New OWASP Top 10 for 2021-Whats New?
Read Time 3 minutes
Introduction
The 2021 edition of OWASP 2021 is finally out! It is time to analyze how these changes can impact your security initiatives.

While the original OWASP Top 10 focused on vulnerability classification, the new list is more data driven and focuses on exploitability and impact. There is also a mapping done to the Common Vulnerability Enumeration (CVE) standard. CVE is a list of records — each containing an identification number, a description, and at least one public reference for publicly known cybersecurity vulnerabilities. This list is maintained by Mitre Corporation.
OWASP TOP 10 2021 List
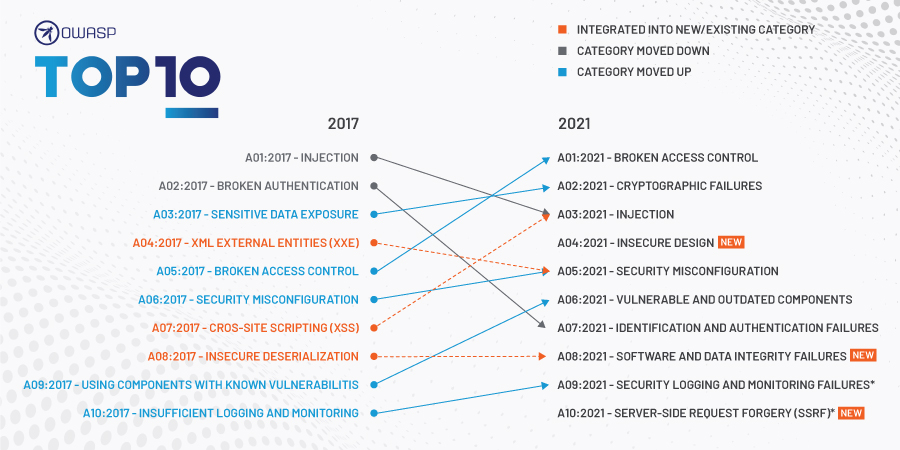
A01-2021-Broken Access Control Jumps to the Top of the List
Broken access control means that a malicious user can access a function that should not be accessible to them. Elevation of privilege attacks and bypassing access control checks are good examples.
It should come as no surprise that Broken Access Control has made it to the top of the list as the new list focusses on exploitability & impact. Broken Access Control is also a common problem with APIs which have proliferated modern applications. While not as common as some of the other vulnerabilities, when found, malicious users can quickly exploit this vulnerability with disastrous consequences.
Best preventive measure against Broken Access Control is do regular pen testing in addition to automatic scans as business logic failures are hard to detect with SAST tools used in the development pipeline.
Summary of Changes
There are three new categories in the OWASP 2021 List. These include:
A04:2021-Insecure Design
Insecure Design is a completely new strategic vulnerability category. It covers all the vulnerabilities that surface due to the designers of the software not taking security into account. Traditionally, many of the security testing was done later in the development cycle leading to expensive remediation work. As enterprises make the shift to a DevOps environment, it becomes imperative to shift security left & build software with a Secure by Design mindset.
Some best practices to address this vulnerability include doing Threat Modelling using techniques like STRIDE, using Secure Design Patterns to eliminate accidental insertion of vulnerabilities into code & leveraging Reference Architectures during the design phase.
A08:2021-Software & Data Integrity Failures
The second new category in the 2021 OWASP Top 10 is also a very generic one and focuses on testing the integrity of software and data in the software development lifecycle. An example of this is where an application relies upon plugins, libraries, or modules from untrusted sources, repositories, and content delivery networks (CDNs).
Many applications now include auto-update functionality, where updates are downloaded without sufficient integrity verification and applied to the previously trusted application. Attackers could potentially upload their own updates to be distributed and run on all installations. The recent SolarWinds hack that impacted over 18,000 Government customers has heightened the risks of this class of vulnerability.
Some industry best practices to minimize the risks include:
- Use digital signatures or similar mechanisms to verify the software or data is from the expected source and has not been altered.
- Ensure libraries and dependencies, such as NPM or Maven, are consuming trusted repositories
- Ensure that your CI/CD pipeline has proper segregation, configuration, and access control to ensure the integrity of the code flowing through the build and deploy processes.
A10:2021 -Server-Side Request Forgery (SSRF)
This third category was added based on industry surveys. SSRF is a web security vulnerability that allows an attacker to induce the server-side application to make HTTP requests to an arbitrary domain of the attacker’s choosing. A successful SSRF attack can often result in unauthorized actions or access to sensitive data within the organization. The recent Capital One attack highlighted the dangers of this kind of vulnerability.
SSRF risks can be mitigated through network segmentation, disabling HTTP redirection, sanitizing user input, and using a whitelist of allowed domains and protocols from where the web server can fetch remote resources.
Categories With Name Changes
Four categories changed names. These include:
- A02:2021-Cryptographic Failures (was Sensitive Data Exposure)
- A06: 2021- Vulnerable & Outdated Components (was Using Components with Known Vulnerabilities)
- A09:2021-Server Monitoring & Logging Failures (was Insufficient Monitoring & Logging)
Categories That Remained Unchanged
These categories remain unchanged although some new scope was added:
- A01:2021-Broken Access Control
- A03:2021-Injection Errors (now includes XSS)
- A05:2021 Security Misconfigurations (now includes XML External Entity (XXE))
How Should You Respond to the OWASP 2021 List?
Left shifting of security has moved developers to the front lines of Application Security. Developer centric training can help you build a common baseline knowledge of security skills. As an AppSec manager responsible for application security, immediately refresh your existing OWASP 10 training to align with the new OWASP 2021 list.
OWASP TOP 10 is risk focused. Consider complementing it with OWASP ASVS security framework and OWASP Proactive Controls which are more remediation focused and can also help with also ensuring you have necessary controls from an audit perspective.
Looking for Developer Centric AppSec training to stay on top of the OWASP Top 10-2021 vulnerabilities for PCI or HIPAA Compliance? Check out our interactive platform here
The post New OWASP Top 10 for 2021-Whats New? appeared first on Secure Coding & Cybersecurity Training.
*** This is a Security Bloggers Network syndicated blog from Blog – Secure Coding & Cybersecurity Training authored by Harish Bhat. Read the original post at: https://www.cyberlabs360.com/blog/new-owasp-top-10-for-2021-whats-new/



