Oasis Security Details MFA Security Flaw Found in Microsoft Cloud Services
Oasis Security today revealed that it worked with Microsoft to fix a flaw in its implementation of multi-factor authentication (MFA) that could have been used by cybercriminals to gain access to every major Microsoft cloud service
Tal Hason, a security researcher for Oasis Security, said services such as Azure, Office 365 and OneDrive were all vulnerable to the same type of brute force attack.
That attack specifically exploited the way Microsoft implemented identity verification after a user was assigned a session identifier. After typing a valid email and password, users are asked to further verify their identity, Microsoft supports a variety of MFA methods, including a verification code from an application. Using such an application, users type in the six-digit code to complete their authentication. Up to 10 consequent failed attempts were allowed for a single session.
By rapidly creating new sessions and enumerating codes, the Oasis research team demonstrated a very high rate of attempts that would quickly exhaust the one million potential options for a 6-digit code, all of which could be executed simultaneously. Microsoft, like many other providers of service, relies on RFC-6238 guidelines to implement authentication.
RFC-6238 suggests a different code be generated for each timeframe of 30 seconds, and most apps and validators. However, due to potential time differences and delays between the validator and the user, the validator is encouraged to accept a larger time window for the code. That means a single authentication code may be valid for more than 30 seconds. The Oasis Security Research testing showed a tolerance of around three minutes for a single code, extending 2.5 minutes past its expiry, allowing 6 times more attempts.
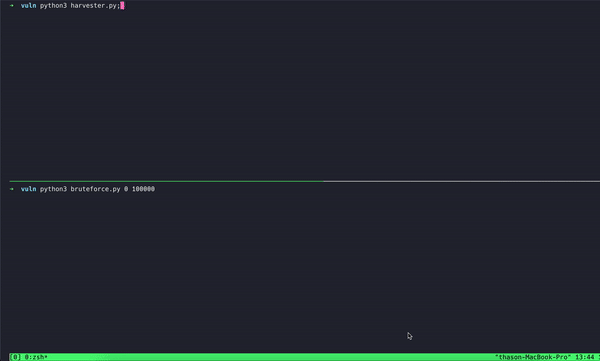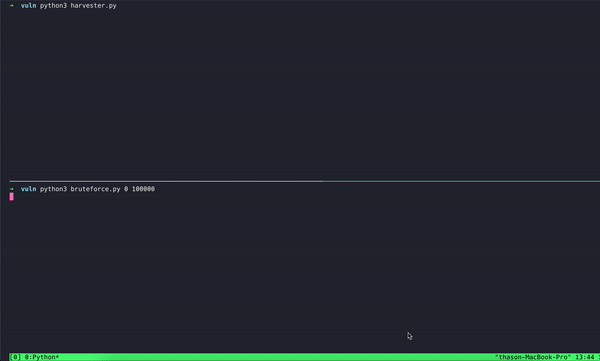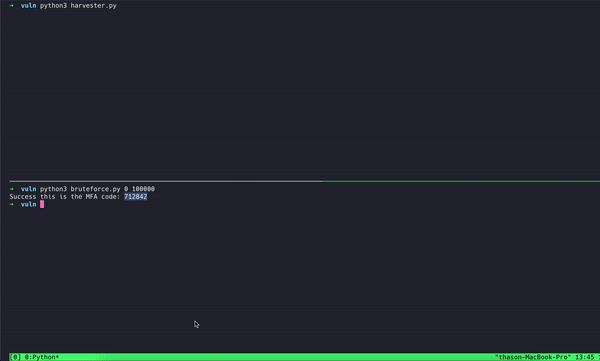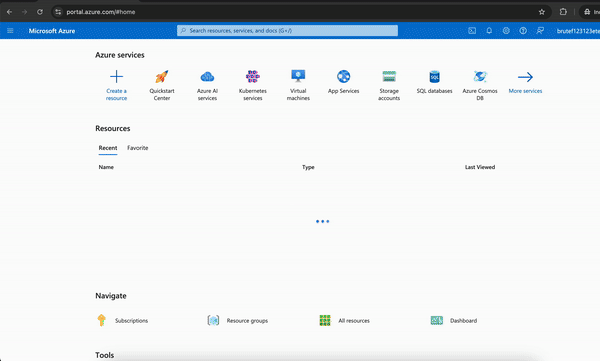
Given the allowed rate, researchers had a 3% chance of correctly guessing the code within the extended timeframe. A malicious actor would have been likely to proceed and run further sessions until they hit a valid guess. The Oasis Security Research team did not encounter any issues or limitations in testing that vulnerability. After 24 such sessions, requiring about 70 minutes, a malicious actor would already pass the 50% chance of hitting a valid code.
Additionally, more codes could have been sent within that timeframe which might have made other code guesses valid.
Ultimately, bypassing MFA took Oasis researchers about an hour to execute, required no user interaction, and did not generate any notification or provide the account holder with any indication of trouble.
Microsoft has since added a much stricter rate limit that once triggered lasts for half a day after several failed login attempts are detected.
It’s not clear how many other cloud services might be prone to the same type of brute force attack, given Microsoft’s dependency on the RFC-6238 guidelines. Organizations should not abandon MFA but they should review how it’s been implemented, said Hason.
There is, of course, no such thing as perfect security, and even as more MFA flaws are discovered it’s still a lot better security alternative to traditional user names and passwords, that are even more easily compromised