NetRise Adds Tool to Analyze Application Binaries for Security Flaws
NetRise today at the 2025 RSA Conference unveiled a binary composition analysis (BCA) tool that makes it possible to identify application security weaknesses in applications that have already been deployed.
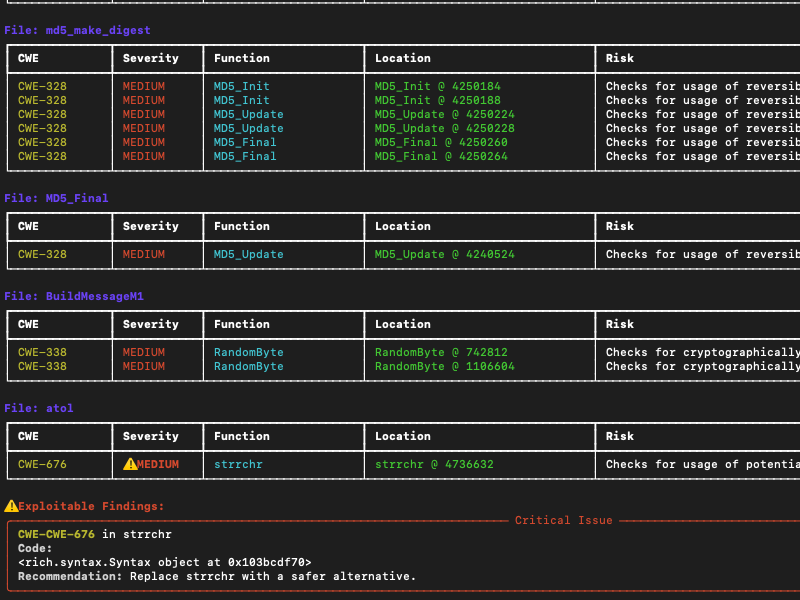
Company CEO Thomas Pace said that NetRise ZeoLens makes it possible to analyze code for vulnerabilities and structure weaknesses that were not previously discoverable after code had been compiled. That capability is critical because most cyberattacks against applications exploit known vulnerabilities and weaknesses in the binary code running in production environments, he added.
Additionally, NetRise ZeroLens takes advantage of generative artificial intelligence (AI) to summarize any issue discovered, which makes it simpler for cybersecurity teams to prioritize which issues need to be brought to the attention of application development teams, said Pace.
While significant progress has been made in terms of adopting best DevSecOps practices to reduce the number of vulnerabilities being introduced into source code in the first place, most of the attacks against applications are aimed at the binary code that is compiled just before an application is deployed. Discovering vulnerabilities in that code running in a production environment is primarily the responsibility of application security teams that are ultimately going to be held accountable for any breach that might occur.
The number of flawed binaries that might be running in production environments will, naturally, vary from one organization to another. However, given how many legacy applications there are, just about every application is vulnerable to an exploit that was overlooked during the application development process.
NetRise ZeroLens is specifically designed to enable red teams and ethical hackers to upload and analyze thousands of binaries concurrently, a process that previously required too much manual effort for those teams to analyze all the binary code running in production environments, said Pace.
In the wake of a series of recent application security breaches, there is, fortunately, more attention being paid to discovering and remediating vulnerabilities. The existing processes used to discover those vulnerabilities, however, tend to create a lot of friction between cybersecurity and application development teams. Many of the vulnerabilities being identified lack the appropriate level of context. For example, it may turn out that the code that is deemed vulnerable isn’t actually exploitable because it was never actually loaded into memory. Scanning binaries will make it easier for cybersecurity teams to identify issues that require the immediate attention of the application development team that built the application in the first place.
Hopefully, there will come a day soon when application security improves simply because more code is being reviewed and remediated before it is deployed. In the meantime, however, AI tools are exponentially increasing the amount of code being generated by application developers. Unfortunately, many of those tools were trained using examples of flawed code running in production environments, which means a lot of that code that ultimately gets compiled into a binary is likely to have a security issue. In effect, the number of application security issues that might arise in the months and years ahead might suddenly increase. As a result, the need to find ways to automate the discovery of security issues in binaries is about to become a whole lot more pressing than most cybersecurity professionals may yet fully appreciate.