Securing Cloud Environments from Ransomware: A Primer
Imagine waking up to find your business’s critical data locked and held hostage—not by a simple attack on your local servers, but by an insidious, multi-layered strike targeting both your on-premises systems and cloud infrastructure. This is the grim reality many organizations now face in the age of cloud adoption. As businesses increasingly migrate to the cloud for its flexibility, scalability, and efficiency, they inadvertently open the door to a new wave of cyber threats.
Among these threats, ransomware stands out as one of the most alarming. Traditionally, ransomware has been confined to on-premises systems, where businesses could rely on tried-and-tested defense strategies. But in 2024, Storm-0501, a notorious ransomware group, changed the game. This advanced cybercriminal syndicate launched an attack on a hybrid cloud environment, compromising both on-premises systems and cloud-based infrastructure in a targeted and devastating campaign.
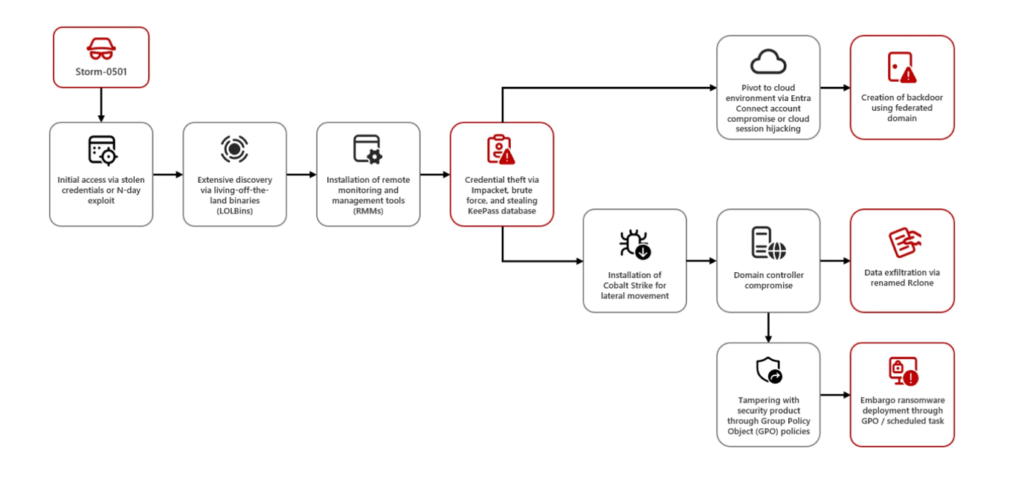
Diagram: Storm-0501 Attack Chain
Source
This attack was more than just a breach; it was a wake-up call. Storm-0501 demonstrated how cloud environments, once thought to be the fortress of business data, can now be a playground for cybercriminals. The hybrid nature of this attack exposed how vulnerabilities in interconnected systems, spanning on-premises and cloud resources can be exploited with devastating effect. The attackers bypassed traditional security measures, leveraging cloud-specific vulnerabilities, such as data exfiltration, lateral movement across hybrid networks, and delayed detection.
As organizations shift from traditional on-premises IT infrastructures to the cloud, they encounter new challenges, particularly around security. Ransomware attacks, once confined to on-prem environments, are evolving, targeting both on-prem and cloud systems. While the core principles of cybersecurity remain unchanged, protecting against unauthorized access, credential abuse, and lateral movement but the ways ransomware propagates in cloud environments present unique challenges that require tailored defenses. This post will explore these differences, highlighting key best practices that can help organizations defend their cloud environment against ransomware.
Preventing ransomware requires foundational cybersecurity measures, whether in on-prem or cloud environments. Some of the best practices include: Access Control & Identity Management (IAM), where the principle of least privilege limits user access based on role, preventing unauthorized access. Network Segmentation is the first step towards segmentation, ensuring that if an attacker gains entry, they cannot easily move across different zones. Multi-Factor Authentication (MFA) adds an extra layer of security by requiring more than a password for access to critical systems. Regular Data Backup ensures up-to-date, encrypted backups are available for recovery in the event of an attack. Patch Management keeps software and systems up to date, reducing vulnerabilities targeted by attackers. Network Monitoring detects potential ransomware activities by tracking user behavior and traffic patterns across environments, enabling early detection. Lastly, a solid Incident Response Plan outlines swift actions to take during an attack, minimizing downtime and damage.
While the foundational best practices for defending against ransomware remain constant, the nature of these attacks shifts dramatically when transitioning from on-prem to cloud environments. Ransomware exploits unique vulnerabilities in cloud infrastructures, where traditional defense strategies may fall short. The way ransomware propagates, spreads, and evades detection in the cloud requires a deeper understanding of its new attack vectors—highlighting the urgent need for tailored security measures that go beyond conventional approaches.
- Lateral Movement: A New Dimension in the Cloud
In on-prem environments, ransomware typically spreads using traditional lateral movement techniques like RDP (Remote Desktop Protocol) or SMB (Server Message Block). This movement is often facilitated by vulnerabilities within the network, where attackers exploit a flat network to move from one machine to another. In the cloud, lateral movement is more subtle and different. Instead of using direct port scanning or network access, attackers can leverage IAM roles to escalate privileges and move laterally. Cloud-based infrastructures like AWS or Azure allow users to configure IAM policies that might grant excessive permissions. Attackers can exploit these misconfigurations, gaining control over critical resources and escalating their access across the cloud infrastructure.Let us consider an example. A security engineer’s account in a cloud environment has been compromised through a phishing attack. Initially, the attacker gains only read-only access to a storage bucket. However, the organization has improperly configured IAM roles, giving the attacker the ability to escalate privileges. By exploiting a misconfigured IAM policy, the attacker gains write access to the bucket, allowing them to upload ransomware. As the attack escalates, they use these permissions to pivot through the environment, eventually gaining access to an EC2 instance and spreading the ransomware across the virtual machines and services. Because lateral movement in the cloud is facilitated through IAM misconfigurations rather than direct network access, the attack goes undetected until significant damage is done.
- The Shared Responsibility Model: A Double-Edged Sword:
Cloud providers like AWS, Microsoft Azure, and Google Cloud follow the shared responsibility model for security. Under this model, the provider is responsible for securing the cloud infrastructure, while the customer must secure their data, applications, and other resources within the environment. In an on-premises data center, security is entirely the organization’s responsibility, covering everything from physical security to network segmentation. In cloud environments, the provider manages the hardware, physical security, and virtualization layers, while the customer must secure everything within their deployment. Misconfigurations or gaps in securing the customer’s layer can be exploited by attackers, such as through exposed APIs that allow ransomware to gain access to critical systems.For example, an organization configures a cloud-based container orchestration system (like Kubernetes) to deploy their applications. While the cloud provider secures the underlying infrastructure, the customer is responsible for securing their applications within the cloud environment. The organization fails to properly configure the API endpoints of their Kubernetes cluster, leaving them exposed to the internet. A ransomware group scans for exposed APIs, identifies the misconfiguration, and gains access to the container orchestration system. From there, they deploy ransomware across several containerized applications, locking down critical business data. The organization assumed the cloud provider was handling everything, but the misconfigured API exposed a critical vulnerability.
- Shadow IT: A Growing Risk in the Cloud
Cloud environments enable quick scaling and greater autonomy for departments, leading to the rise of shadow IT: when employees or departments create their own IT resources without involving the central IT team. This presents significant risks, especially for ransomware, as these unsupervised resources often lack proper security controls. In the context of ransomware, shadow IT can create “hidden” attack vectors that are difficult to manage. For example, employees might expose a Virtual Private Cloud (VPC) to the internet or fail to implement necessary network segmentation. In traditional on-prem environments, shadow IT typically involved unauthorized hardware or software, but in the cloud, the ability to quickly spin up and expose resources increases the risk of weakly protected systems being targeted.Let us consider a marketing department that quickly provisions a cloud-based storage solution for a new campaign, without consulting the IT team. The department creates an S3 bucket in AWS, configuring it to be publicly accessible so that external partners can easily upload files. Unfortunately, the team forgets to enable proper encryption and access control policies. A ransomware group scans for open S3 buckets and discovers this one. With no authentication or encryption in place, the attacker uploads a ransomware payload to the bucket. The ransomware then spreads through other misconfigured services connected to the storage, compromising sensitive files. In this case, the shadow IT deployment in the cloud bypassed security oversight, creating an easy attack vector for ransomware to exploit.
Securing Cloud Environments from Ransomware
Cloud environments present unique challenges when it comes to securing against ransomware attacks. The dynamic and distributed nature of cloud infrastructure, combined with complexities like misconfigured identity and access management (IAM), unprotected APIs, and the prevalence of shadow IT, creates a broad attack surface. These vulnerabilities allow attackers to move laterally, escalate privileges, and potentially gain access to critical systems. To effectively combat these risks, it’s crucial to implement comprehensive strategies that limit attackers’ opportunities to spread, exploit excessive privileges, and breach sensitive cloud resources. Below are a few approaches to strengthen cloud security and protect against ransomware threats.
- Microsegmentation: Preventing Lateral Movement
Solution
Microsegmentation is a vital strategy to prevent ransomware from spreading across cloud workloads and services. Unlike traditional on-premises networks, cloud environments require dynamic and flexible microsegmentation that scales with infrastructure changes. By dividing the cloud environment into smaller, isolated segments, you control communication between workloads, limiting the impact of potential breaches.- Isolate workloads based on function, sensitivity, and access needs: This prevents ransomware from easily spreading if one service is compromised, helping to contain the attack.
- Control inter-service communications: Implement strict policies to ensure only authorized services can interact with each other. By restricting unauthorized connections, you reduce lateral movement when one service is infected.
- Dynamic segmentation for cloud-native environments: Cloud workloads scale rapidly and frequently change. A flexible, dynamic segmentation solution automatically adapts to these changes, maintaining security as services scale up or down.
- Enhanced traffic visibility and monitoring: Achieve granular visibility into network traffic across the cloud environment. This enables you to detect and block suspicious activity early, stopping malicious actions before they escalate.
By applying these strategies, you limit the reach of ransomware and protect critical resources from being compromised during lateral movement attacks.
- IAM Misconfigurations and Excessive Privileges
Solution
Excessive privileges are a primary attack vector for ransomware, enabling attackers to escalate their access. Applying the Principle of Least Privilege (PoLP) minimizes unnecessary permissions and prevents attackers from gaining access to critical resources.- Implement PoLP: Regularly review IAM roles and permissions to ensure users only have the access they need.
- Use conditional access policies: Restrict access based on factors such as location, device health, or IP address range.
- Automate access audits: Implement tools that detect misconfigurations in real time, alerting security teams when excessive privileges are granted.
- Leverage federated identity systems: Centralize authentication for consistent access controls across all cloud platforms.
- Securing Cloud APIs and Service Endpoints
Solution
APIs and service endpoints are common entry points for attackers. Securing these interfaces with strong authentication and monitoring mechanisms can prevent unauthorized access.- Apply API rate limiting: Prevent brute-force attacks or misuse by limiting the number of requests to your APIs.
- Enforce strong authentication: Use OAuth, API keys, or mutual TLS for secure API access.
- Utilize Web Application Firewalls (WAFs): WAFs detect and block suspicious API traffic.
- Implement service meshes: Enforce secure communications and encryption between microservices.
- Combating Shadow IT in Cloud Environments
Solution
Shadow IT—unauthorized cloud services used by employees—introduces vulnerabilities that can be difficult to detect. Maintaining visibility across all cloud resources is essential for security compliance.- Use centralized cloud management platforms: Gain visibility over all resources deployed across business units.
- Implement Cloud Security Posture Management (CSPM): Secure and monitor all cloud resources, including those outside approved channels.
- Educate employees: Raise awareness about the risks of using unauthorized services and provide secure alternatives.
- Automated discovery tools: Identify and assess shadow IT resources to ensure they are configured securely.
- Strengthening Cloud Security Posture Through Automation
Solution
Automation helps maintain consistent cloud security and reduces human error. By integrating security throughout the cloud infrastructure process, you can quickly respond to emerging threats.- Automate infrastructure deployment with Infrastructure as Code (IaC): Ensure security policies are integrated from the start.
- Use security automation platforms: Conduct continuous security assessments and automatically remediate issues like misconfigured resources.
- Implement automated backup verification: Ensure data restoration is quick and reliable during a ransomware attack.
- Enhanced Cloud Monitoring and Threat Intelligence
Solution
Real-time monitoring and threat intelligence are crucial for detecting and responding to ransomware attacks in cloud environments. Using machine learning and analytics, you can quickly identify and mitigate threats.- Use cloud-native threat detection tools: Continuously monitor for suspicious activity such as abnormal access patterns or lateral movement.
- Integrate with SIEM systems: Correlate security events across cloud and on-premises environments to gain a comprehensive view of potential ransomware activities.
- Participate in threat intelligence sharing: Stay updated on emerging threats and ransomware techniques to proactively defend your environment.
By employing these strategies, organizations can create a robust, multi-layered defense against ransomware in cloud environments. Microsegmentation plays a pivotal role in preventing lateral movement, while IAM controls, API security, and automation together form a comprehensive protection strategy against a variety of threats.
Conclusion
As ransomware attacks increasingly target cloud environments, we must ask: How secure are we in a system that constantly evolves, where control feels elusive? Are we truly aware of the hidden risks lurking in our cloud infrastructures, waiting to be exploited? In a world where everything is interconnected, what does it really mean to be “secure” in the cloud? The threat is not just about technology—it’s about understanding the complexity of the environment we’re operating in and the vulnerabilities we may be overlooking. Are we prepared for the challenges that lie ahead, or are we underestimating the risks until it’s too late?
Contact us today to learn how we can help secure your cloud environment and guide you through the complexities of today’s cybersecurity landscape.
The post Securing Cloud Environments from Ransomware: A Primer appeared first on ColorTokens.
*** This is a Security Bloggers Network syndicated blog from ColorTokens authored by Devasmita Das. Read the original post at: https://colortokens.com/blogs/cloud-security-ransomware-protection/



