Fortanix Adds Dashboard to Better Prioritize Remediation Efforts for PQC Era
Fortanix today added a tool to its portfolio that makes it simpler to identify instances of where encryption has been applied that are susceptible to being potentially broken whenever the post-quantum computing (PQC) era arrives.
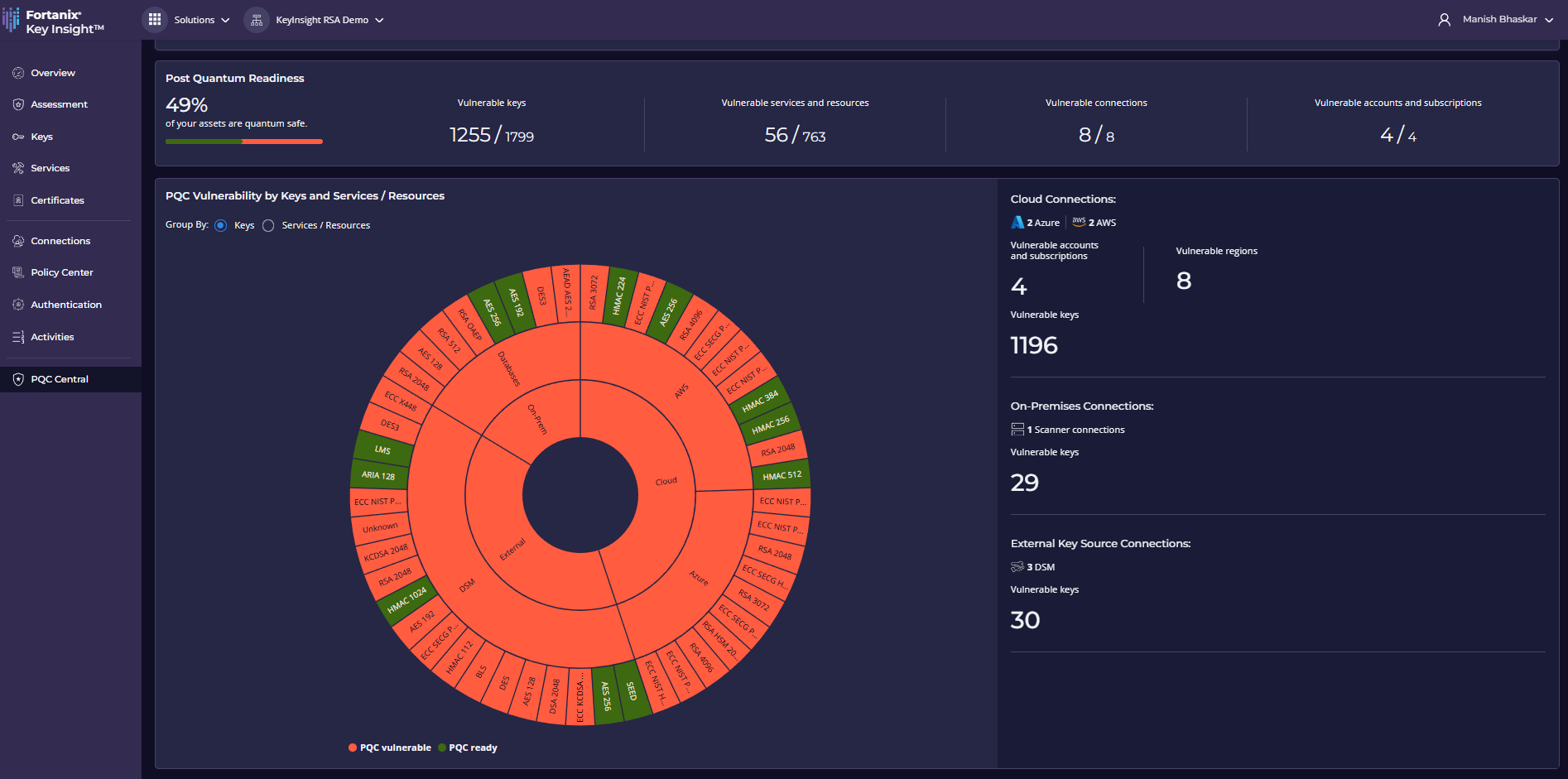
Anuj Jaiswal, chief product officer at Fortanix, said PQC Central adds a dashboard to Fortanix Key Insight, a capability that discovers instances of cryptography and potential risk levels that is a component of the core Fortanix Armor platform. Key Insight via that dashboard generates a prioritized list of PQC issues, including dependencies, that need to be addressed using Data Security Manager, the encryption and key management component of the Fortanix Armor platform.
The overall goal is to make it simpler for cybersecurity teams to prioritize encryption migration projects, based on the level of risk there is to an organization’s most critical applications, said Jaiswal.
No one knows for certain when quantum computing will advance to the point where it can be used to break legacy encryption schemes, but sometime before the end of this decade, it is expected that capability will be achieved. Many organizations by then may have replaced legacy applications and systems with offerings that rely on some type of post-quantum encryption, but there will still be plenty of applications that are likely to be still running five years from now. Fortanix is making a case for identifying those applications today with an eye toward steadily replacing vulnerable encryption schemes over the next several years.
At the core of the Fortanix portfolio is a platform that makes use of confidential computing to ensure keys are always encrypted, even while running in memory, when data is typically most vulnerable.
It’s not clear how rapidly organizations are replacing legacy encryption schemes, but just about any new applications will rely on one of several that the National Institute of Standards and Technology (NIST) has deemed to be quantum safe. The challenge is that replacing legacy encryption schemes today requires a significant amount of time and effort, which makes prioritizing which projects to focus on first essential, noted Jaiswal.
The rate at which that transition will be required also varies by country. The European Union, for example, expects member states to transition to post-quantum cryptography by the end of next year. The Trump administration in the U.S., however, has now changed course by eliminating a previous order issued by former President Biden that required Federal agencies to start using quantum-resistant encryption “as soon as practicable”, in addition to requiring vendors to use PQC when technologically possible. The Trump administration also eliminated instructions for the departments of State and Commerce to encourage key foreign allies and overseas industries to adopt post-quantum computing algorithms defined by the National Institute of Standards and Technology (NIST).
There is, of course, a lot of debate over which encryption schemes and protocols may need to be updated for the post-quantum era. Some argue that so long as the initial connection made by a digital certificate is post-quantum secure, the rest of the IT environment will remain secure. Regardless of how much effort is ultimately required, the time to determine what level of resources might actually be required is now.