Anti-Ransomware Day: Hit With an Attack? What the Playbooks Don’t Tell You
Anti-Ransomware Day reminds us that ransomware is a business crisis waiting to unfold. Initiated by INTERPOL and Kaspersky in 2020, this global awareness day marks the anniversary of the infamous WannaCry outbreak—a ransomware attack that paralyzed systems in over 150 countries. It’s a call to move beyond reactive thinking and get serious about preparedness.
Yet even with heightened awareness and official playbooks in hand, many organizations still fall for outdated assumptions when it matters most. Because when ransomware hits your business in the gut, the reality rarely matches the script.
Below, we debunk four persistent ransomware incident response myths that could mean the difference between a contained incident and a full-blown crisis.
Myth #1: “Once ransomware hits, it’s too late.”
Is it game over the minute a ransom note flashes on your screen? Not if you’re prepared. The myth that “it’s too late” breeds a dangerous defeatism, when in fact quick containment can save the day.
Yes, data on the initially infected machines may be scrambled, but a ransomware outbreak doesn’t have to mean an enterprise-wide meltdown. In practice, ransomware does move fast, so it is imperative to perform hardening in advance, and have playbooks that can be executed on the first occurrence of an attack. This is where modern breach containment shines.
If you’ve built your network on zero trust principles – think microsegmentation – one compromised laptop doesn’t automatically mean the whole domain is toast. You can quarantine the affected segment, preserve unaffected systems, and limit the blast radius.
With the right containment tools, some organizations have even remotely killed ransomware processes mid-attack, saving critical servers. The bottom line: “too late” is a myth. With a well-drilled response plan and a segmented architecture, you can snatch victory from the jaws of defeat even after ransomware hits.
Download the GigaOm Radar Report | Ransomware spreads fast. See why ColorTokens’ containment-first approach earned a perfect score across the board.
Myth #2: “Backups mean you’re safe.”
Many organizations assume that as long as they back up their data, a ransomware attack is just a speed bump: we’ll simply restore everything and avoid paying ransom. It’s the ultimate safety net – on paper.
Backups are absolutely essential – but believing they alone will “save the day” is a myth. Why? Today’s ransomware gangs anticipate your backup strategy.
Attackers commonly destroy or encrypt backups as part of the attack.
- CISA highlights that tools like Vssadmin and Wbadmin are frequently misused to impair or wipe out backups.
- If your backups aren’t offline or protected, attackers will likely wipe them out before you can use them.
Modern ransomware attacks usually come with double extortion.
- Criminals not only lock your files but also steal sensitive data.
- They then threaten to leak it unless you pay.
Backups don’t protect against everything.
- Even with perfect backups, you’re still vulnerable if proprietary or customer data is stolen.
- Backups solve for data availability—not confidentiality or extortion.
By all means, keep robust, offline backups – that’s non-negotiable. But don’t mistake backups for a free pass to ignore other defenses.
True business resilience against ransomware demands a layered approach. This includes preventing the attack from reaching those backups in the first place (via network isolation of backup repositories and strict access controls), and limiting what the ransomware can do even if it lands.
Microsegmentation can fence off your backup servers or cloud storage so that an intruder in one network zone can’t even see, let alone access, the backup environment. Identity isolation ensures that even if an admin credential is compromised, it can’t be used to log into backup systems or delete snapshots.
Watch Now | Hear ColorTokens CEO Rajesh Khazanchi explain how containment stops threats from spreading across interconnected IT, OT, and IoT systems—in conversation with ISMG.
Myth #3: “Unplug everything to stop the spread.”
The first instinct many IT teams have when ransomware strikes is to yank every cable and shut down everything. After all, containment is step one in every incident ransomware response plan.
But CISA explicitly warns against rashly pulling the plug. Simply “powering down” systems might stop the malware – but it also wipes out crucial forensic evidence stored in memory. Drastic shutdowns should only be a last resort.
Don’t confuse that with unplugging everything. Isolation should be targeted and coordinated, not chaotic.
- With internal segmentation and east-west traffic controls, ransomware in one network zone (e.g. user VLAN) can’t easily spread to others (e.g. servers or OT networks).
- This architecture acts like firebreaks in a forest – the damage is contained by design.
Why segmentation matters: A tale of two networks
- Flat, unsegmented networks:
- One breach opens the door to everything.
- All systems live in a zone of implicit trust.
- Ransomware spreads laterally – fast.
- Responders panic and consider pulling every plug.
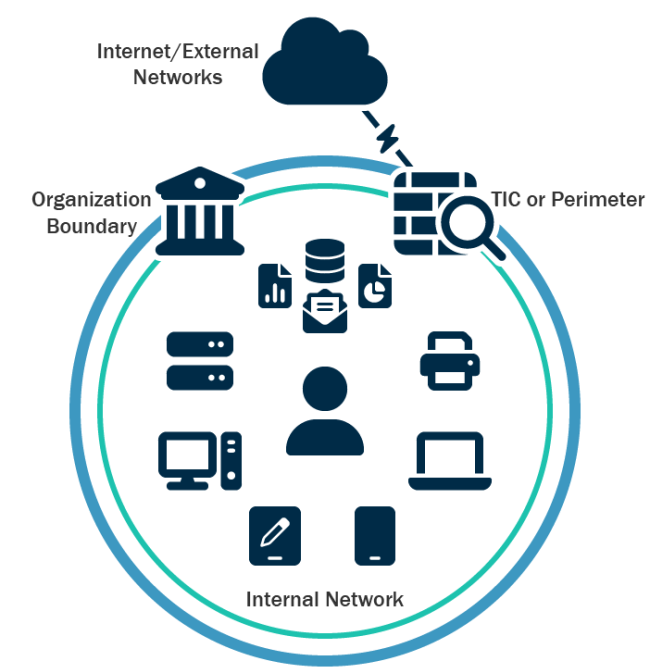
Figure: Flat (Unsegmented) Network. Source: CISA
- Well-segmented networks:
- Infrastructure is divided into isolated zones: user, guest, production.
- Microsegmentation and internal access controls throttle lateral movement.
- Ransomware in the user segment can’t leap to critical systems or backups.
- Containment is built-in – responders gain time to act without shutting everything down.
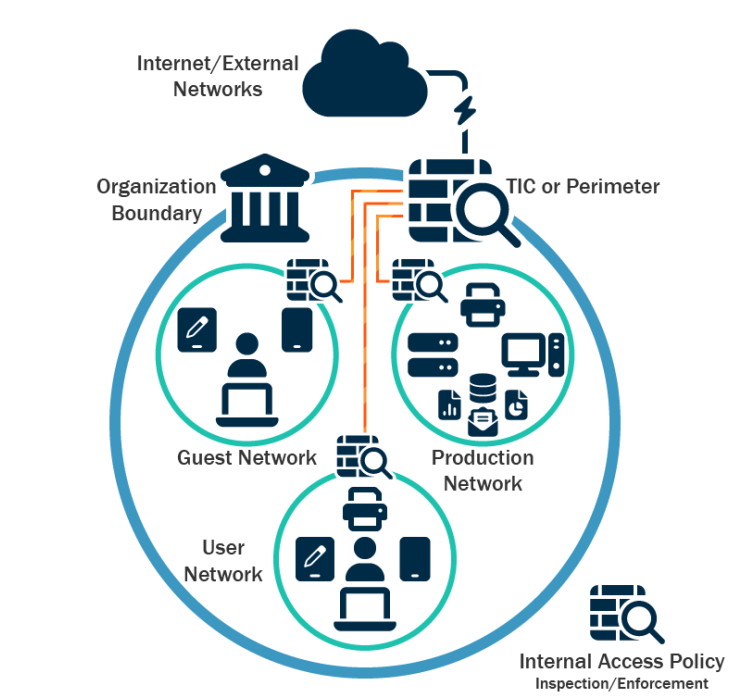
Figure: Segmented Network. Source: CISA
Build before you’re breached.
Don’t wait until the crisis to figure this out. Invest in segmentation and automated containment capabilities now.
- Deploy internal firewalls or software-defined policies to quarantine infected hosts instantly.
- Implement identity-based access controls so stolen credentials don’t grant full access.
- Automate response: some orgs detect ransomware-like behavior and cut access for the infected node automatically – without taking down the whole floor.
Access the Forrester Wave Report | OT and IoT are the new frontline. Learn why Forrester ranks ColorTokens ‘Superior’ in securing them.
Myth #4: “We’ll figure it out during the attack.”
“We’ll handle it when it happens” is a dangerous myth. When ransomware hits, everything speeds up—and melts down.
- Systems are locked.
- Alarms are blaring.
- Execs want answers.
- Customers might find out.
It’s pure chaos if you’re unprepared. And without a predefined playbook, you’ll lose valuable time just deciding:
- Should we pull the plug on internet access?
- Who alerts law enforcement?
- Are employees and clients in the loop?
Attackers count on this confusion—it gives them time to burrow deeper into your systems. Worse still, if you haven’t already deployed microsegmentation or identity isolation, you can’t roll it out mid-crisis. It’s too late.
Breach readiness is a business survival plan.
The most resilient organizations approach ransomware like a fire drill:
- Everyone from the CISO to the PR team knows the plan.
- Backup procedures are in place—like manual workarounds or alternate sites.
- Criteria for legal actions, ransom decisions, and law enforcement contact are clearly laid out—long before that countdown timer starts ticking.
The companies that weather ransomware best are those that assumed it would happen—and practiced for it. Those that think they’ll figure it out on the fly? Too often, they don’t.
Containment-First: The Mindset Anti-Ransomware Day Demands
Anti-Ransomware Day is a wake-up call to be ready when they land. Ransomware is the digital wildfire of our time, and perimeter defenses alone won’t stop it. It’s time to move beyond a perimeter-only mindset and embrace containment-first thinking.
That means assuming attackers will get in and focusing on how to trap and neutralize them once inside. This is the essence of being breach readiness by design: build your network like the enemy is already there.
- Microsegment your network so one compromised zone doesn’t bring down the rest.
- Lock down lateral movement with strict east-west traffic controls and proactive monitoring.
- Secure every workload individually—nothing is too small to be a target.
Containment buys you time, control, and confidence. The real test isn’t whether malware gets in—it’s whether it spreads. Architect your environment so that when ransomware hits, it hits a wall.
Anti-Ransomware Day is the perfect moment to shift from theory to action. Prepare now, contain decisively, and make your organization a place where ransomware has nowhere left to go.
If you want to know more about containment-first, breach ready strategies, reach out to us here.
The post Anti-Ransomware Day: Hit With an Attack? What the Playbooks Don’t Tell You appeared first on ColorTokens.
*** This is a Security Bloggers Network syndicated blog from ColorTokens authored by Tanuj Mitra. Read the original post at: https://colortokens.com/blogs/ransomware-incident-response/



