Cybersecurity Snapshot: CISA’s Best Cyber Advice on Securing Cloud, OT, Apps and More
In this special edition of the Cybersecurity Snapshot, we’re highlighting some of the most valuable guidance offered by the U.S. Cybersecurity and Infrastructure Security Agency in the past 12 months. Check out best practices, recommendations and insights on protecting your cloud environments, OT systems, software development processes and more.
In case you missed it, here’s CISA’s advice on six cybersecurity areas.
1 – How to choose cyber secure OT products
If your organization is shopping around for operational technology (OT) products, CISA published a guide in January 2025 aimed at helping OT operators choose OT products designed with strong cybersecurity features.
Titled “Secure by Demand: Priority Considerations for Operational Technology Owners and Operators when Selecting Digital Products,” the publication highlights 12 cybersecurity elements that OT products should have, including:
- Support for controlling and tracking modifications to configuration settings
- Logging of all actions using open-standard logging formats
- Rigorous testing for vulnerabilities and timely provision of free and easy-to-install patches and updates
- Strong authentication methods, such as role-based access control and phishing-resistant multi-factor authentication, to prevent unauthorized access
- Protection of the integrity and confidentiality of data at rest and in transit
According to CISA, many OT products aren’t designed and developed securely, so they ship with issues such as weak authentication, known vulnerabilities and insecure default settings.
In fact, the agency says it’s common for hackers to specifically target OT products they know are insecure, instead of going after specific organizations. Thus, it’s critical for organizations, especially those in critical infrastructure sectors, to pick OT products that are built securely.
“When security is not prioritized nor incorporated directly into OT products, it is difficult and costly for owners and operators to defend their OT assets against compromise,” reads the guide, published in collaboration with other U.S. and international agencies.
Back in September 2024, CISA sounded the alarm on critical infrastructure organizations’ susceptibility to common, well-known attack methods in its “CISA Analysis: Fiscal Year 2023 Risk and Vulnerability Assessments” report.
The report’s findings are based on risk and vulnerability assessments (RVAs) of the security of 143 critical infrastructure organizations that CISA and the U.S. Coast Guard conducted in 2023.
Specifically, CISA and USCG assessors had the most success gaining initial access, attaining network permanence, evading defenses and moving laterally by using valid accounts, phishing schemes and default credentials — all simple attack methods.
For example, the use of valid accounts, which are legitimate accounts whose login credentials have been compromised, was the most successful attack technique for achieving:
- Initial access (41.3%)
- Persistence (42.2%)
- Privilege escalation (44.7%)
Valid-account use also ranked as the second most successful attack technique for evading defenses.
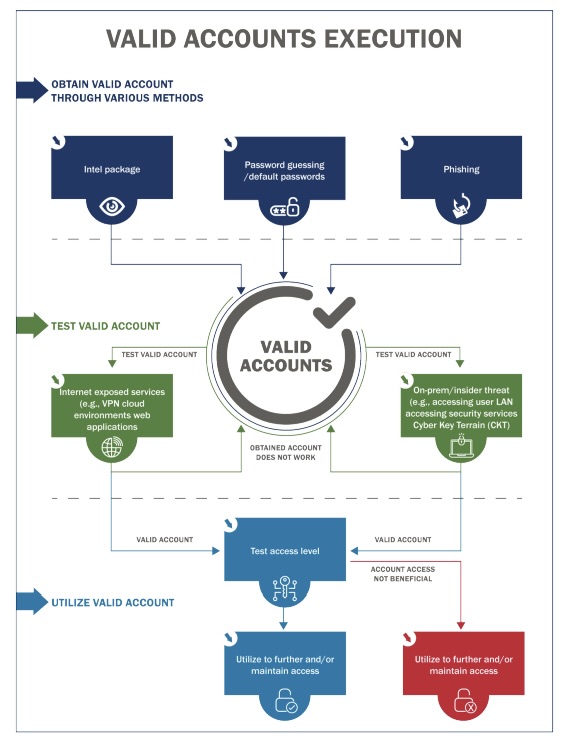
(Source: “CISA Analysis: Fiscal Year 2023 Risk and Vulnerability Assessments” report, September 2024)
The report offers troves of recommendations to critical infrastructure organizations, including:
- Adopt a secure password policy that requires phishing-resistant multi-factor authentication for remote access; strong passwords; unique credentials, and more.
- Maintain a comprehensive asset inventory, and keep software updated and patched.
- Segment networks and block outbound connections from internet-facing servers to prevent lateral movement and privilege escalation.
For more information about protecting critical infrastructure environments and about operational technology (OT) security, check out these Tenable resources:
2 – What SBOMs are and how to implement them
Looking to learn more about software bills of materials (SBOMs), which in theory help boost your software supply chain security by listing all ingredients in a software product, such as an application?
In October 2024, CISA updated the document “Framing Software Component Transparency,” which offers foundational guidance about SBOMs, such as what they are and how to implement them.
SBOMs’ purpose is to provide granular visibility into all software components in your environment. Thus, an SBOM should help you locate all instances of a component with a newly disclosed flaw, such as a critical vulnerability — as happened with the Log4j utility.
However, the software industry is still working through complex SBOM-related challenges in areas including standards, data comprehensiveness and interoperability.
“Framing Software Component Transparency” zeroes in on the challenge of “universally identifying and defining certain aspects of software components.”
Specifically, the CISA guidance states the need to:
- Establish a minimum set of baseline attributes for identifying components “with sufficient relative uniqueness.”
- Identify optional attributes beyond the baseline ones.
- Correlate SBOMs with third-party sources for analysis purposes.

A few months later, CISA tackled a related topic: secure software development.
The best practices are organized into two categories — software development process goals and product design goals — and include:
- Software development process goals:
- Address vulnerabilities before releasing the software product, and publish a vulnerability disclosure policy.
- Separate all software development environments, including development, build and test, to reduce the lateral movement risk.
- Enforce multi-factor authentication across all software development environments.
- Securely store and transmit credentials.
- Product design goals
- Reduce entire classes of preventable vulnerabilities, such as SQL injection vulnerabilities, memory safety vulnerabilities and cross-site scripting vulnerabilities.
- Provide timely security patches to customers.
- Don’t use default password in your products.
- Let users know when your products are nearing end-of-life status and you will no longer provide security patches for them.
The recommendations “will help to protect the sector from cyber incidents, identify and address vulnerabilities prior to product release, improve incident response, and significantly improve software security,” CISA said in a statement.
For more information about SBOMs:
- “How Our Business Complies with SBOM Recommendations” (DevProJournal)
- “How to create an SBOM, with example and template” (TechTarget)
- “SBOMs – Software Supply Chain Security’s Future or Fantasy?” (SecurityWeek)
For more information about secure software development:
- “CISA Tells Tech Vendors To Squash Command Injection Bugs, as OpenSSF Calls on Developers To Boost Security Skills” (Tenable)
- “Secure Development” (Software Engineering Institute, Carnegie Mellon Univ.)
- “Secure Software Development Framework” (NIST)
3 – Key takeaways from red team exercises
In July 2024, CISA published a must-read report explaining how its red team probed a large federal agency’s network, quickly found a way in and stayed undetected for months.
The 29-page report details the so-called SilentShield assessment from CISA’s red team, explains what the agency’s security team should have done differently and offers concrete recommendations and best practices you might find worth reviewing.
Mimicking the modus operandi of a typical nation-state attacker, CISA’s red team exploited a known vulnerability on an unpatched web server, gaining access to the agency’s Solaris environment. Separately, the red team also breached the network’s Windows environment via a phishing attack.

Once inside, the red team exploited other weaknesses, such as unsecured admin credentials, to extend the scope of the breach, which went undetected for five months. At that point, CISA alerted the agency about the SilentShield operation.
CISA has authorization to conduct SilentShield assessments, whose purpose is to work with the impacted agency and help its security team strengthen its cyberdefenses.
Here’s a brief sampling of the assessed agency’s security weaknesses:
- Lack of sufficient prevention and detection controls, including an inadequate firewall between its perimeter and internal networks; and insufficient network segmentation
- Failure to effectively collect, retain and analyze logs, which hampered defensive analysts’ ability to gather necessary information
- Bureaucratic processes and siloed teams
- Reliance on flagging “known” indicators of compromise (IOCs) instead of using behavior-based detection
- Lack of familiarity with the identity and access management system (IAM), which wasn’t tested against credential-manipulation techniques nor were its anomalous-behavior alerts monitored
Recommendations include:
- Deploy internal and external firewalls
- Implement strong network segmentation
- Enroll all accounts in the IAM system, and make sure it’s not vulnerable to credential manipulation
- Centralize logging and use tool-agnostic detection
To get more details, read the report, titled “CISA Red Team’s Operations Against a Federal Civilian Executive Branch Organization Highlights the Necessity of Defense-in-Depth.”
For more information about the threat from nation-state cyber attackers:
- “What CISOs Need to Know About Nation-State Actors” (InformationWeek)
- “4 Ways to Defend Against Nation-State Attacks” (BankInfoSecurity)
- “Growing Nation-State Alliances Increase U.S. Cyber Risks” (Government Technology)
- “Nation-State Hackers Leverage Zero-Day Vulnerabilities to Penetrate MITRE Cybersecurity Research Network” (CPO Magazine)
4 – How to implement secure practices for cloud services
In a move to boost the U.S. government’s cloud security, CISA released in December 2024 a set of required cybersecurity actions for federal civilian agencies — mostly focused on applying secure configuration baselines to their cloud apps.
The mandate to secure cloud environments comes via the Binding Operational Directive (BOD) 25-01 — titled “Implementing Secure Practices for Cloud Services.”
“Malicious threat actors are increasingly targeting cloud environments and evolving their tactics to gain initial cloud access,” CISA said in a statement.
The guidance, while applicable only to U.S. federal civilian agencies, can be helpful to all organizations in the public and private sectors. Its foundation is CISA’s Secure Cloud Business Applications (SCuBA) project, which offers recommendations for hardening the configuration of cloud services.

“The scope of the BOD 25-01 includes all production or operational cloud tenants (operating in or as a federal information system) utilizing Microsoft 365,” Tenable Staff Research Engineer Mark Beblow explained in a recent blog about this directive.
“CISA may release additional SCuBA Secure Configuration Baselines for other cloud products which would fall under the scope of this directive,” he added.
Earlier in 2024, CISA joined the National Security Agency to publish five information sheets detailing cloud security best practices and mitigations in areas including cloud IAM; keys management; network segmentation and encryption; and data protection.
Here are the links to the documents:
To get more details and analysis on these cloud security best practices and mitigations, read the blog “CISA and NSA Cloud Security Best Practices: Deep Dive” from Tenable Senior Research Engineer Zan Liffick.
To learn more about cloud security, check out these Tenable resources:
5 – How to design software more securely
CISA has been pushing its “Secure by Design” program, which encourages software manufacturers to build cybersecurity into the design of their products, which the agency firmly believes would dramatically lower cyber risk.
Examples of this effort are CISA’s calls to stamp out well-known software flaws that nonetheless remain prevalent in applications and other software products, such as traversal vulnerabilities, OS command injection vulnerabilities and cross-site scripting vulnerabilities.

Also part of the program is the Secure by Design pledge, an initiative CISA launched in May 2024 to encourage software manufacturers to voluntarily commit to secure software development practices, such as using multi-factor authentication and being more transparent in vulnerability reporting.
Tenable was one of the 68 original signatories of the pledge. “This initiative is a commitment to enhance the security posture of our products and, by extension, the broader digital ecosystem,” Tenable CSO and Head of Research Bob Huber wrote in a blog.
As part of the Secure by Design initiative, CISA also reached out to technology buyers, encouraging them to seek software products designed and built securely. To help technology buyers make this assessment, CISA, joined by cyber agencies from the Five Eyes countries — Australia, Canada, New Zealand, U.S. and U.K. — published the guide “Secure-by-Design: Choosing Secure and Verifiable Technologies.”
The 40-page document seeks “to assist procuring organizations to make informed, risk-based decisions” about digital products and services, and is aimed at executives, cybersecurity teams, product developers, risk advisers, procurement specialists and others.
“It is important that customers increasingly demand manufacturers embrace and provide products and services that are secure-by-design and secure-by-default,” reads the guide.

The authoring agencies define the secure-by-design principles that software manufacturers should follow when building digital products and services. Here’s a sampling:
- Adopt a proactive, security-focused approach
- Align cybersecurity goals across all levels of the organization
- Mitigate threats through software design, development, architecture and security measures
- Design, build and deliver software with fewer vulnerabilities
The guide is divided into two main sections: External procurement considerations, which is by far the longest; and internal procurement considerations. Topics covered include:
- Supply chain risk management
- Open source software usage
- Data sharing
- Development process
- Maintenance and support
- Contracts, licensing and service level agreements
For more information about the secure-by-design concept:
- CISA’s “Secure by Design” home page
- “What Will It Take to Adopt Secure by Design Principles?” (Information Week)
- “10 security-by-design principles to include in the SDLC” (TechTarget)
- “Secure Product Design Cheat Sheet” (OWASP)
- “Lock Down the Software Supply Chain With ‘Secure by Design’” (Dark Reading)
6 – The importance of adopting a common security posture for your organization
Is your company considering implementing a consistent and uniform set of foundational cybersecurity practices for all teams and departments throughout the organization? If so, you might want to check out how CISA plans to lead such an effort across 100-plus federal agencies.
CISA will be in charge of the project, which it detailed in the document “Federal Civilian Executive Branch (FCEB) Operational Cybersecurity Alignment (FOCAL) Plan,” announced in September 2024.
The goal: To standardize the cybersecurity operations of civilian agencies in the executive branch, known by the acronym FCEB, to ensure they can all properly manage cyber risk in today’s complex and fast-evolving threat landscape.

Currently, these agencies architect their IT and cybersecurity operations independently, and consequently their ability to manage cyber risk varies. “There is no cohesive or consistent baseline security posture across all FCEB agencies” and as a result “the FCEB remains vulnerable,” CISA says in the FOCAL plan’s document.
The FOCAL plan focuses on five core areas:
- Asset management
- Vulnerability management
- Defensible architecture
- Cyber supply-chain risk management
- Incident detection and response
“The FOCAL Plan was developed for FCEB agencies, but public and private sector organizations should find it useful as a roadmap to establish their own plan to bolster coordination of their enterprise security capabilities,” CISA said in a statement.
To get more details, check out the Tenable blog “CISA Releases FOCAL Plan to Help Federal Agencies Reduce Cyber Risk” from Tenable Director of Security Engineering Garrett Cook.
*** This is a Security Bloggers Network syndicated blog from Tenable Blog authored by Juan Perez. Read the original post at: https://www.tenable.com/blog/cybersecurity-snapshot-cisa-advice-cloud-security-ot-security-appdev-security-sbom-secure-design-05-02-2025



