2020 Ends With A Bang
December 2020 was an eventful month in cyber security. This blog recaps three of the major security events we saw towards the end of last year.
December began with FireEye’s breach announcement that included a leak of its red team tools arsenal. Quickly after this announcement, Imperva Threat Research group made sure that all of our WAF customers were being protected from malicious usage of these tools. As we thought we would, we soon saw a rise in attacks against Imperva customers based on these tools and vulnerabilities – all of which were detected and blocked.
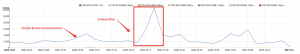
Following FireEye’s announcement, we soon learned about the SolarWinds breach and the huge impact of this new supply chain attack. Once again, we added security controls against two attack vectors – SUPERNOVA .NET webshell access and SolarWinds Orion API authentication bypass. Both vectors grant attackers the capability to remotely execute commands on victims’ machines, which is bad. Very bad. Right now we’re seeing massive scanning attempts across Imperva’s customers, trying to find systems with vulnerable SolarWinds to exploit.
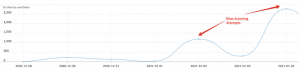
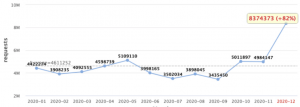
Oh, and not to forget we also had Christmas, always a time when attackers try to spam you and your loved ones, usually in an attempt to buy forged goods in special sales or participate in shady lotteries. During December, we saw a huge rise in spam attacks against Imperva customers, specifically in the United States where spam messages grew by 82%. All of these were detected and blocked.
Now that 2020 is behind us we’re hoping for a more calm and secure 2021 
The post 2020 Ends With A Bang appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Nadav Avital. Read the original post at: https://www.imperva.com/blog/2020-ends-with-a-bang/



