Babuk Locker: Mediocre, But Gets the Job Done
New Year’s ransomware news came early this year, when various media platforms began reporting the discovery of Babuk Locker, the newest ransomware variant to target corporations by encrypting files across network-connected devices and extorting ransom payments. For those hoping to see new ground broken in ransomware technology, Babuk Locker would have come as a disappointment. The code, its execution, the ways the operators communicate with victims and the threats to the stolen data have been labeled “unprofessional.” This does not mean that the malware is harmless; in fact, the opposite is true.
Discovery of Babuk Locker
Babuk Locker was discovered only a few days after most of the West celebrated the new year, but those behind the ransomware had already snatched up a few victims. Victims included an elevator and escalator company, an office furniture manufacturer, a car parts manufacturer, a medical testing products manufacturer and an air conditioning and heating company based in the U.S.
We can thank computer science student Chuong Dong for the analysis; Dong’s work is the best resource on Babuk Locker currently available to the InfoSec community. According to Dong’s analysis, while the ransomware is fairly standard in terms of what it does and how it does it, the operators have included several common tactics that made strains like Sodinokibi and Ryuk surge in terms of successful infections. Such tactics include the double extortion tactic, hyperthreading and the ability to encrypt files across a victim’s network. Let’s look at each in turn, and how Babuk Locker implements these tactics.
Double Extortion Ransomware
This has been, perhaps, the single most dominant trend in ransomware for the past year. Last year, at about the same time, the Maze ransomware gang (who have now opted for early retirement) began threatening to release stolen data before encryption of data was executed. The threats were soon followed by the gang releasing the data via a data leak site, accessible by other threat actors via a Tor browser. This became known as the ‘double extortion’ tactic, and has seen wide adoption by almost all the major ransomware gangs targeting large corporate and government networks.
The tactic became synonymous with gangs classified as human-operated ransomware gangs; the term describes ransomware operators who use manual tools to gain access to a network, and slowly increase their network privileges until they can manually execute the malware’s encryption protocols for the greatest effect on the target network. The double extortion tactic is an evolution of the human-operated trend. Recently, the tactic has evolved further to include gangs hiring call centers to cold-call victims and pressure them to pay the ransom.
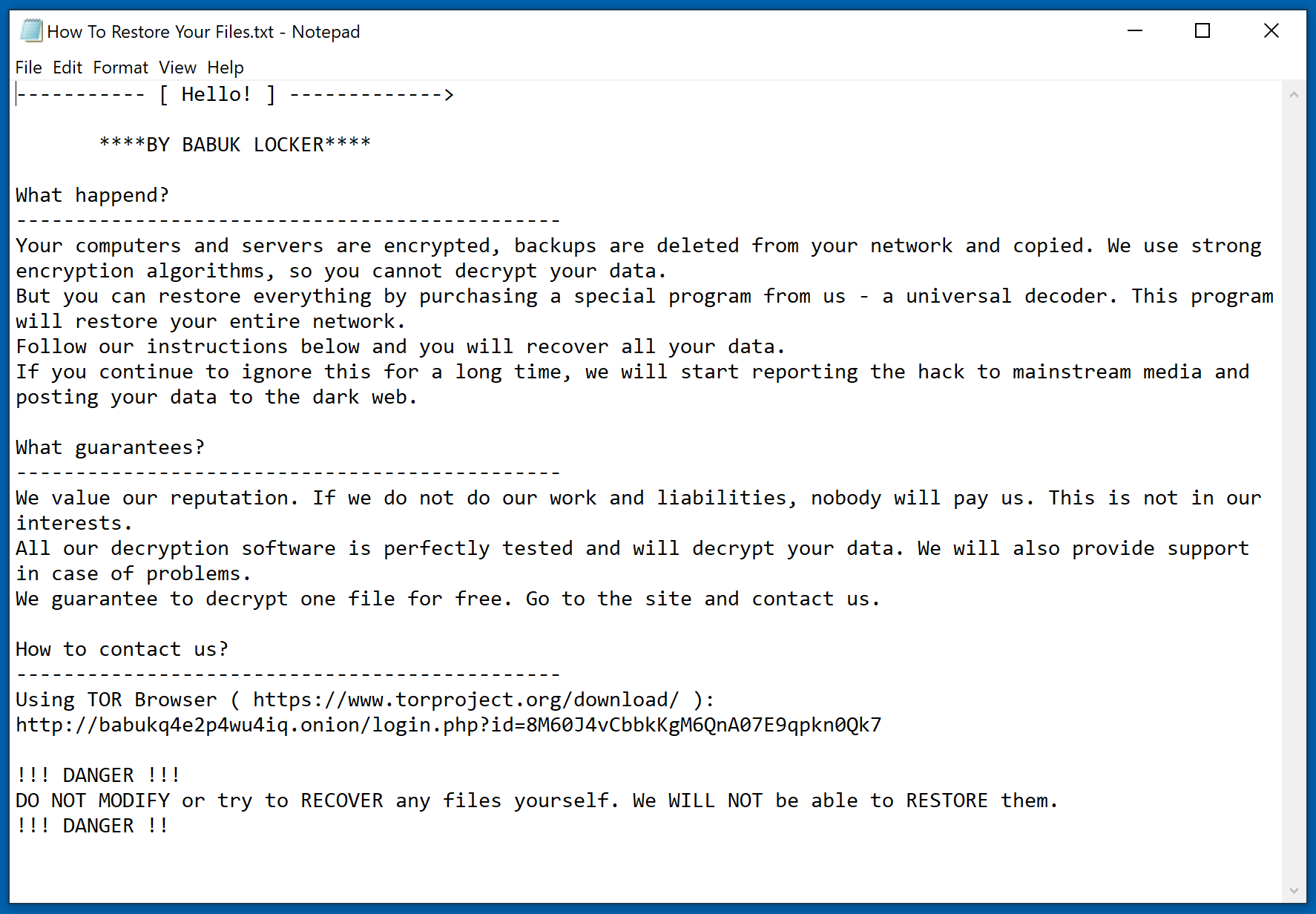
Based on current research, Babuk operators have not gone so far as to cold-call victims; however, they have threatened to release – and have released – data belonging to victims. Rather than releasing data via a dedicated leak site, the ransomware’s operators posted on underground hacker forums announcing, and then releasing, data of victims who refused to pay. Babuk does have a website, but this is used to communicate with victims and negotiate ransom payments. Here, one might view the operation as amateurish, in that all victims communicate via the same text channel so that everyone can see past communication between victims and the attacker.
Encryption across the Network
When ransomware was in its infancy, it tended to only encrypt files locally; that is to say, only files on the infected machine could be encrypted so that the user could not access them. In modern networks, files are shared across the network so that the business can operate. It was only a matter of time before hackers realized that these shared network resources could be encrypted, too, and could effectively halt daily operations. Large organizations like Travelex, according to reports, paid the Sodinokibi gang over $2 million USD when their network was struck in this fashion, and forced the company to suspend many of its services.
Babuk Locker ransom demand message:
Babuk is capable of targeting files across the network through the use of command-line instructions that allow the malware to search across the network for shared resources. The command can also encrypt only local files. If the attacker successfully compromises a network-connected machine with high enough administrative privileges, it can be safely assumed that the attacker will look to encrypt files across the network, as this will cause more damage. The malware uses a combination of SHA256 hashing, ChaCha8 encryption, and Elliptic-curve Diffie–Hellman (ECDH) key generation and exchange algorithm to protect its keys and encrypt files. This means that, barring a major mistake by the malware’s developers, the encryption is solid with no apparent way to decrypt files without the decryption key. This forces victims to either pay or restore from backups. The likelihood that a free decryptor will be released anytime soon is slim.
To further complicate recovering from Baduk Locker, the malware will do several things to help speed up and smooth the encryption process. But, first, before encryption begins, the malware looks for shadow copies and deletes them. Shadow copies are used to help create restore points if something critical happens to the machine so that important data isn’t lost; deleting these makes recovery harder for those impacted by a Baduk attack. The malware will also terminate services that prevent file manipulation or alterations, including services associated with security suites that may prevent the malware from doing what it is intended to do.
The list of services targeted includes: vss, sql, svc$, memtas, mepocs, sophos, veeam, backup, GxVss, GxBlr, GxFWD, GxCVD, GxCIMgr, DefWatch, ccEvtMgr, ccSetMgr, SavRoam, RTVscan, QBFCService, QBIDPService, Intuit.QuickBooks.FCS, QBCFMonitorService, YooBackup, YooIT, zhudongfangyu, sophos, stc_raw_agent, VSNAPVSS, VeeamTransportSvc, VeeamDeploymentService, VeeamNFSSvc, veeam, PDVFSService, BackupExecVSSProvider, BackupExecAgentAccelerator, BackupExecAgentBrowser, BackupExecDiveciMediaService, BackupExecJobEngine, BackupExecManagementService, BackupExecRPCService, AcrSch2Svc, AcronisAgent, CASAD2DWebSvc, CAARCUpdateSvc.
Files encrypted by Babuk Locker:
Lastly, if files are in use, they cannot be encrypted – not ideal for an attacker looking to encrypt as much as possible to guarantee that daily operations are stopped. To do this, Baduk Locker will terminate running processes that are used to run certain file types that businesses and government organizations rely on.
The processes terminated include: sql.exe, oracle.exe, ocssd.exe, dbsnmp.exe, synctime.exe, agntsvc.exe, isqlplussvc.exe, xfssvccon.exe, mydesktopservice.exe, ocautoupds.exe, encsvc.exe, firefox.exe, tbirdconfig.exe, mydesktopqos.exe, ocomm.exe, dbeng50.exe, sqbcoreservice.exe, excel.exe, infopath.exe, msaccess.exe, mspub.exe, onenote.exe, outlook.exe, powerpnt.exe, steam.exe, thebat.exe, thunderbird.exe, visio.exe, winword.exe, wordpad.exe, notepad.exe.
Hyperthreading
The act of encrypting files is a noisy affair, and when done en masse, it’s a key indication that something is wrong. Ransomware operators know this, and often choose to encrypt data when the business is quiet, slow or closed for the day. This is done in the hopes that no one is working; no one will notice and shut down the servers if something appears wrong. This information is gained by compromising the network days or weeks in advance of the attack and encryption process. This is one of the reasons why the final phase of the attack is usually done over weekends, and often in the early hours of the morning.
Other than relying on early hours best left for sleep, hackers have several tricks to make the encryption process go off smoothly. The speed at which files can be encrypted is an advantage, and to achieve this, hackers will abuse a machine’s hyperthreading capability. Modern CPUs have several cores stacked on top of one another to make processing faster. Each core acts like its own mini processor; the more you have the more tasks can be processed simultaneously. Hackers will use the CPU’s hyperthreading ability to encrypt files faster. In practice, hyperthreading, when abused by hackers, is done to process various types of data. That which is easily encrypted is done on one thread, while larger, more complex data is sent to another thread for encryption. This drastically improves encryption efficiency, and reduces the overall time taken.
Babuk takes advantage of hyperthreading by first evaluating the number of CPU cores on the victim’s machine. Then, it creates a data structure to handle the threads. Dong points out that this method has several flaws, stating,
“The first problem with this approach has to do with thread’s concurrency in an OS. A huge amount of threads can potentially be created for each process. However, in an ideal situation, it’s better to have one thread running per processor to avoid having threads competing with each other for the processor’s time and resource during encryption….However, that, by itself, is not that big of a problem if the author implemented a queue-like structure to process encrypting requests to utilize 100% of the victim’s processing power. Unfortunately, they decided to only spawn one encrypting thread per existing drive.”
As there’s likely to be more drives than threads created by the malware, Babuk cannot create as many threads as needed to speedily encrypt the targeted data. The malware then reverts to older, less efficient means of traversing through folders to encrypt data. If the malware can create the required number of threads to match the number of drives on the victim’s machine, the encryption will be a more efficient affair. Researchers will be quick to point out this flaw; however, for those already a victim of Babuk Locker, such discussions will be of little comfort.
Conclusion
Babuk Locker has already proved capable of creating corporate victims, and ransom demands have topped $80,000 USD. This amount is smaller than the take from some of the world’s most dangerous ransomware gangs, but it is not insignificant. While it can be successfully argued that the current version of Babuk Locker is not as efficient and well-coded as other ransomware examples, it still poses a clear danger to business and government networks.