Major Global Ransom Denial of Service Campaign Continues Rising Trend in Global DDoS Attacks
Extortionists Claim Connection to Fancy Bear and Lazarus Group
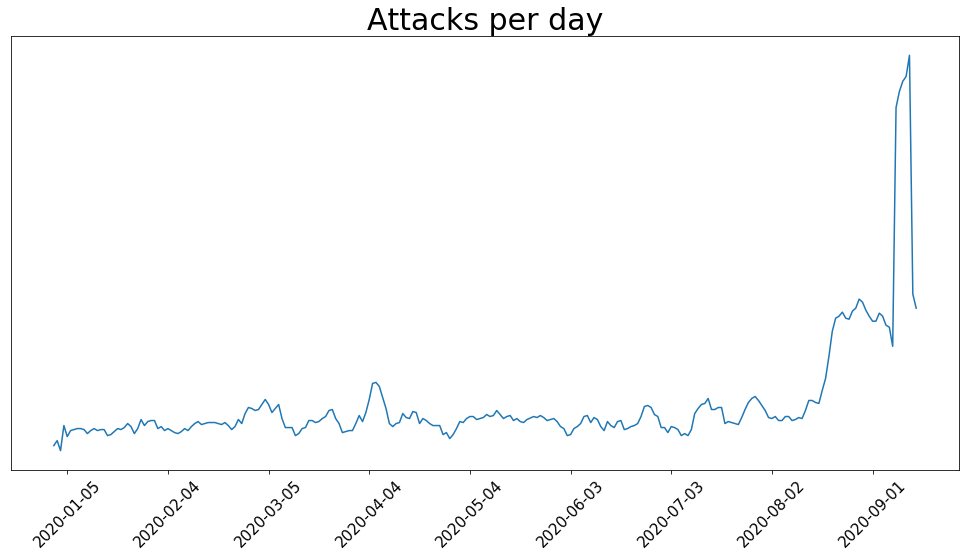
In the past weeks the number of serious Ransom Denial of Service (RDoS) threats has ramped-up considerably, with extortion campaigns targeting thousands of large commercial organizations including financial services. Coming from extortionists leveraging the names of well-known threat actor groups such as ‘Fancy Bear’ and ‘the Lazarus Group’, and consisting of ransom demands for a bitcoin payment to prevent a distributed denial of service (DDoS) attack on their target’s network, the threats have raised sufficient concern for the FBI to issue a formal alert warning organizations to be aware of this type of malicious attack and to adopt DDoS protection solutions to guard against them.
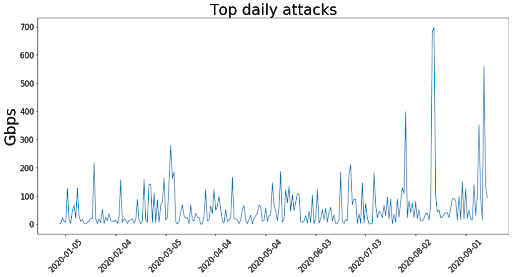
RDoS campaigns are extortion-based DDoS threats motivated by financial gain. According to the FBI, the recent spate of threats against the financial services industry threatened to conduct a ‘2 terabit per second (Tbps) DDoS attack unless the institution paid a ransom of 20 bitcoin, worth approximately USD $228K’. The threats normally also contain a statement that the threat actors will issue a small DDoS attack immediately to demonstrate their capabilities.
Imperva has observed RDoS activity carried out by threat actors claiming to be the ‘Lazarus Group’ and threatening to launch a DDoS attack against the customer’s entire network if a ransom pay-out is not paid within six days. Once the attack has started, a payment of 30 bitcoin (approx USD $328K) will stop it, with an additional 10 bitcoin (USD $110K) demanded for each day the ransom remains unpaid. Similar to the attacks outlined in the FBI alert, the attackers threatened to begin a small attack on the company’s main IP address immediately to prove the threat is not a hoax.
According to the FBI alert, the DDoS “demonstration activity” varied, with some targeting a single IP address and others targeting multiple IPs. And, while most institutions didn’t report additional activity after the six-day mark, some did report follow-up activity.
DDoS attacks don’t always come with a ransom demand but, given that even one hour of downtime can cost organizations up to $100K in some cases, this type of RDoS attack is worth taking seriously and mitigating against.
Should you pay?
Paying might not be the solution. Known cyber threat groups that engage in RDoS campaigns usually don’t announce their intention to attack, so if you receive an extortion email prior to an attack there’s a good chance it’s a scam, or that the attackers aren’t who they claim to be and don’t possess major DDoS capabilities.
In fact, paying doesn’t necessarily guarantee an end to the problem. The extortionists might add you to a list of companies who pay out and just keep on threatening you and demanding even more money. They might even attack you even if you’ve paid.
Alternatively, a DDoS for hire/hacktivist group might want to attack your network but will try to get some extra cash by sending a ransom note. They’ll attack anyway, simply because it’s their agenda or because they’ve been paid to.
Despite the scammers launching sample DDoS attacks following their initial threat, the FBI alert outlined that analysts are confident that they lack the bandwidth or capability for larger, more destructive attacks. and that any follow-on threat can be curtailed through third-party DDoS mitigation services. However even seconds of downtime can hurt a business, and a longer period can be devastating and this is why time-to-mitigation (TTM) is vital.
How Imperva Can Help
Imperva offers an emergency DDoS mitigation solution to protect you against any secondary attacks. The Imperva Infrastructure Protection service is easily deployed as either always-on or on-demand and a Solution Manager will guide you through the onboarding process to protect your entire network infrastructure against further DDoS attacks.
Start your onboarding process today by visiting Network DDoS Protection Onboarding.
A closer look at the attacks
By Johnathan Azaria – Imperva Threat Research
Imperva’s analysis of the sample DDoS attacks launched by the threat actors shows that the common, low-effort ransom DDoS attacks use amplification vectors such as DNS response, SSDP, NTP, Memcache etc. These vectors allow the attacker to use only a small number of attacking bots in order to generate a massive bandwidth attack. In other words, it’s a cheap, effective, low-effort way to channel a major attack, and not a small attack that ‘will not cause any damage’, as claimed in the scammer’s original message. These vectors work by exploiting vulnerable servers that can be manipulated into sending massive amounts of traffic to a target of the attacker’s choice.
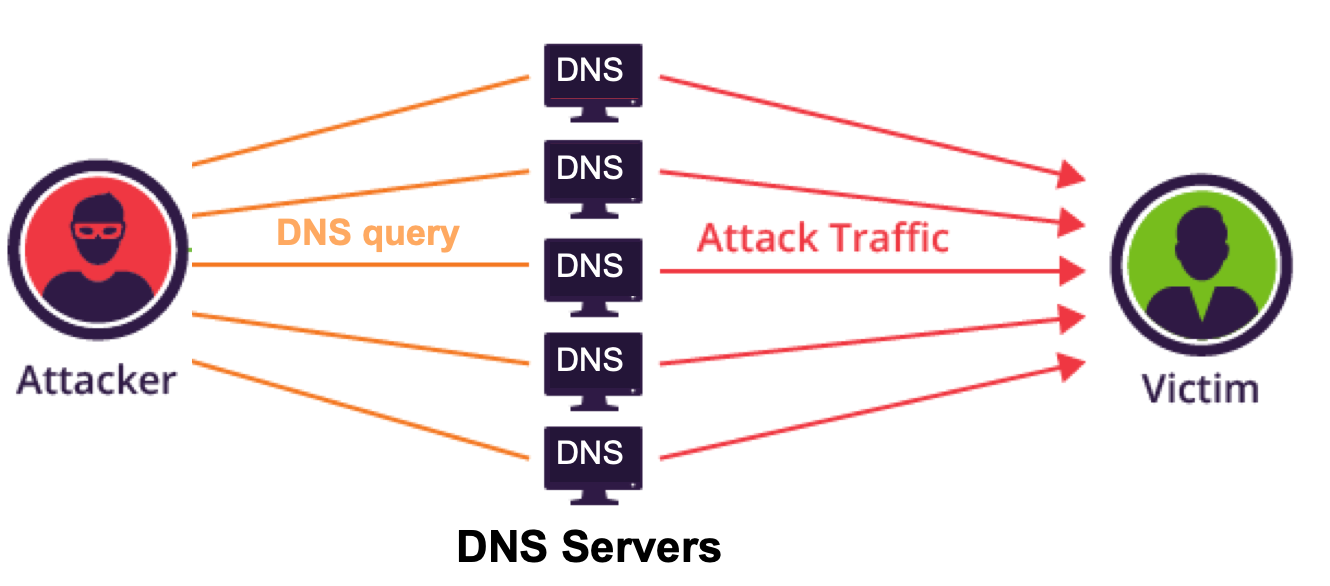
The flow of these attacks is quite simple. In this example, we’ll refer to DNS servers, i.e. a DNS amplification attack. Many DNS servers allow users to request all records of a certain site, a request known as an ANY request. The request itself is pretty small but the response from the DNS server is quite big because it contains many records – the ratio between the request size and the response size is the amplification factor. Attackers exploit this feature by sending many DNS ANY requests to DNS servers while pretending to be the victim. This causes the DNS server to send the response to the victim server, unaware it’s flooding it with massive amounts of traffic and effectively DDoSing it.
These vectors, as deadly as they might sound, are simple to detect and easily mitigated by cloud DDoS protection solutions. Because these attacks can peak quickly and reach devastating amounts of traffic, the most important factor is the time to mitigate – the amount of time it takes the protection service to start mitigating traffic.
Most of the RDoS attacks we mitigated in the last few weeks used amplification vectors. However, in some cases, the attackers took the time to do their homework.
In one massive attack we mitigated, the attackers partially studied the attacked network and sent in tailored HTTPs requests that were somewhat similar to the normal traffic.
To onboard visit Network DDoS Protection Onboarding.
Learn more about Imperva DDoS Protection Solutions here.
The post Major Global Ransom Denial of Service Campaign Continues Rising Trend in Global DDoS Attacks appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Grainne McKeever. Read the original post at: https://www.imperva.com/blog/major-global-ransom-denial-of-service-campaign-continues-rising-trend-in-global-ddos-attacks/