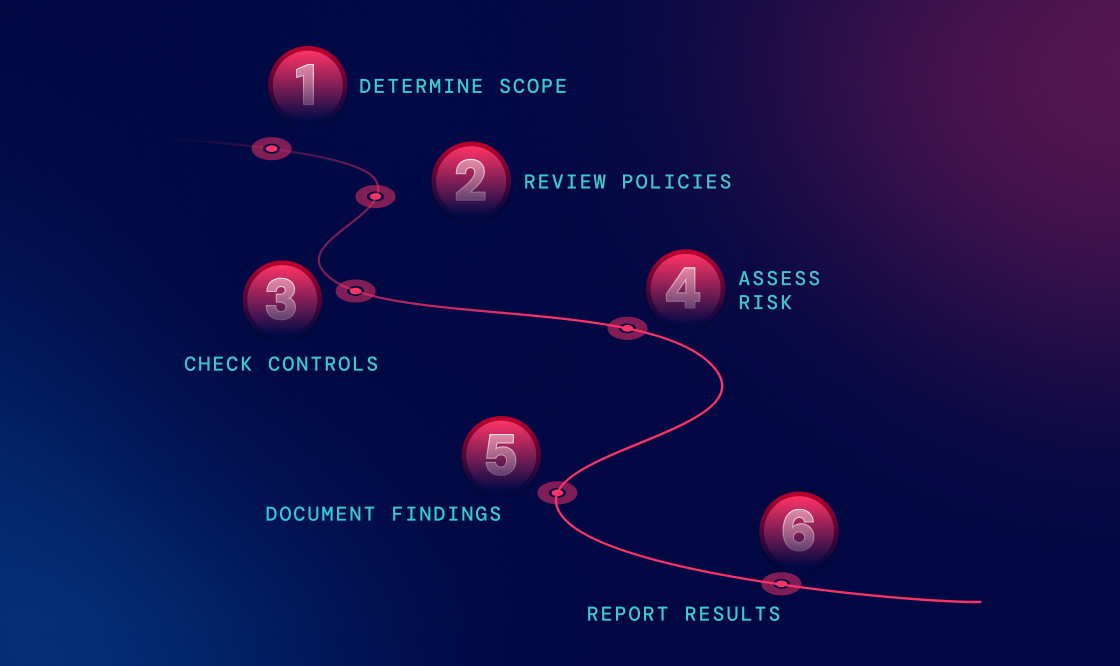
How to Conduct a Cybersecurity Compliance Audit in 6 Steps
How to Conduct a Cybersecurity Compliance Audit in 6 Steps
Whether you’re preparing for a cybersecurity audit and compliance review or working to meet standards like ISO 27001, NIST, SOC 2, or GDPR, the traditional fragmented approach simply isn’t sustainable. That’s why organizations are turning to security automation, control mapping, and continuous monitoring as essential tools.
In this guide, we’ll walk through six practical steps to help you conduct a cybersecurity compliance audit, driven by automation, real-time control validation, and audit preparedness.
What is a Cybersecurity Audit and Why is it Needed for Regulatory Compliance?
A security compliance audit is a formal evaluation of an organization’s cybersecurity policies, controls, and practices to ensure alignment with regulatory and industry standards.
Failing to conduct regular audits can expose your business to:
- Data breaches that compromise sensitive information
- Operational disruptions that damage business continuity
- Legal and regulatory penalties, including fines and reputational damage
An effective cybersecurity compliance audit helps organizations prevent these issues by proactively identifying vulnerabilities and demonstrating accountability to customers and regulators.
Next, we’ll walk you through six key steps to conduct a successful cybersecurity compliance audit—efficiently and with confidence.
1. Define Regulatory Requirements and Compliance Scope
Before diving into evidence collection, clearly define which compliance frameworks or regulations your organization must follow. These may include:
- SOC 2 for service organizations
- HIPAA for healthcare
- ISO/IEC 27001 for global information security
- NIST CSF for federal agencies or vendors
Establish the scope of the audit by identifying the departments, data types, systems, and regions that fall under compliance requirements. Align each regulatory obligation to specific business processes and controls.
2. Perform Risk Assessments and Asset Inventory
Next, conduct a risk assessment to identify where your organization is most vulnerable. This involves:
- Mapping digital assets, including devices, applications, and data repositories
- Assessing threats and potential impact of breaches
- Ranking risk levels and defining mitigation strategies
A comprehensive asset inventory ensures nothing is overlooked and sets the foundation for compliance control mapping.
3. Automate Control Monitoring and Evidence Collection
One of the most significant challenges in maintaining compliance is keeping up with evidence collection—especially across distributed teams and systems. Manual processes tend to break down under pressure, leading to outdated or incomplete records.
To overcome this, organizations are increasingly adopting automated methods to monitor controls and collect audit evidence continuously. These systems validate whether controls are working as intended, track changes over time, and centralize audit artifacts in one place. The result is a more consistent compliance posture with significantly less overhead.
Swimlane’s Compliance Audit Readiness (CAR) solution is designed specifically for this purpose—enabling continuous compliance monitoring, reducing manual workloads, and ensuring audit readiness through automation.
4. Detect and Respond to Non-Compliance or Gaps
After your controls are in place, the focus shifts to vigilance. Identifying when something goes wrong—and acting on it quickly—is a core part of compliance readiness.
Start by defining what “non-compliance” looks like in your context. Then:
- Implement regular scans or reviews of key control areas
- Establish alerting mechanisms for deviations or failures
- Create a process to investigate, document, and resolve issues
What matters most is not perfection, but responsiveness. Timely remediation, combined with a documented history of corrective actions, shows auditors that your organization treats compliance as an ongoing discipline.
5. Document Policies, Procedures, and Controls
A strong compliance program is built on clear, well-maintained documentation. This isn’t just for the auditors—it ensures that your teams understand expectations and can respond consistently when incidents occur.
Your documentation should include:
- Security policies (e.g., access control, incident response)
- Defined procedures for applying and reviewing controls
- Control maps aligned to each compliance framework
- Revision history and approval records for traceability
Many teams treat this step as an afterthought. But when policies are hard to find—or worse, outdated—compliance readiness is compromised.
6. Conduct Internal Audits and Prepare for External Reviews
Before an external audit takes place, an internal audit helps validate your readiness and surface potential issues.
This internal review should mimic the structure of an external assessment as closely as possible. Consider:
- Reviewing all control tests and evidence for completeness
- Interviewing stakeholders to verify policy adherence
- Testing response workflows (e.g., access revocation or breach handling)
- Evaluating how quickly and accurately audit data can be retrieved
Internal audits serve a dual purpose: improving your compliance posture and building confidence across teams. They help turn compliance into a repeatable, scalable function—rather than a stressful, last-minute scramble.
Types of Cybersecurity Compliance
SOC 2
Focuses on five trust service principles: security, availability, processing integrity, confidentiality, and privacy. It’s a must-have for SaaS and service-based companies.
ISO/IEC 27001
A global standard that outlines best practices for an information security management system (ISMS). Ideal for companies operating across multiple jurisdictions.
NIST Cybersecurity Framework (CSF)
Developed by the National Institute of Standards and Technology, it provides a flexible approach to managing and reducing cybersecurity risk.
HIPAA (Health Insurance Portability and Accountability Act)
Applies to healthcare providers and business associates managing protected health information (PHI). Ensures patient data privacy and security.
Cybersecurity Compliance Audit Best Practices
- Leverage automation to reduce audit prep time
- Use a unified platform for control mapping across frameworks
- Engage stakeholders early, including compliance officers, IT, and legal
- Monitor continuously, not just once a year
- Train teams regularly on evolving requirements and tools
Cybersecurity compliance audits are no longer optional—they’re essential for regulatory alignment, risk reduction, and customer trust. Using AI automation platforms like Swimlane Turbine can dramatically streamline the audit process, reduce manual effort, and improve control reliability across your organization.
Learn how Swimlane Turbine simplifies compliance and keeps your organization audit-ready.
Cybersecurity Audit FAQs
What is a compliance audit in cybersecurity?
It’s a formal process to assess whether an organization’s cybersecurity controls align with regulatory standards and internal policies.
How frequently should you conduct a cybersecurity audit?
At least once a year or more frequently if required by industry standards, risk exposure, or after significant changes.
What is the difference between a cybersecurity audit vs. an IT audit?
An IT audit covers all aspects of IT systems and processes, while a cybersecurity audit focuses specifically on protecting data, systems, and networks from cyber threats.
Do you conduct a cybersecurity audit internally?
Yes, internal audits are conducted by the organization’s own teams to assess readiness. External audits are performed by certified third parties.
Request a demo
If you haven’t had the chance to explore Swimlane Turbine yet, request a demo.
The post How to Conduct a Cybersecurity Compliance Audit in 6 Steps appeared first on AI Security Automation.
*** This is a Security Bloggers Network syndicated blog from Blog Archives - AI Security Automation authored by Jack Rumsey. Read the original post at: https://swimlane.com/blog/cyber-security-compliance-audit/