Fuzz in Your Language, Fuzzer, or Architecture!
Fuzz in Your Language, Fuzzer, or Architecture!
·
At ForAllSecure, we’re all about fuzzing and making it easier for customers to quickly fuzz and secure their applications. That’s why we’ve gone ahead and compiled a catalog of fuzz targets intended for Mayhem that’s written and compiled using several different languages (and architectures) like C/C++, Python, Go, Rust, Java and many others! We’ve also added several choices for specifying which fuzzer engine to use, whether that’s the popular libFuzzer, honggfuzz, AFL, or even our own Mayhem for Code fuzzer.
In essence, we’ve provided a swiss army knife of fuzzing options to not only serve as a quick-and-easy reference point for users to get started with fuzzing in general, but to also showcase Mayhem’s versatility for fuzzing several languages and architectures in tandem with specific fuzzer engines. This catalog of tutorial fuzzing targets also emphasizes the recommended workflow for compiling targets using Docker and fuzzing such containerized applications in Mayhem.
With introductions out of the way, let’s now take a look at the fuzzme repository hosted on GitHub!
How Are Targets Organized in the Fuzzme Repository?
When you first navigate to the fuzzme repo, you’ll be greeted by a README.md displaying a nicely formatted table with links organizing the tutorial fuzz targets by Language, Environment, Fuzzer, Image Size, and a Docker Hub link to the respective Docker image for the target application.
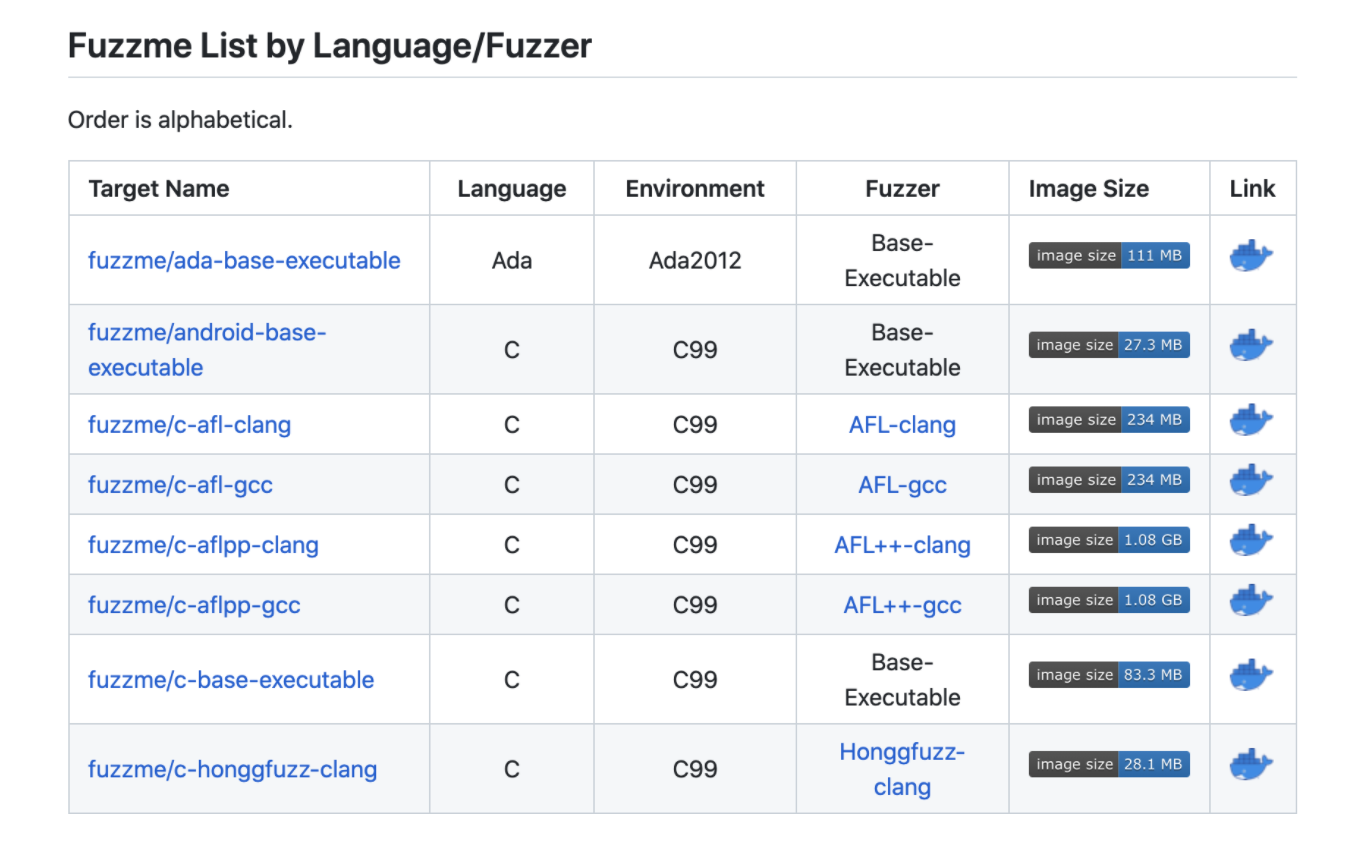
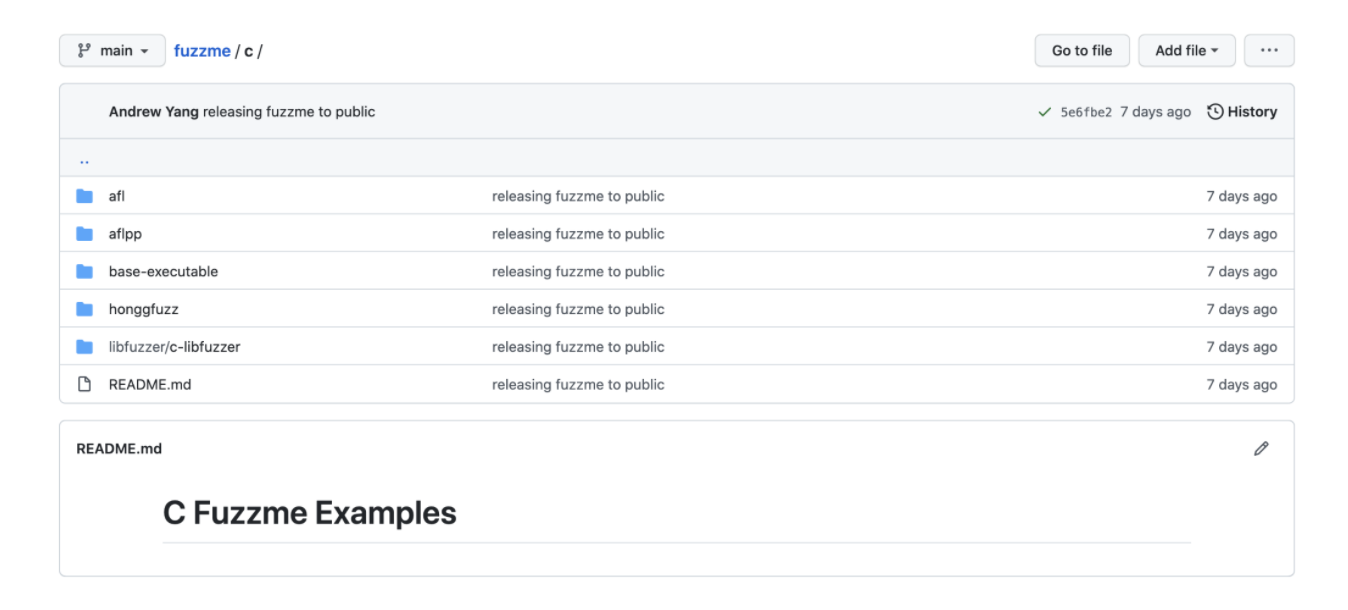
More specifically, each target is organized by language-specific folders, with multiple sub-folders indicating the fuzzer engine and compiler used, such as gcc or clang. For example, if we look at the folder containing C language targets, we can see the multiple sub-folders underneath.
Walking Through a Fuzzme Target Application
Let’s now pick a fuzzme target to try out! Navigate to the c-base-executable target and take a look at the following items.
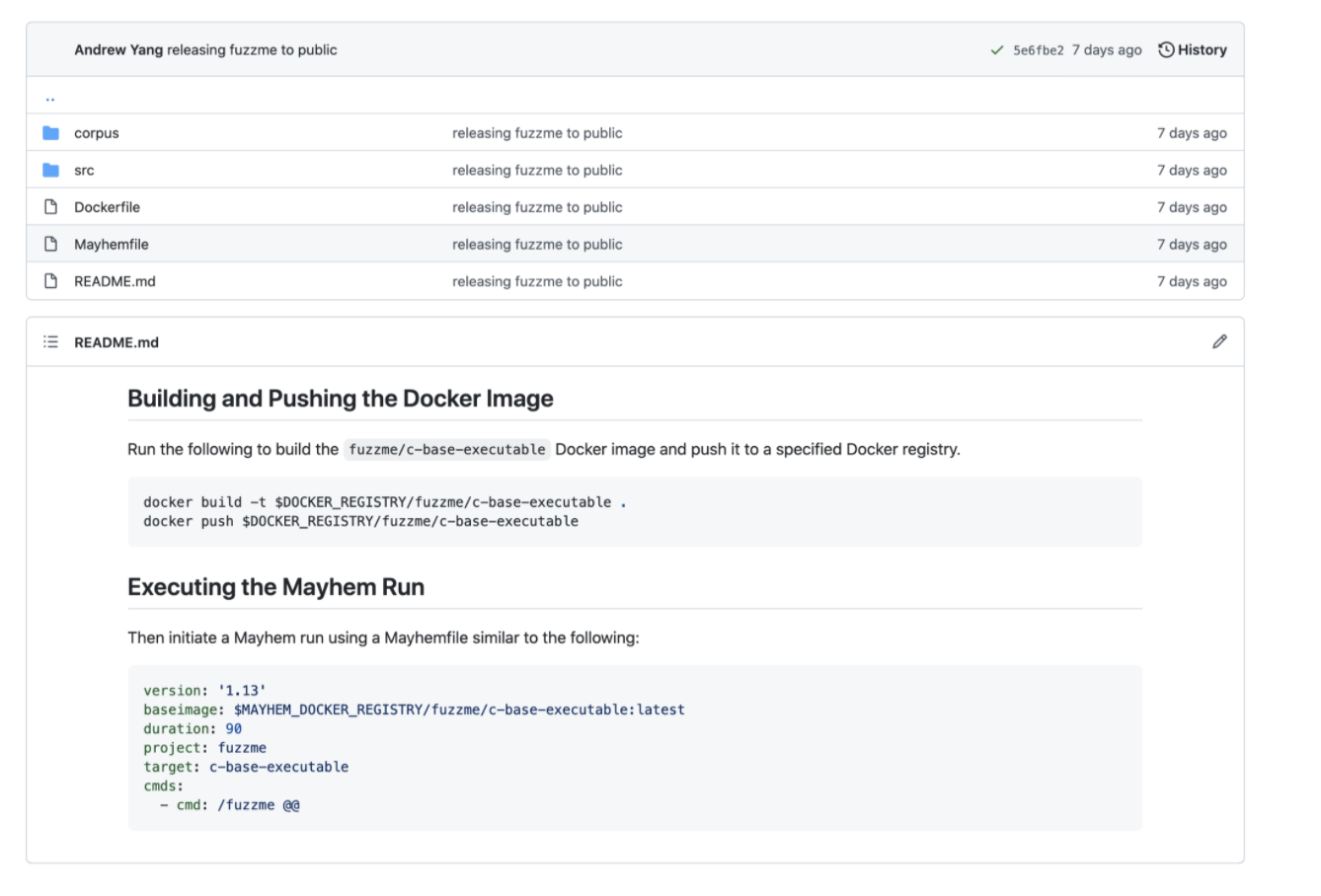
For each target folder we’ve included the following array of items: a seed test corpus folder, a src folder containing source code for the target application, a Dockerfile for compiling the containerized application, and a Mayhemfile for fuzzing the Docker image containing the target application (once it has been uploaded to a Mayhem Docker Registry).
For this example, let’s first take a look at the source code, fuzzme.c:
#include <stdio.h>
#include <string.h>
int fuzzme(char *buf)
{
if(strlen(buf) >= 3)
if(buf[0] == 'b')
if(buf[1] == 'u')
if(buf[2] == 'g') {
printf("You've got it!");
return 1/0; // Defect: divide-by-zero.
}
return 0;
}
int main(int argc, char *argv[])
{
FILE *f;
char buf[12];
if(argc != 2){
fprintf(stderr, "Must supply a text filen");
return -1;
}
f = fopen(argv[1], "r");
if(f == NULL){
fprintf(stderr, "Could not open %sn", argv[1]);
return -1;
}
if(fgets(buf, sizeof(buf), f) == NULL){
fprintf(stderr, "Could not read from %sn", argv[1]);
return -1;
}
fuzzme(buf);
return 0;
}
Here we see on line 11 that a divide-by-zero error will be introduced once the test case “bug” is input to the C fuzzme target. If we now look at the corresponding Dockerfile, we can see the compilation steps for producing the containerized C fuzzme binary.
FROM debian:buster-slim as builder
RUN apt-get update &&
apt-get install -y gcc make libc6-dbg &&
rm -rf /var/lib/apt/lists/*
COPY src/fuzzme.c .
RUN gcc fuzzme.c -o /fuzzme
# Set to fuzz!
ENTRYPOINT []
CMD /fuzzme @@
Therefore, as the README for the fuzzme/c-base-executable target suggests, we just need to execute the following commands within the directory:
docker build -t $DOCKER_REGISTRY/fuzzme/c-base-executable .
docker push $DOCKER_REGISTRY/fuzzme/c-base-executable
Note: You will need to set the DOCKER_REGISTRY environment variable to that of your Mayhem Docker Registry. For example, tutorial.forallsecure.com:5000. And once the Docker image has been successfully uploaded, just simply execute the Mayhem run using the included Mayhemfile:
version: '1.13'
baseimage: $MAYHEM_DOCKER_REGISTRY/fuzzme/c-base-executable:latest
duration: 90
project: fuzzme
target: c-base-executable
cmds:
- cmd: /fuzzme @@
You can simply execute a mayhem run command in the current directory if you have the Mayhem CLI installed, or execute a Mayhem run by using the web-based Mayhem UI and manually inputting the above Mayhemfile configuration.
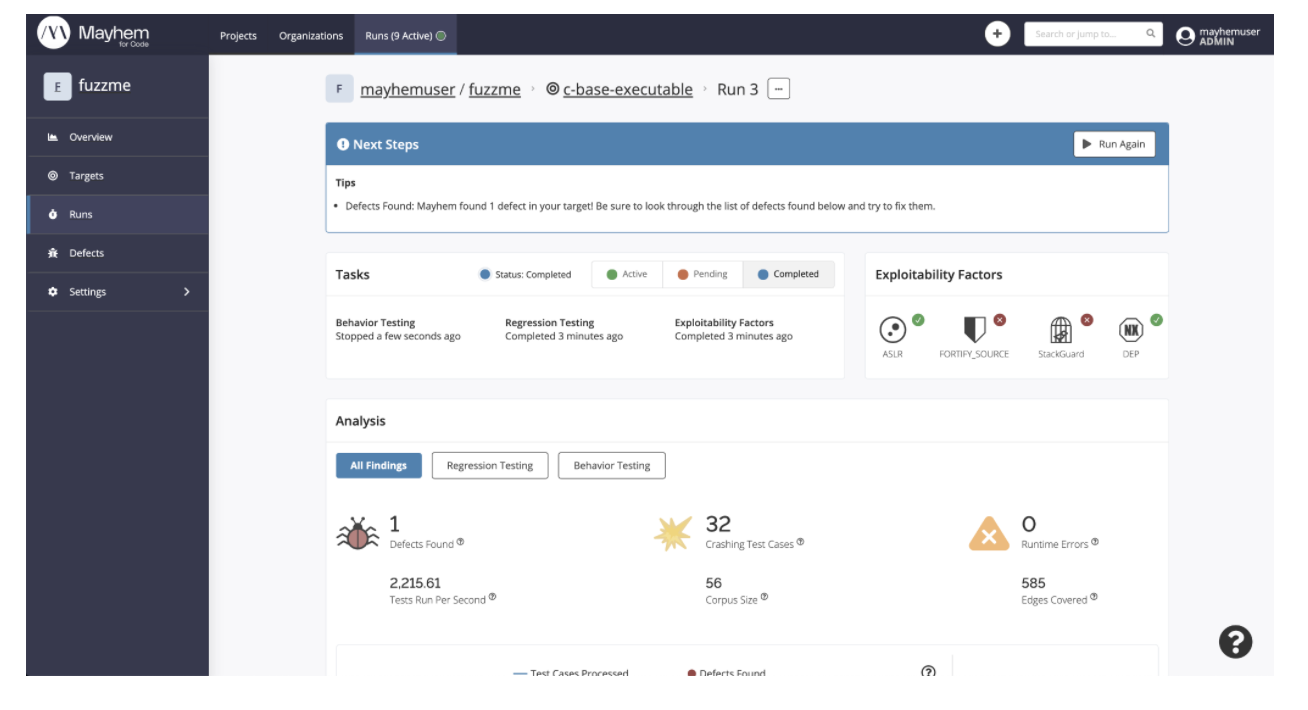
And that’s it! You should see something similar to the following in the Mayhem UI for your Mayhem deployment. Nice job, you just fuzzed a C binary and found a defect!
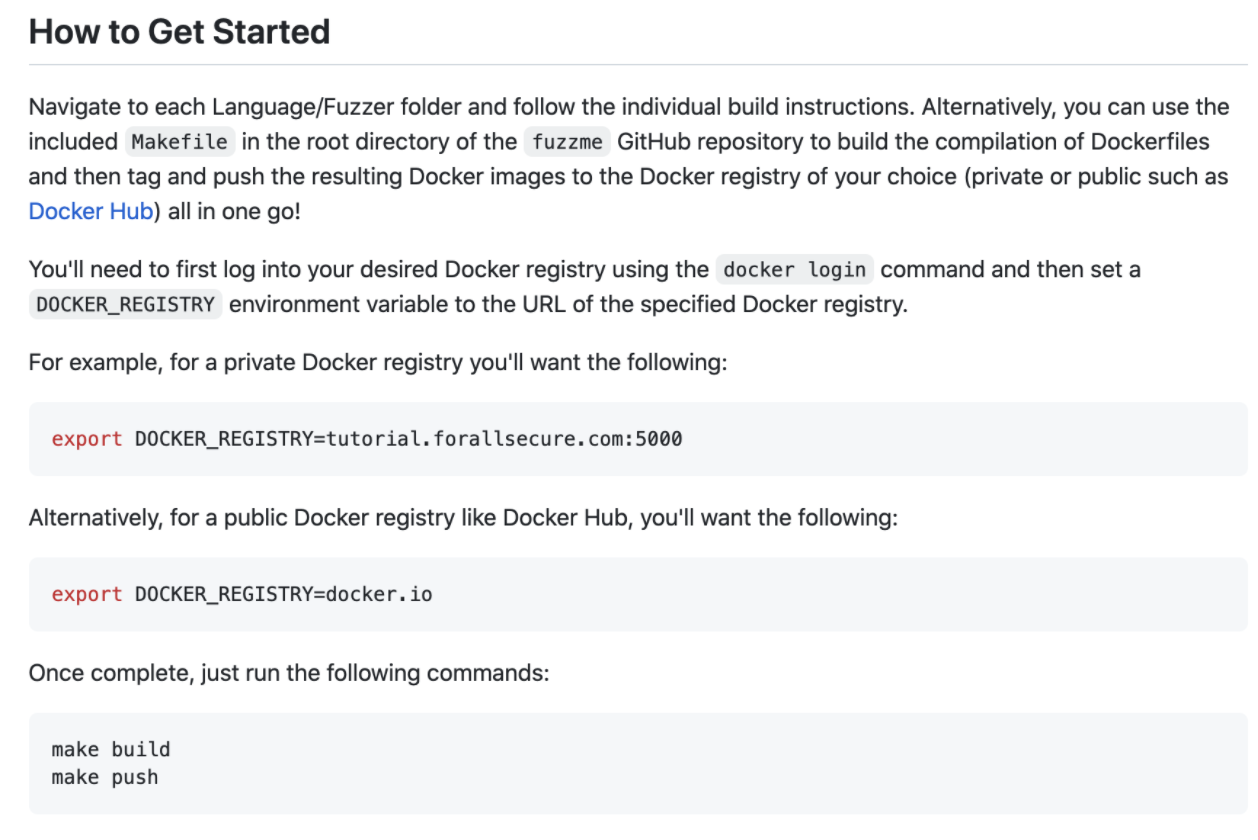
Looking to try some other fuzzme targets out? In this case, compiling each target and pushing the respective Docker image to a Mayhem Docker Registry may become too time consuming. Therefore, use the included Makefile at the root of the fuzzme repository to compile and push all fuzzme targets in one go!
Language Guides for the Fuzzme Targets
Need a true step-by-step walkthrough? If you have access to a Mayhem instance, check out the language guides in the Mayhem documentation for a detailed explanation on several of the fuzzme targets written in C/C++, Go, Rust, Java, and Python!
The language guides will be similar to the walkthrough shown here; however, we’ll have the opportunity to dive deeper and explain each line of code involved in designing the target application and compiling the binary using Docker, as well as show you how to create your very own fuzzme targets!
And finally, we’re always looking to improve! If you have any other questions, issues, or requests for more information, feel free to message us on slack or email us at [email protected]!
Stay Connected
Subscribe to Updates
By submitting this form, you agree to our
Terms of Use
and acknowledge our
Privacy Statement.
*** This is a Security Bloggers Network syndicated blog from Latest blog posts authored by Andrew Yang. Read the original post at: https://forallsecure.com/blog/fuzz-in-your-language-fuzzer-or-architecture