Debating SIEM in 2023, Part 1
Hey, it is 2023, let’s debate SIEM again!
Debate SIEM? In 2023?
This is so 1997! Or perhaps 2017. Anyhow, Security Information and Event Management (SIEM) is a growing $4+B market that is proving remarkably resilient, and, actually, interesting again.
Let’s start with an obligatory AI response:
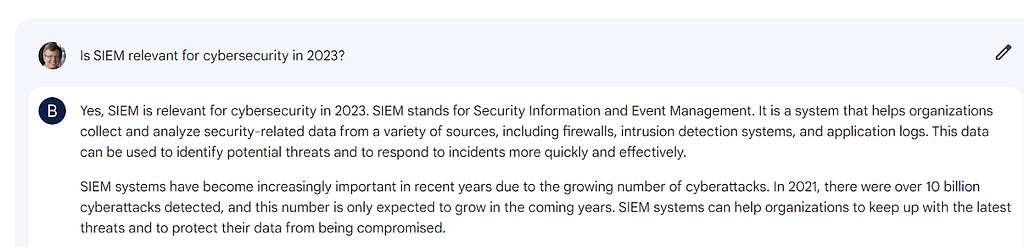
Let’s proceed with a just-as-obligatory Gartner quote: “The SIEM market is maturing at a rapid pace and continues to be extremely competitive. The reality of what SIEM was just five years ago is starting to detach from what SIEM is and provides today.” (Obligatory Gartner quote from 2022 SIEM MQ)
Finally, let’s move to an obligatory Anton Twitter poll 🙂
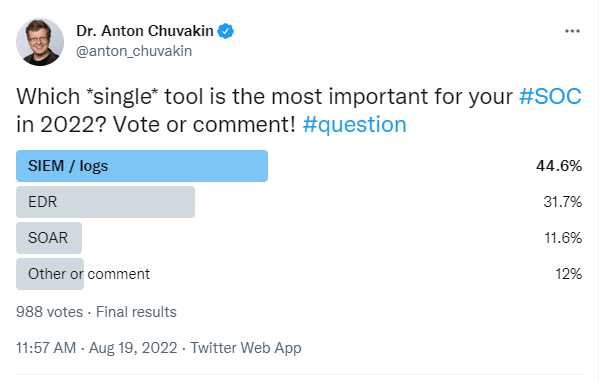
So, our mini-conclusion at this stage is that yes, SIEM is relevant for 2023.
Let’s see if anything threatens its relevance in the coming years. Question game time!
Q: Can XDR kill SIEM?
A: Can a dragon eat a duck? Well, sure, if dragons existed. Otherwise, no, sorry. So, can XDR kill SIEM? Well, it needs to exist as a consensus reality among the “market makers” and customers (security leaders and professionals) first. Otherwise, see “Your XDR? ‘Yeah, well, that’s just, like, your opinion, man.’”
Q: Can Security Data Lakes kill SIEM?
A: Can a transmission take over the car market? Eh, no, because it is a car part. You need the rest of the car to drive. The way I observe today’s market reality, there are two camps here.
One camp shows a general data lake lacking (or should I say “laking”?) any security features, content and knowledge (transmission, not a car), while the other camp builds a SIEM and then keeps insisting (to their own detriment of being excluded from SIEM evaluations … hilarity ensues!) that their SIEM is not a SIEM but a “security data lake.” Today’s SIEMs incorporate a modern data stack, and may resemble a data lake in many aspects, but the “SDL kills SIEM” argument is IMHO silly. Here is another great example.
Q: I’ve heard some organizations do D&R just fine without a SIEM?
A: Sure, of course, you can go “SIEM-less”! Some organizations built incredibly sophisticated log analysis platforms for security that they don’t call “SIEM.” Now imagine that these DIY tools appear on the open market. Guess what market that would be? Exactly, SIEM! So, not calling your SIEM a SIEM won’t make it not a SIEM, and the market will correct you if you try anyway. Or, you sink in your own data lake…
Some organizations run EDR-centric SOCs where a commercial SIEM tool is not present, while log analysis is less relevant (compared to endpoint activity analysis), but ultimately they do look at logs (or should, because EDR alone has obvious gaps).
Apart from that, there are many scenarios where “not buying a commercial SIEM” is the right choice (for example, many MSSP/MDR examples have you paying for SIEM value, rather than owning a SIEM product). In another case, if your entire IT stack is SaaS, you can perhaps end up with a “CASB as SIEM” scenario (rare, but plausible).
However, I don’t see a way to go without any security log analysis capability.
Q: What about the cloud, can the cloud kill SIEM?
A: Well, there are corner cases where this is the case, but in many cases cloud boosts, rather than kills a SIEM. My serious answer, however, is: organizations moving to cloud will change the SIEM space, will make SIEM less relevant for some clients (SMB in a single cloud, SaaS-heavy organizations), but more relevant for others (analyze logs across clouds, etc)
Q: So can SIEM really die?
A: In my “humble” opinion, the SIEM name may die, but the need to analyze logs for security cannot really die in the foreseeable future. Now, if you want to see a funny take on this, go here.
Q: OK, fine, SIEM cannot die, but can it be relegated to the “boring compliance technology box” while some new exciting tools deliver the security insights from various telemetry?
A: Sure, in theory, but this is not happening today. SIEM is a security capability that is also useful for some regulatory and framework compliance (PCI DSS, HIPAA, NIST CSF, etc).
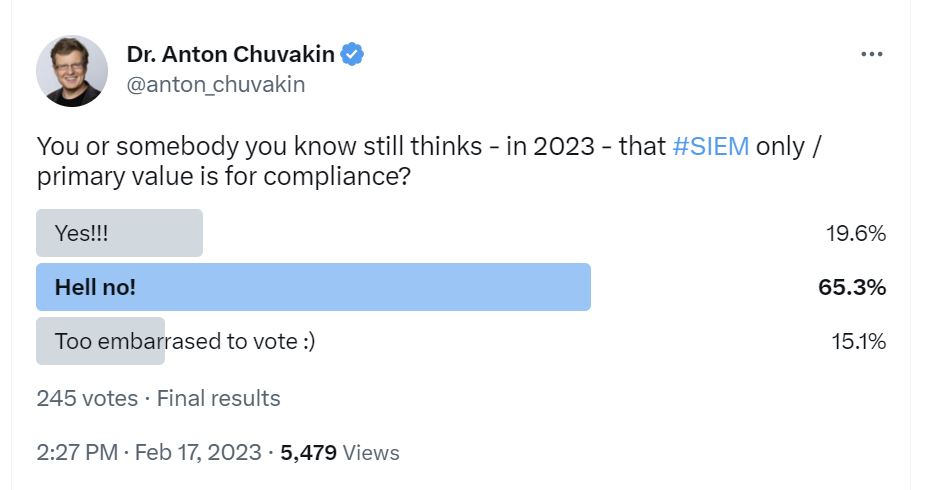
Where do we go from here? I think that…
- SIEM — a security-focused telemetry analysis capability — matters and will still matter in 3–7 years (and, I have no idea if it will still be called “SIEM”)
- SIEM is hugely better as a cloud-based (cloud-native, really) tool
- SIEM will take more lessons from EDR to be more immediately useful for security
Next up, in Part 2, we will have a 2023 SIEM use case discussion! Fun!
Resources:
- “Security Correlation Then and Now: A Sad Truth About SIEM”
- “20 Years of SIEM: Celebrating My Dubious Anniversary”
- “Today, You Really Want a SaaS SIEM!”
- “Left of SIEM? Right of SIEM? Get It Right!”
Debating SIEM in 2023, Part 1 was originally published in Anton on Security on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from Stories by Anton Chuvakin on Medium authored by Anton Chuvakin. Read the original post at: https://medium.com/anton-on-security/debating-siem-in-2023-part-1-992bfe095334?source=rss-11065c9e943e------2





