Home » Security Bloggers Network » Risk Register Examples for Cybersecurity Leaders
Risk Register Examples for Cybersecurity Leaders
Risk registers are a widespread utility among many cybersecurity professionals that allow practitioners to track and measure risks in one place. This type of reporting can quickly help align your teams to the initiatives that matter and can save an organization valuable resources, time and labor. By utilizing compliance, scope and efficacy, any project team can utilize a risk register for the betterment of their cybersecurity.
Creating a register might seem easy using a generic risk register template found online, but properly and managing risk and potential impact can be difficult. Deciding what exactly goes into a risk register is dependent on your organization’s cybersecurity posture, potential risks and identified risks. Optimally, your risk register should be used to create an inventory of potentially adverse events, with the likelihood, impact and description of an event to track the risk. With that should accompany a separate register to log control deficiencies that can contribute to the risks inside your risk register. Coordinating with stakeholders and other personnel in your company is necessary for accurately scaling and reviewing risk in your register. But using a risk register alone, proves nothing towards compliance if it’s not accompanied by a methodology to continuously monitor and track your compliance initiatives.
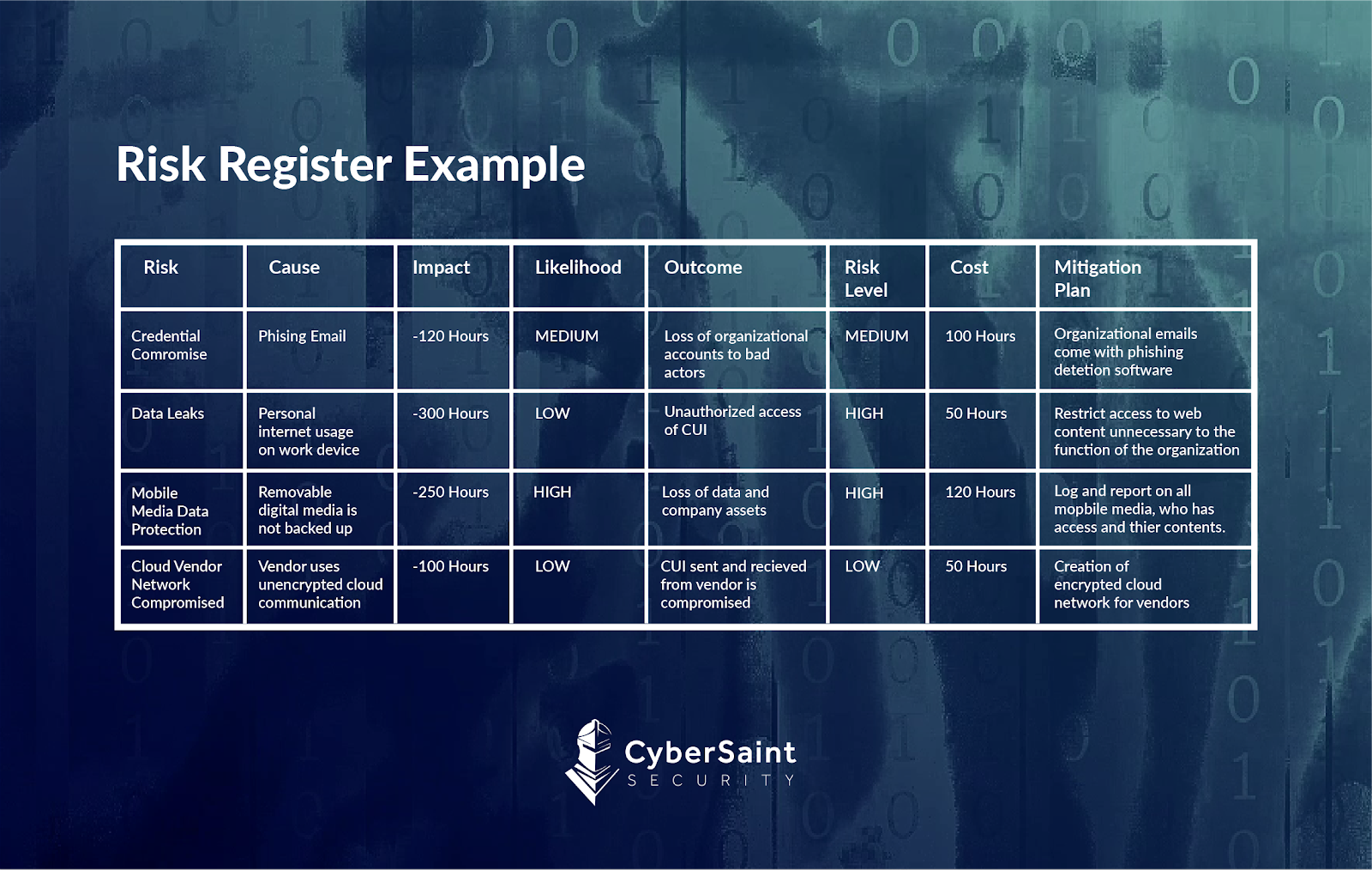
As shown below, your risk register should include:
- Risk Description: Describe the risk being measured and how it threatens the organization.
- Cause: The event or trigger that causes the risk to happen.
- Result or Impact: The impact your organization faces if the risk occurs.
- Likelihood: How probable the risk is to happen to your company.
- Outcome: How detrimental the risk can be if it happens.
- Risk Level: How high of a priority the risk is to your organization based on your risk matrix.
- Cost: Expense to mitigate the risk or minimize its impact as much as possible.
- Mitigation Actions: What actions were taken to mitigate the risk.
By using an Integrated Risk Management (IRM) solution responsible for managing risk continuously, risk registers function more as a method for reporting amongst team members than actively proving compliance. Being a static form of reporting, there’s potential room for error and impact on a project if a risk register is not supplemented by a continuous compliance solution. But having a risk register in place can help delegate across project risk management, track risk owners, prioritize your response plans, action plans, and risk response based on the risk category.
A multitude of cybersecurity frameworks and standards in use today require risk registers as a supplementary way of proving your organization is effectively executing its risk management processes in tandem with a continuous solution, like IRM. By utilizing an Integrated Risk Management solution like CyberStrong, you can prove compliance across a multitude of frameworks and measure your cybersecurity posture as a whole. Creating and maintaining a risk register can be automated and streamlined using CyberStrongs patented AI to quantify your risk and save your organization valuable time, labor and resources. If you have any questions about how to create a risk register or how using cyberstrong can help automate your compliance process, give us a call at 1-800-NIST CSF or click here and request a free demo.
Risk registers are a widespread utility among many cybersecurity professionals that allow practitioners to track and measure risks in one place. This type of reporting can quickly help align your teams to the initiatives that matter and can save an organization valuable resources, time and labor. By utilizing compliance, scope and efficacy, any project team can utilize a risk register for the betterment of their cybersecurity.
Creating a register might seem easy using a generic risk register template found online, but properly and managing risk and potential impact can be difficult. Deciding what exactly goes into a risk register is dependent on your organization’s cybersecurity posture, potential risks and identified risks. Optimally, your risk register should be used to create an inventory of potentially adverse events, with the likelihood, impact and description of an event to track the risk. With that should accompany a separate register to log control deficiencies that can contribute to the risks inside your risk register. Coordinating with stakeholders and other personnel in your company is necessary for accurately scaling and reviewing risk in your register. But using a risk register alone, proves nothing towards compliance if it’s not accompanied by a methodology to continuously monitor and track your compliance initiatives.
As shown below, your risk register should include:
- Risk Description: Describe the risk being measured and how it threatens the organization.
- Cause: The event or trigger that causes the risk to happen.
- Result or Impact: The impact your organization faces if the risk occurs.
- Likelihood: How probable the risk is to happen to your company.
- Outcome: How detrimental the risk can be if it happens.
- Risk Level: How high of a priority the risk is to your organization based on your risk matrix.
- Cost: Expense to mitigate the risk or minimize its impact as much as possible.
- Mitigation Actions: What actions were taken to mitigate the risk.

By using an Integrated Risk Management (IRM) solution responsible for managing risk continuously, risk registers function more as a method for reporting amongst team members than actively proving compliance. Being a static form of reporting, there’s potential room for error and impact on a project if a risk register is not supplemented by a continuous compliance solution. But having a risk register in place can help delegate across project risk management, track risk owners, prioritize your response plans, action plans, and risk response based on the risk category.
A multitude of cybersecurity frameworks and standards in use today require risk registers as a supplementary way of proving your organization is effectively executing its risk management processes in tandem with a continuous solution, like IRM. By utilizing an Integrated Risk Management solution like CyberStrong, you can prove compliance across a multitude of frameworks and measure your cybersecurity posture as a whole. Creating and maintaining a risk register can be automated and streamlined using CyberStrongs patented AI to quantify your risk and save your organization valuable time, labor and resources. If you have any questions about how to create a risk register or how using cyberstrong can help automate your compliance process, give us a call at 1-800-NIST CSF or click here and request a free demo.
*** This is a Security Bloggers Network syndicated blog from CyberSaint Blog authored by Justin Peacock. Read the original post at: https://www.cybersaint.io/blog/risk-register-examples-for-cybersecurity



