The SEVillage at DerbyCon was…. AH-MAZING

Let’s talk about it
October brought Social-Engineer to the SEVillage at DerbyCon 8.0 – Evolution, SEORG’s final SEVillage for the year, and WOW, was it an AMAZING DerbyCon. Ryan and Colin arrived Tuesday to set up shop and stuff many padfolios to prepare for their OSINT class that ran over Wednesday and Thursday. The OSINT class was Social-Engineer’s largest class EVER and it sold out in TWELVE SECONDS. Yes. You read that correctly. Our largest class sold out in 12 seconds. The students loved it, and one team even finished the final hands-on challenge in just over an hour when it usually takes multiple hours. A second team slid past the finish line in the nick of time, just before class ended on Thursday.
After class, the rest of the team rolled into Louisville, KY where DerbyCon was held at the Marriott downtown, instead of the Hyatt, for the first time. Our amazing volunteers and staff gathered together to set up the village and prep for the amazing few days to come.
Vishing data and the SECTF – Friday, October 4, 2018
Friday started for SEORG at noon when Cat Murdock and Chris Hadnagy took the Track 1 stage to present on Social-Engineer’s last-three years’ of vishing data in their speech “IRS, HR, Microsoft and your Grandma: What they all have in common.”

Cat gets psyched about data
Did you know that Mondays are the hardest day to compromise targets via vishing by a HUGE percentage?!? On Monday, social engineers are looking at a 29% compromise ratio compared to a 58%-65% compromise ratio any other day of the week. Apparently, employees hit the ground running on Mondays, are fresh off the weekend, and ready to secure their information from SEs.

Chris and Cat drop some data knowledge

That one-time Cat stole Dave’s hat but everyone got iced anyway
After the speech, the SEVillage team raced back to launch the 2nd SECTF at DerbyCon. The room was PACKED, with audience members sitting on the floor and lining the walls.

A completely packed room awaited the SECTF at DerbyCon
This year, the targets featured were large energy companies including Halliburton, Phillips 66, Devon Energy, Noble Energy, and Sunoco. While these targets were particularly challenging, and some even had systems that had to ethically be avoided for competition’s sake, it was one of the most entertaining SECTFs to date.

DEF CON’s 2nd place winner and always amazing audience member – Rachel Tobac
All the contestants were able to get targets on the phone and elicit many flags. The competition was SO fierce, the difference between the first and second place winner was only a single flag, making for a great competition. In the end, Krittika’s amazing reporting and calls won her the first-place trophy. This means that all the winners of the SECTF prizes this year were women!!! Get it, ladies!
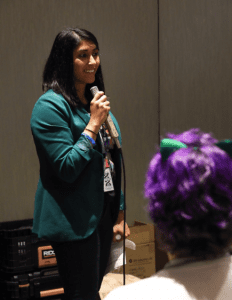
Our DerbyCon 1st place winner, Krittika, Answering some Q&A after calls

The first competitor started the afternoon off right! Soooo many flags!

This sweet SECTF trophy finally found its forever home!
Can you fool the Polygraph, Mission SE Impossible,and Ethics– Saturday, October 5
Saturday at Derby is always an amazing day, as it starts off with the incredibly unique “Can you fool the Polygraph” challenge. Our reigning champion from 2017 began as the first competitor in this competition.

Reigning champ defends his title!
Contestants had to answer extremely uncomfortable questions while attempting to trick the polygraph machine, which has sensors measuring reactions on the chest, fingers, and even your butt. Questions ran along the lines of, “have you ever taken credit for a coworker’s accomplishments?” As well as, “do you regularly urinate in the shower?” Ultimately, our ferocious, and possibly psycho/sociopathic, competitors ended in a three-way tie!! Whaaatt….

With game faces like this, the tie was not surprising
Clearly, we couldn’t end in a tie. So, our amazing polygraph examiner created a tie breaker for us on the spot! Thanks, Jacob. The tie breaker was having the contestants answer “no” to the question, “Is it <insert day of the week here>?” Each contestant was asked five days of the week, including “Saturday,” the day the competition occurred, and they had to answer “no” to each objective question. The individual who lied the best won!
CONGRATS TO OUR WINNER SCOTT!!!

The most convincing liar of them all – Well done, Scott!
After a brief lunch break, the Village rallied for Mission SE Impossible, a staged “escape room” type competition where competitors have to shim themselves out of handcuffs and leg cuffs, pick a lock, analyze microexpressions, and traverse a laser grid produced by tiny sharks with lasers on their freakin’ heads.

No pressure or anything, but I hope he hustles with all those people watching…

Will he break free?!?! Spoiler alert – he did.

The SEVillage is family friendly, and this kid ROCKED it!
Disclaimer: No sharks were harmed in the making of MSI

Super sweet lasers in the HOUSE

Commitment to dodging those laser sharks

Our winner, squeezing through lasers on his way to victory
Ultimately, MSI ended with our winner, Rick, slamming the competition by finishing in RECORD time at 59 seconds. CONGRATULATIONS, RICK!!!!
Once MSI wrapped up, we only had one SEVillage activity remaining; a panel on Ethics in Social Engineering featuring Jamison Scheeres, Chris Silvers, Rachel Tobac, Grifter, and Chris Hadnagy. This panel was inspired by our recently released Social Engineering Code of Ethics, as, after its release, it quickly became a community tool and topic. It was truly wonderful to see a packed house looking to discuss ethics in our work from 6-8PM on a Saturday.

Full house for the ethics panel
The discussion was amazing, all viewpoints and questions were compelling and deep. Ultimately the community is made stronger when we can have tough conversations like these, where we really dig into thinking about where the tactics we use can take an emotional toll on targets while still being a necessary precaution to protect against malicious actors. A full recording of this panel is available here. #NotAPhish

The participants of the Ethics in Social Engineering Panel, Jamison, Chris S, Rachel, Grifter, and Chris H

Jamison dropping some deep thoughts
Wrap up – Sunday, October 6, 2018
Sunday, the team packed up the village and wearily found brunch in Louisville before heading to closing ceremonies, officially wrapping up the SEVillage at DerbyCon as well as all SEVillages for 2018. The weekend was truly an epic con, and we are always so grateful to be able to attend. We could not do it without our sponsor, Red Sky, or our amazing team. A huge thanks to Jim, Kris, Chris, Hannah, Evan, Spencer, Colin, Ryan, Cat, and Chris H – the weekend would literally not be possible without these wonderful individuals.

Colin manning that swag booth!

These are some great people!
Thank you all and be looking for the SECTF report that dives into the data from all our 2018 SECTF competitions!! The webinar discussing the report will be at 2PM ET on November 28. You can sign up now and don’t forget to mark your calendars!
Sources
http://www.irongeek.com/i.php?page=videos/derbycon8/track-1-00-irs-hr-microsoft-and-your-grandma-what-they-all-have-in-common-christopher-hadnagy-cat-murdock
https://www.social-engineer.org/resources/ethics-in-social-engineering-sepanel-at-derbycon-viii/
https://www.social-engineer.org/framework/general-discussion/code-of-ethics/
The post The SEVillage at DerbyCon was…. AH-MAZING appeared first on Security Through Education.
*** This is a Security Bloggers Network syndicated blog from Security Through Education authored by Social-Engineer.Org. Read the original post at: https://www.social-engineer.org/general-blog/the-sevillage-at-derbycon-was-ah-mazing/



