When the Perimeter Fails: Microsegmentation as the Last Line of Defense
According to a recent review of cybersecurity tools deployed in enterprises, the average number of tools in an enterprise stood at 32. Most of these tools keep bad actors from penetrating the enterprise perimeter. We should recognize that the modern enterprise is no longer a single campus or a data center, but a collection of server and end-user devices spread across enterprise-owned facilities, public clouds, and remote/home offices. The perimeter definition should, therefore, include data centers, public clouds, LANs, user devices, and even the user identity. Cybersecurity vendors have developed various tools to protect these perimeters. However, despite the best efforts of the vendor or the enterprise customer’s configuration of the tool, there are bound to be weaknesses that attackers can discover and exploit.
Let’s look at some perimeter security tools and their weaknesses that bad actors have exploited.
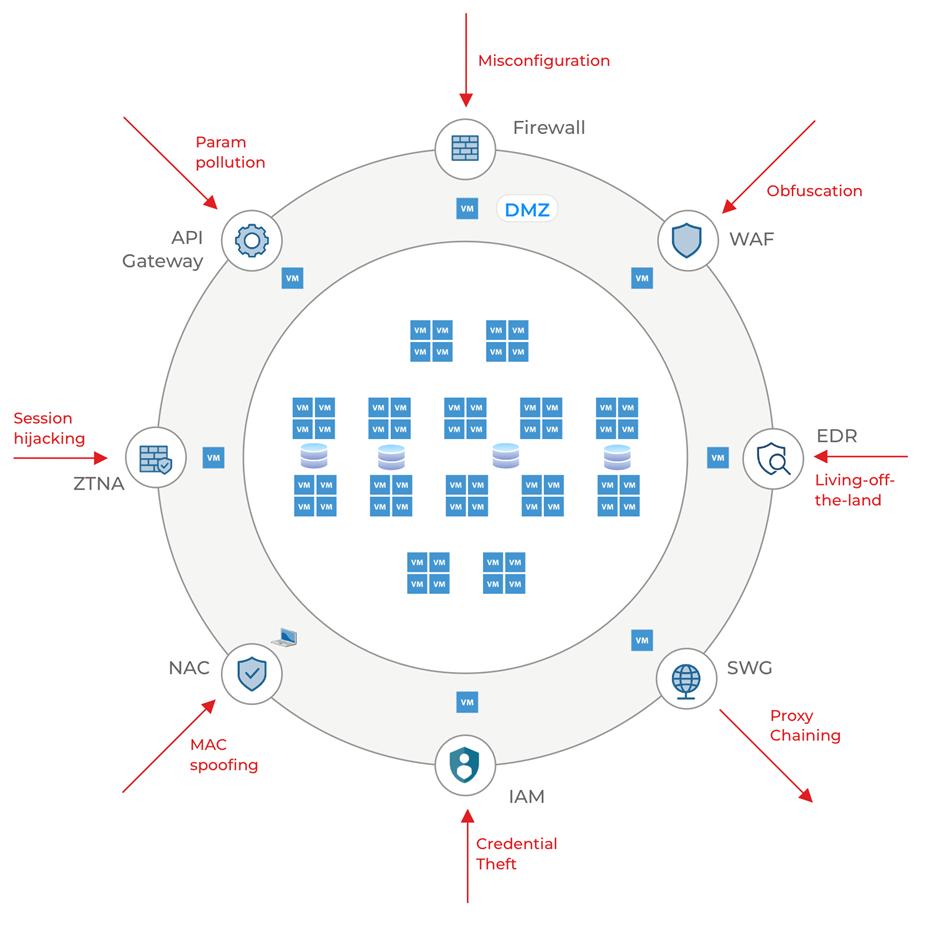
Firewalls block unauthorized access to internal systems from bad actors via the Internet. However, misconfigurations or overly permissive policies may allow adversaries to connect to internal systems using SSH or RDP.
Web Application Firewalls (WAFs) prevent exploitation of known vulnerabilities but are less effective against unknown or zero-day exploits.
We include Endpoint Detection and Response (EDR) tools in this discussion because a laptop computer is a perimeter of its own when operated outside the enterprise network. Attackers can use techniques such as obfuscation, living off the land, etc., to circumvent EDR solutions.
The three examples we have looked at address inbound threats. Now let’s consider malware exfiltrating data or communicating with the attacker’s command and control (C2 or CnC) server. Secure Web Gateways (SWGs) monitor traffic destinations and can prevent data exfiltration to known malicious sites or C2 communication disguised as web traffic. However, the malware may use proxy chaining to route the HTTP session via a permitted proxy or VPN system and evade the SWG solution.
We have been talking about network and device perimeters thus far. Still, some call for identity as the new perimeter as users connect to enterprise systems from enterprise and non-enterprise networks and devices. Identity and Access Management (IAM) systems now offer more robust authentication methods like multi-factor authentication. However, credential theft is still a weakness as passwords are often re-used and easily found on the dark web. Non-human identities like services and agents are also prevalent, and subject to credential abuse with access keys harvested from public source-code repositories.
Network access control (NAC) solutions restrict enterprise access to authorized and compliant users in campus environments. Zero Trust Network Access (ZTNA) solutions perform the same function for remote environments. Both these solutions have weaknesses that attackers have exploited.
These are just a few of the many solutions that make up the cybersecurity stack of most enterprises, and none are without a weakness.
Now that we understand that guarding the perimeter from being breached 100% of the time is impossible, let us consider the ramifications of the initial compromise. In most cases, the first system exploited by the attacker is of little consequence. However, it provides the attacker a vantage point to scan the network and discover other systems, such as databases, file servers, domain controllers, etc., that contain valuable data to exfiltrate or encrypt for ransom. Frequently, the immediate neighbors of the initial compromise are also uninteresting, so the attacker moves laterally to one or more neighbors, and the process continues.
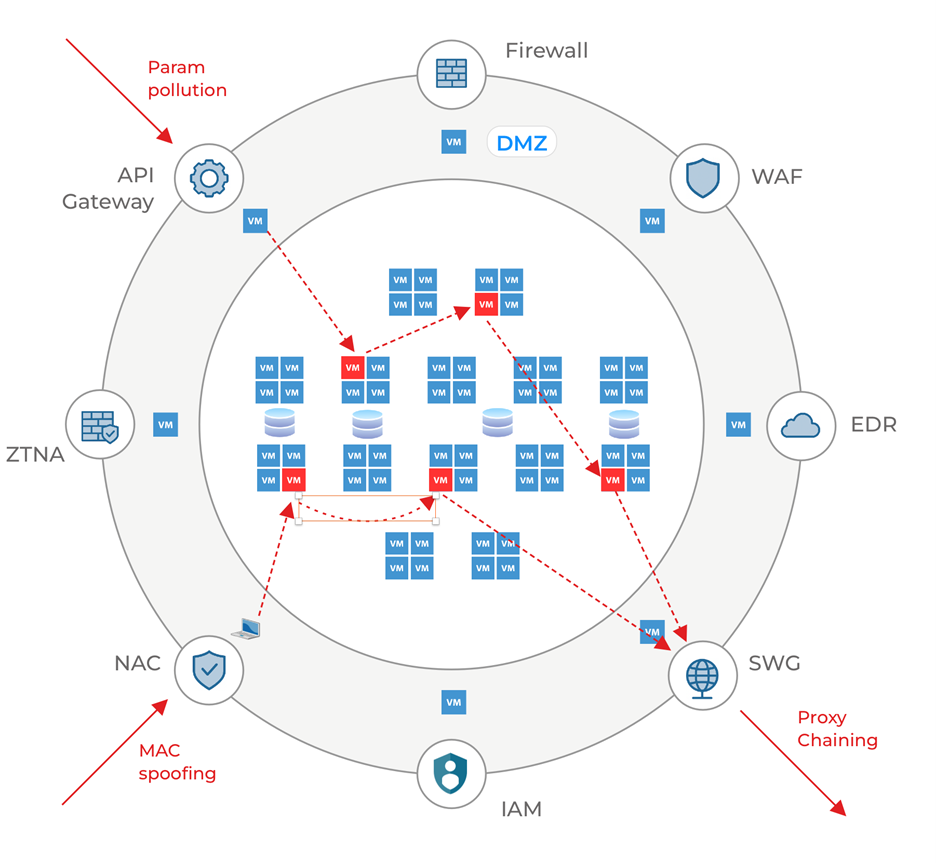
The figure above shows two scenarios where the attacker uses techniques to defeat an API gateway and a network admission control (NAC) system, and then uses lateral movement to find systems of interest, and then uses proxy chaining to exfiltrate data past a secure web gateway (SWG).
Post-mortem analyses of numerous data breaches have revealed that attackers frequently use lateral movement to find systems of interest after gaining initial entry into the enterprise network. We know that perimeter tools cannot prevent lateral movement. Still, many organizations believe that VLAN-based network segmentation and their EDR or NDR systems provide sufficient defense. Let’s discuss why this is incorrect.
VLAN-based segmentation addresses the need to limit the broadcast domain of networks and provide logical separation of networks. They are not a strong security measure against lateral movement, as most VLANs will span multiple applications and systems, allowing an attacker to move freely within the VLAN and find ways to jump across VLANs.
EDR systems protect the endpoint from various attacks, but do not address lateral movement. When the attacker performs a network connection for discovery or lateral movement, the EDR system cannot distinguish this from a legitimate application or an administrator’s attempt to perform the same connection with certainty. The inability to detect a malicious action from a legitimate action is why post-mortem breach analyses often show few or no EDR alerts.
Network detection and response (NDR) systems are probably best equipped to detect lateral movement as they specifically monitor network connections between systems. However, these systems are expensive to deploy pervasively, leading to many blind spots. Furthermore, these tools can detect lateral movement, but rely on other systems like SIEMs to eliminate false positives and initiate a remediation action.
For these reasons, we need a purpose-built solution to prevent lateral movement, and leading cybersecurity standards organizations and experts recommend microsegmentation. Microsegmentation enables the creation of micro-perimeters around systems and devices. The organization then determines what network communications must be allowed between and within these micro-perimeters. The microsegmentation solution enables the testing and enforcement of these least-privilege policies to prevent arbitrary lateral movement by attackers.
Access Report | GigaOm Radar Report evaluates 15 top microsegmentation vendors. Know why ColorTokens is the only vendor to earn a perfect 5.0 score in every category of the Key Features comparison.
The figure below shows the same two attack vectors we discussed previously, but the network now implements microsegmentation. While this does not prevent the initial compromise, it confines the attacker to the microsegment and cannot traverse the network, looking for more critical systems.
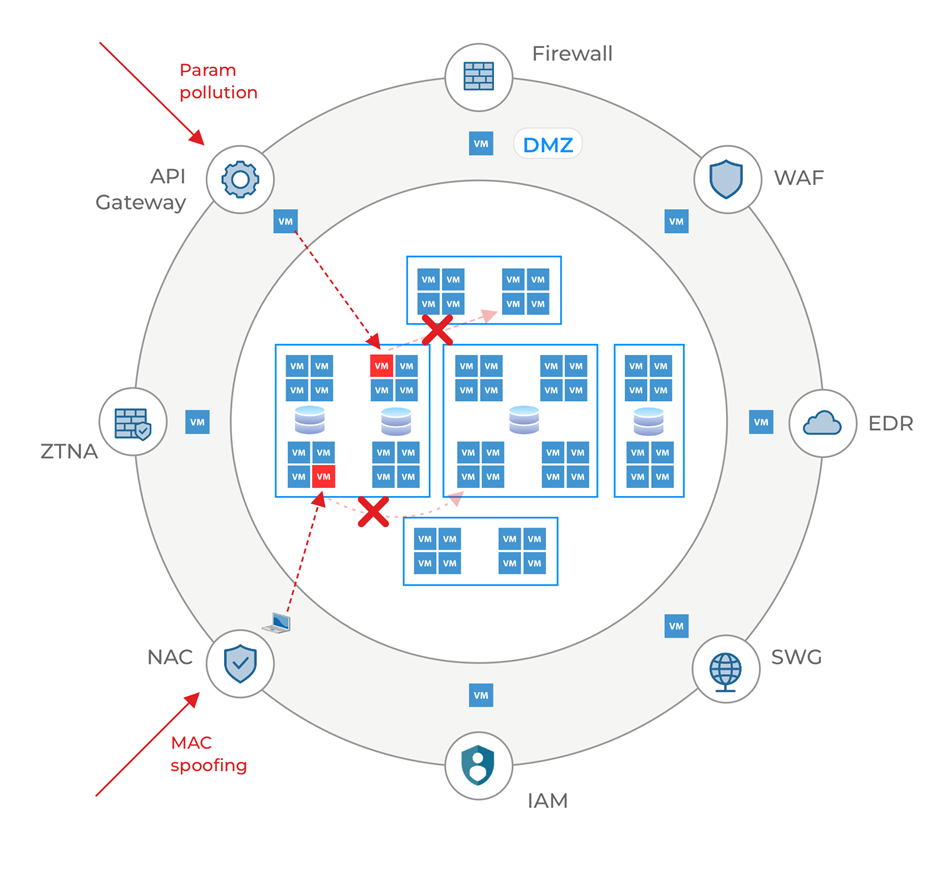
In conclusion, each element in the security stack addresses a family of threats. However, most perimeter security products focus on preventing an incursion, but do nothing if an attacker gets in by exploiting a weakness or finding an alternative entry point. Microsegmentation of the network is the only way to ensure that an inevitable breach is limited to the initial victims and does not result in enterprise-wide disruption and a business crisis.
If you want to see how microsegmentation can work in your environment, drop us a note here.
The post When the Perimeter Fails: Microsegmentation as the Last Line of Defense appeared first on ColorTokens.
*** This is a Security Bloggers Network syndicated blog from ColorTokens authored by Venky Raju. Read the original post at: https://colortokens.com/blogs/microsegmentation-lateral-movement-defense/



