The Difference Between Breach Prevention and Breach Readiness and Why It Matters
At ColorTokens our mission is to help our clients win in the ongoing, dynamic battle against hackers and malicious actors that is being fought 24 hours a day, seven days a week. We wake up every morning knowing that, while we slept, very smart and motivated adversaries have been busy figuring out new ways to breach our client’s critical digital operations. We know that our clients look to us to innovate and continuously improve solutions to help them keep one step ahead of the bad guys in the digital battlespace. We know that a lot depends on the success of our efforts.
Thankfully, we’re not alone. Our brothers in the fight develop solutions that protect the perimeter of the enterprise by trying to prevent breaches; identity & access management, multi-factor authentication, firewalls, anti-virus, Endpoint Detection and Response, encryption, intrusion detection systems, threat intelligence, etc., all aiming to keep malicious actors out. Breach prevention solutions play a crucial role. That’s why businesses have invested so much in them.
But the challenge is that recent history has proven that despite their excellent and necessary technology, breaches continue to occur. Many times, it’s not the fault of the solution; often, in these attacks, the weak link is the human in the chain, perhaps finally succumbing to an MFA prompt bombing at 3:00 AM. The fundamental problem is that in the realm of cyber security, the defender must be successful every single time. The attacker only needs to be successful once.
Our work at ColorTokens is designed to answer our client’s question, “What can we do to be ready to survive the inevitable breach?” They want to be able to continue their critical digital operations despite an attack. Our Xshield Enterprise Microsegmentation PlatformTM stops the lateral movement of ransomware and malware so that the breach does not become a crisis. Because it enforces very granular micro-perimeters within the enterprise landscape, it can isolate critical systems, and quarantine compromised ones. Here’s an analogy: If a home invader breaks through your exterior door, Xshield’s microsegmentation locks the doors between every room and even to the closets and cabinets, limiting what the intruder can damage or steal. That’s why we say that our solution goes beyond breach prevention. It makes your enterprise breach ready.
We encourage you to explore microsegmentation in general, from us or one of the other three leaders in the Forrester Wave for Microsegmentation Solutions (which you can access free of charge here). We sincerely believe that any microsegmentation is better than no microsegmentation.
However, we think we have an approach to implementing microsegmentation that is different and better. Using our unique methodologies of auto-tagging, templatized policies, and progressive incremental enforcement, we can make significant improvements in your security posture in 90 days or less, which is much faster than other solutions. And with our progressive incremental enforcement, you can do it without disruption.
Xshield uses templates to define zero-trust traffic policies for logical segments, as shown in the figure below. For example, templates can be defined for applications and their dependencies, for on-premise or cloud environments or locations, for dev, test and production systems, for internet access, etc. A given network asset can inherit policies from multiple templates.
Importantly, our templatized policy approach also pertains to events that unfold during a breach. It lets administrators configure pre-staged emergency policy templates that can be automatically invoked if there’s a signal that the perimeter defense has been breached (using our open standards-based API integration to SIEM and EDR systems.) That is how Xshield can preferentially isolate systems that are deemed critical, so the attack doesn’t stop the business from operating. That’s an important part of what we mean by being breach ready.
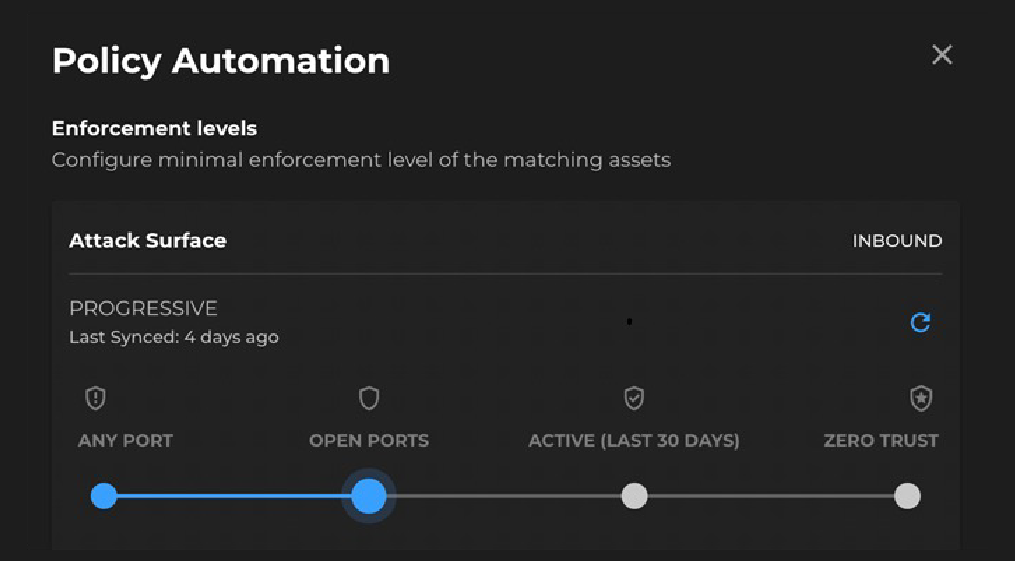
Progressive Test and Enforcement of Policy Templates
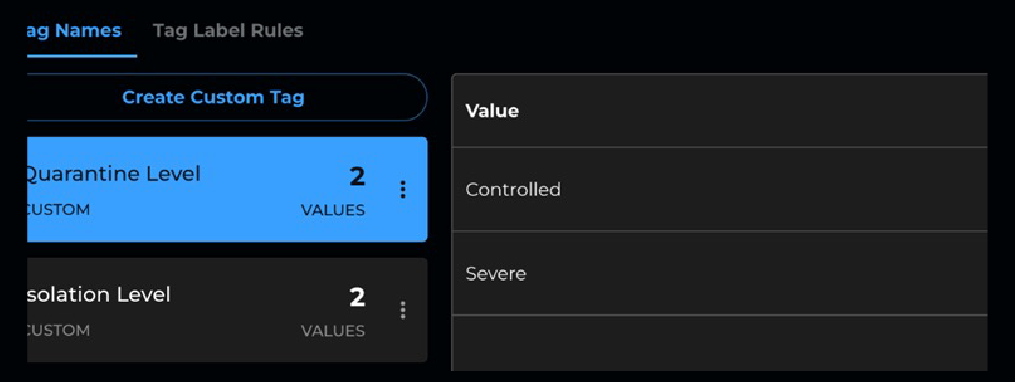
Tagging Assets for Breach Response Policies
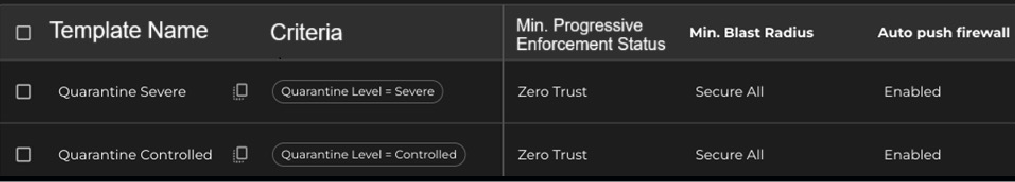
Creating Breach Response Templates
Why being breach ready really matters.
Concerning breach prevention vs. breach readiness, a skeptical CISO might ask, “Is this a distinction without a difference?” Our experience with our customers says, no, it’s not; there are real-world benefits to being breach ready. It changes the course of events in the event of a successful attack. It affects the outcomes for the enterprise, the financial health of the business, the safety and satisfaction of its customers. At a high level, let’s consider the outcomes of a breach, without proactive breach readiness, and with it:
Traditional Incident Response
- Shutdown network, Minimum Business Viability.
- Containment is an expensive technical investment
- 0 to 20% continuity after a cyber attack.
- Withstand losses to the business, then recover.
Breach Ready Incident Response
- No shutdown = Maximize Business Operations
- Attack containment is an inherent capability
- 60 to 80% business continuity during cyberattacks
- Minimal Business loss, progressive business recovery
Implementing ColorTokens’ microsegmentation can make a significant difference in the outcomes of a breach. It changes the nature of the stressful hours the CISO and network security leaders must live through during the progress of the event, and it gives the briefings they must deliver to the CEO and the Board a different tenor. They can describe how the actions they have already taken to be breach ready have reduced the business losses and accelerated the recovery to full operational status. If the breach was a ransomware attack, they can report on how the lateral spread was stopped before the attacker could encrypt their critical assets. I’d say it’s a distinction with a very strong difference.
Contact us to schedule a demo so we can show you how we can deliver this ability for you to have a completely different experience in the event of an inevitable breach. www.colorTokens.com/contact-us.
The post The Difference Between Breach Prevention and Breach Readiness and Why It Matters appeared first on ColorTokens.
*** This is a Security Bloggers Network syndicated blog from ColorTokens authored by Bob Palmer. Read the original post at: https://colortokens.com/blogs/breach-readiness-enterprise-security/



