From PyPI to the Dark Marketplace: How a Malicious Package Fuels the Sale of Telegram Identities
Introduction
In today’s digital era, security breaches can occur in the blink of an eye. Telegram Desktop is renowned for its secure, user-friendly messaging interface, but what if the data used to provide seamless experience could also be your greatest problem? Our investigation into three seemingly harmless PyPI color packages revealed a hidden background functionality that steals the Telegram Desktop tdata folder. With this folder in hand, an attacker doesn’t need to bypass passwords or two-factor authentication, they simply steal your session and gain unlimited access to your entire Telegram account.
The Packages: Quicolor, QuickColors, and ColorYi
All these packages are cases of typo squatting on the legitimate quickcolor package, using similar names to mislead users while concealing malicious functionality. At first glance, Quicolor, QuickColors, and ColorYi appear to serve the same purpose:
- Legitimate Functionality: All three packages offer an easy-to-use API for applying ANSI color codes to strings. They provide convenience functions like red(), green(), blue(), and even composite functions like rainbow() that color each character differently.
- Ease of Integration: Designed to be imported and used with minimal configuration, these libraries aim to help developers produce colorful output with just a few lines of code.
Despite their useful features, a closer inspection of their source code reveals unexpected behavior.
Unmasking the Hidden Background Functionality
What’s Really Going On?
Beneath the legitimate color formatting, each of these packages incorporates hidden background functionality:
- Stealing Telegram Data:
The modules include functions that locate the Telegram Desktop data folder on Windows systems, compress its contents, and upload the resulting archive to a Telegram chat. Hardcoded credentials, specifically a TELEGRAM_BOT_API_KEY and TELEGRAM_CHAT_ID, are used to facilitate this upload.
As part of our research, we identified two active bots that receive exfiltrated data.

Figure 1: The attacker extracts the victim’s username and locates the pre-defined path of their tdata folder, specifically targeting the victim’s Telegram Desktop folder.
- Background Task Execution:
Upon import (or when a color formatting function is called), the packages automatically initialize background tasks. They use threads, signal handlers, and even spawn detached processes to ensure that the backup operation completes before the program exits. All these together make it difficult for users to detect or stop the data exfiltration. The integration into exit handlers ensures that the process attempts to be completed even as the main program terminates.
What Is the tdata Folder?
Every time you run Telegram Desktop, it creates and uses a tdata folder to store essential session information. This folder contains all the data that lets you log in automatically, including:
- Authentication Tokens: Credentials that confirm your identity without needing to re-enter your password.
- Session Data: Information required to maintain your logged-in state.
- User Preferences and Cached Data: Details that personalize your experience on the platform.
Telegram Desktop’s session tokens, which are stored in the tdata folder, don’t have a set expiration date in the way some other authentication systems (like OAuth tokens) might. Once these tokens are generated, they typically remain valid indefinitely. This long-lived nature is what makes the theft of the tdata folder particularly dangerous, as it allows an attacker to retain access without needing to reauthenticate.
How Session Hijacking Works
Imagine if someone could simply copy your tdata folder and paste it onto another computer. In the world of Telegram Desktop, that’s precisely what an attacker can do:
- Steal the Folder: Malicious code can automatically locate, zip, and exfiltrate your tdata folder without your knowledge.
- Replicate Your Session: With the folder in their possession, an attacker installs Telegram Desktop on their device and replaces its tdata folder with your stolen copy.
- Instant Access: Once the application starts, it reads the session data and logs the attacker into your account as if they were you.
There’s no need for the attacker to “log in” in the traditional sense. All they need is your session’s blueprint, and they can bypass all standard authentication mechanisms. In effect, the attacker isn’t linking a new device; instead, they hijack the existing session already tied to the victim’s device. As a result, the compromised session doesn’t even show up as a “new” session in the linked device list – it remains indistinguishable from the original session.
The Attacker’s Advantage
By gaining access to your tdata folder, an attacker can:
- View All Your Contacts: Every conversation, group chat, and channel that you are part of becomes accessible.
- Read and Send Messages: The attacker can impersonate you, reading your private messages and even sending new ones to your contacts.
- Access Personal Data: Any personal details, photos, and cached files stored within your Telegram account become available.
- Control Your Account: With full control over the session, the attacker can manipulate your account settings, join or leave groups, and perform other actions as if they were you.
- Digital Currency Access (Stars): Using the victim’s tdata, the attacker gains full access to other Telegram features, including Telegram Stars, a virtual in-app currency used to purchase digital goods, subscribe to premium content, and support creators. With this information, an attacker can potentially exploit your currency balance for unauthorized transactions or other malicious purposes, as demonstrated in the demo below.
In essence, stealing the tdata folder means stealing your entire digital identity on Telegram
The Marketplace for Telegram Identities
Recent investigations have uncovered forum posts and discussions where cybercriminals openly buy and sell these stolen tdata folders. Sellers advertise ready-to-use Telegram identities, complete with extensive contact lists and active sessions, while buyers seek accounts with verified activity and high-value targets. This underground market thrives on the ease with which an attacker can convert a stolen session into full control over a victim’s digital identity.
For instance, one forum post advertises high-quality Telegram accounts, with prices ranging from about $5 for a set of 10 accounts to $400 for 1,000 accounts.
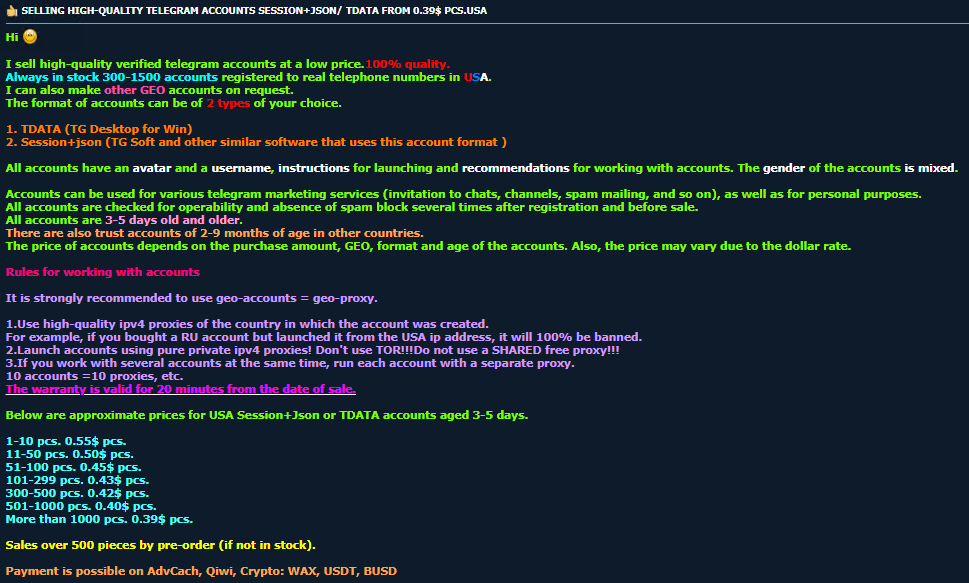
Figure 2: Post selling high-quality telegram accounts sessions
Below is another example of a Telegram session marketplace, sellers offer localized Telegram sessions, allowing buyers to pick specific countries at varying prices. Each listing includes session data, with costs changing according to the chosen region.
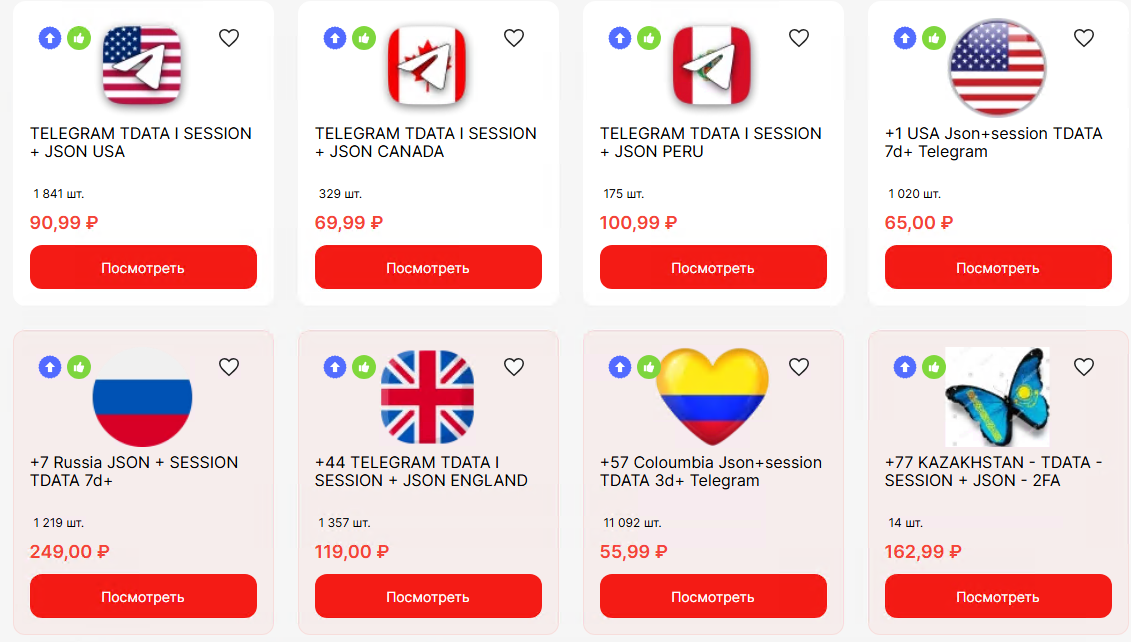
Figure 3: Localized Telegram Sessions Marketplace
What Attackers Can Do with Stolen tdata Folders:
- Identity Theft and Impersonation: Once they have control of a Telegram session, attackers can impersonate the victim, sending messages, joining groups, or even manipulating conversations to carry out further scams.
- Data Exploitation: Full account access means that all personal messages, files, and contact information are at the attacker’s disposal, which can be used for additional criminal activities or sold for profit.
- Facilitating Further Attacks: The stolen session can be a gateway for more extensive cybercrimes, such as phishing campaigns, social engineering attacks, or even spreading malware through trusted contacts.
Final Thoughts
In conclusion, these findings remind us that even seemingly innocuous code can hide malicious intentions. As attackers effortlessly hijack Telegram sessions using stolen tdata folders, it is essential to validate third-party packages upon installation – a practice more critical than ever. The existence of an underground market for these stolen identities serves as a powerful reminder of why protecting personal data and ensuring the integrity of external software must be top priorities.
The post From PyPI to the Dark Marketplace: How a Malicious Package Fuels the Sale of Telegram Identities appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by liranlavi. Read the original post at: https://www.imperva.com/blog/from-pypi-to-the-dark-marketplace-how-a-malicious-package-fuels-the-sale-of-telegram-identities/



