Fake VS Code Extension on npm Spreads Multi-Stage Malware
In a recent discovery, our research team uncovered a fake VS-code extension—truffelvscode—typosquatting the popular truffle for VS-code extension. This extension serves as a trojan horse for multi-stage malware. This blog takes a closer look at how the malicious extension operates, its obfuscation techniques, and IOCs related to this incident.
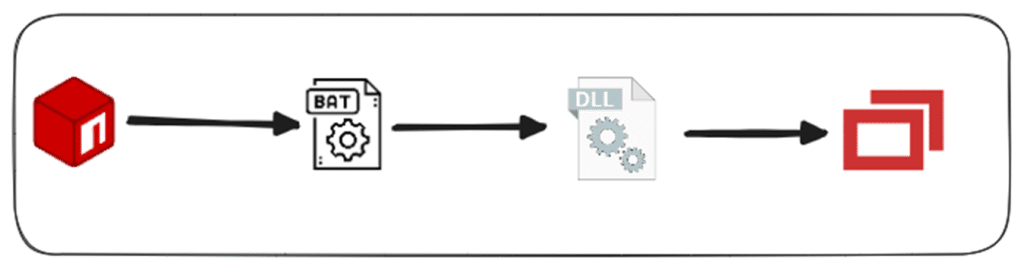
Figure 1. Attack chain
VS code extensions
VS Code extensions are add-ons that enhance Visual Studio Code by adding new features, themes, debuggers, and other integrations. This helps developers customize their workflow, improve code quality, and integrate with tools like Git, Docker, and even AI-powered coding assistants. Extensions are installed from the VS Code Marketplace.
Package analysis
The package was published 5 days ago on Feb 1, 2025. Upon examining the code, the package includes only two files, package.json, and an index.js file. The package.json file looks legitimate with no irregular installation scripts, but it has the same description as the original truffle extension: “Build, debug and deploy smart contracts on EVM-compatible blockchains.”

Figure 2. Legitimate package.json file with the original extension description
Looking at the index.js file, a heavily obfuscated code was revealed. Examining this file a little deeper, and with the help of a deobfuscator tool, we were able to reveal an ‘exec’ command at the end of the file, which connects to an external host for downloading and executing the first stage of the malware.

Figure 3. Obfuscated index.js file with the malicious exec command
The multi-stage attack chain
The attack is structured in several stages, each building on the previous one to eventually provide the attacker with remote control of the compromised system.
Stage 1: Downloading an obfuscated batch file
Upon execution, the obfuscated index.js file initiates a download of an obfuscated batch file. Notably, this batch file is itself obfuscated using the Abobus-obfuscator, a tool that significantly complicates static analysis. The obfuscation not only hides the script’s true purpose but also makes detection and reverse-engineering more difficult for automated analysis tools.

Figure 4. Obfuscated batch file
Stage 2: Executing a malicious DLL
To understand the behavior of this obfuscated batch file, we executed it in an isolated environment. Once executed, we found that the batch file was programmed to download a dynamic-link library (DLL) file using silent powershell WebRequest invocation—the second stage of the malware. After downloading, the batch file immediately executes this DLL, which serves as a critical component in the attack chain and acts as a launcher for the next phase of the infection.

Figure 5. Hidden PowerShell execution, downloading second stage DLL
Stage 3: Installing a preconfigured ScreenConnect client and gaining remote access to the compromised machine
To examine the suspicious DLL, we ran it through the any.run service, an online sandbox for automatically and dynamically dissecting malware behaviors. Looking at the exported report, we immediately saw the goal of this DLL execution: download and run the third and final stage of the malware.

Figure 6. Any.run report, revealing the third stage of the malware
This stage involves downloading and executing a ScreenConnect installer, which is typically known as a legitimate remote desktop application. In our case, after unzipping the installer, in order to get some knowledge on the files it will drop in our machine, we saw a system.config file that contained the preconfigured remote host, port, and encryption key, which will configure the ScreenConnect, to immediately create a connection between the compromised machine and the attacker machine.

Figure 7. ScreenConnect configuration file, preconfiguring the remote host and port
Finally, to prove that the connection was really established, we ran the command “netstat -ano | findstr 8041” and saw that our analysis was successful.

Figure 8. Netstat response proving our analysis
Conclusion
The discovery of the truffelvscode extension points to an alarming trend in software supply chain attacks increasingly targeting developers. By typosquatting, the attackers can distribute multi-stage malware, allowing them remote access to compromised systems. This incident serves as a reminder of the need for caution when installing VS Code extensions, especially those obtained from public package registries like npm.
To mitigate these types of threats, developers and security teams should consider the following.
- Verify package authenticity by checking the publisher details, number of downloads, and user reviews.
- Analyze package contents before installation, especially for extensions with minimal files and obfuscated scripts.
- Monitor network activity for suspicious outbound connections, which could indicate malware execution.
- Adopt automated security scanning tools to detect typosquatting, obfuscation, and malicious dependencies.
As bad actors get more innovative with their tactics, proactive security measures are crucial to prevent software supply chain attacks. Staying informed and leveraging the right security tools can help protect your development environment from similar threats in the future.
*** This is a Security Bloggers Network syndicated blog from Mend authored by Lisa Haas. Read the original post at: https://www.mend.io/blog/fake-vs-code-extension-on-npm-spreads-multi-stage-malware/



