2, Windows RT 8.1, Windows Server 2008, Windows Server 2012, Windows 8.1, Windows Server 2016, Windows Server 2008 R2, Windows 10 and Windows 10 Servers.
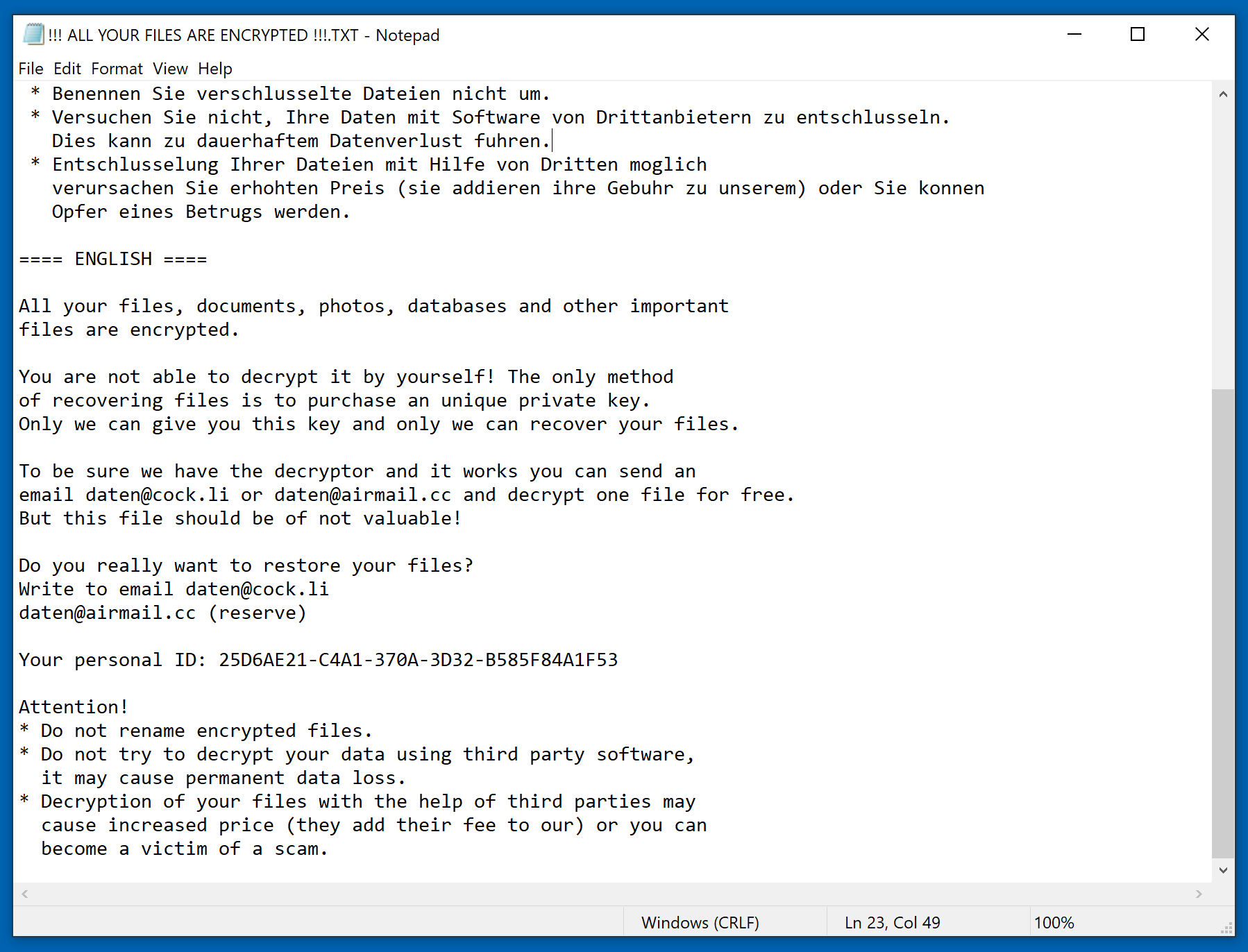
Screenshot of a ransom demanding message displayed by this ransomware:
Currently, there have been two versions of Buran detected so far, both written in Delphi. The second version shows improvements over the first. Improving the code is necessary for malware looking to be distributed by affiliates, as they will want improvements to avoid detection and infect machines. This is also a hallmark of RaaS models, as the ransomware itself needs to attract affiliates and they are unlikely to sign up if the malware is perceived to be outdated. Once Buran is dropped on a vulnerable system, it will check to see if the machine is registered in Belarus, Russia or Ukraine. If the check returns true, then Buran will exit.
Another feature of the malware worth noting is that it is capable of creating files and storing them on temporary folders. Buran will also look to maintain persistence on the infected computer by creating registry keys. This tactic of maintaining persistence was also found on Jumper and VegaLocker. That the code is written in Delphi is also interesting in that the code was predominantly taught in Latin America and former countries that made up the Soviet Union. Given that the code excludes machines registered in Russia, Belarus and Ukraine, some have speculated that the operators of the ransomware may be operating in one of those three countries.
Buran Targets German Companies
In October, reports emerged that German companies were actively being targeted in a campaign distributing Buran. The organizations were being targeted via a malspam campaign using an eFax lure in conjunction with a malicious Word document. The ransom note was also translated to German and contained the German word for data—“daten.” The spam email contained links to a PHP page that served the malicious Word documents which would download the ransomware, presumably through the use of enabling macros. By using hyperlinks rather than attachments, it is believed those behind the campaign were attempting to avoid detection by malware scanners set up to block spam emails.
This targeting of German organizations, as well as other campaigns, shows that Buran is not distributed in a hyper-targeted way. Rather, the malware is adapted to the need of the affiliates behind a certain campaign. The malware used in such a way is often referred to as commodity malware, as no specific target molds its development.
The main aim of the developers is to make money. To keep making money, Buran performs several anti-forensic features to prevent detection and analysis by security researchers. For example, Buran deletes the RDP connection logs, even though the ransomware is not distributed via RDP connections. These anti-forensic measures are noisy and alert those defending networks, but it appears that the developers are more concerned with deleting evidence rather than early detection of the ransomware.
Undercutting the Competition
Buran is not the first, nor the last, piece of ransomware to be offered as a RaaS. Currently, Sodinokibi follows a similar business model, and GandCrab practically perfected the business model. To get an edge over the competition, Buran’s developers are employing an age-old business tactic rather than a novel or new code and technologies: undercutting their rivals.
Normally RaaS developers charge anywhere between 30% to 40% of successful infections resulting in ransom payment. Buran operators are charging only 25%, substantial savings for those looking to extort funds but could not be bothered to develop the ransomware. That is not all the developers of Buran are willing to negotiate the on their percentage share—some lucky souls could come away with even bigger savings. Given that Buran has received an update since it was released into the wild and that the developers are willing to undercut their competition, it is safe to assume they are in for the long haul. Perhaps, they hope that by attracting affiliates at a lower price point, they can attract more than their competitors, thus earning similar or more amounts of illegally gotten cash than their rivals.
Another indicator that Buran’s developers are in for the long game is that the ransomware will not infect machines in certain regions. One possible reason is to prevent the attention of local law enforcement so they can operate for longer periods.
Given that there is no free decryptor available yet for Buran, some victims may feel obligated to pay. It is advised by law enforcement that no ransom should be paid when users or companies fall victim to such an attack. The costs associated with not paying could be far higher. At the risk of sounding like a broken record, prevention is better than the cure. Given that Buran depends on exploiting vulnerabilities to infect machines, updating software and moving away from legacy software such as Flash can greatly decrease the chance of being infected.