What Are Living Off the Land Attacks?
In the physical world, “living off the land” simply means to survive only by the resources that you can harvest from the natural land. There may be multiple reasons for doing this — perhaps you want to get “off the grid,” or maybe you have something or someone to hide from. Or maybe you just like the challenge of being self-sufficient.
In the technology world, “living off the land” (LotL) refers to attacker behavior that uses tools or features that already exist in the target environment. In this multi-part blog series, we’ll explore why attackers use LotL, review a selection of the tools and features they use, and discuss examples of actual LotL attacks. We’ll also provide some guidance for detecting and preventing some of the commonly used approaches.
Why Attackers Live off the Land
Let’s start with why attackers use tools that already exist in the environment to execute plan an attack. Attackers may be motivated by one or many of the following reasons:
1. Fly Under the Radar/Avoid Detection
Attackers may choose to fly under the radar of either prevention or detection technologies. Typically, prevention technologies will use a signature-based approach to detect and quarantine malicious processes. They may also use hash values or other indicators of comprise (IOCs) to detect a process.
While attackers can change indicators of compromise (IOCs) relatively easily (see The Pyramid of Pain), using pre-existing software avoids the process being flagged as suspicious. It also saves the attacker cycles in developing the binary to deliver an attack.
The Pyramid of Pain
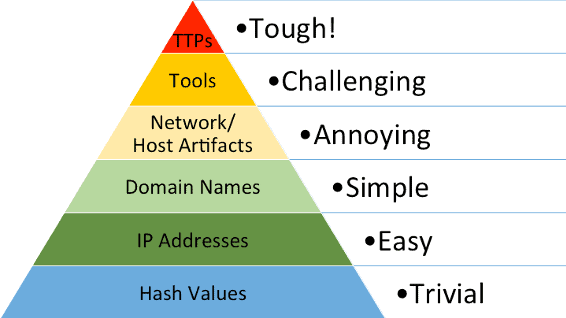
Figure 1: The pyramid of pain represents the difficulty level for attackers to change indicators that a defender might use to detect their activity.
2. Use Power Tools Already Embedded in Operating Systems
Operating systems typically carry tooling for automation and scripting administrative activities. Windows PowerShell is a good example. Every Windows OS since November 2006 includes PowerShell. This makes it a pervasive tool in a typical enterprise environment. These tools will typically provide easy access to both local and domain-based configuration. For example, with PowerShell, you can configure anything from Active Directory objects to local raw disks.
3. Tooling Can be Difficult to Develop and Distribute
Typically, an attacker will scope out a target, but he or she may not know the entire environment the tools operate in. This creates some hurdles for building, compiling, and testing program. These tools should allow for a variety of operating systems and environments, and it may be difficult, if not impossible, to test for every possible scenario.
Why Attackers Use Existing Tools to Execute Attacks
Attackers that use already existing tooling avoid the need to build, test, and QA tools. They don’t have to worry about compatibility, dependencies, and so forth. It’s also challenging to build programs that are stealthy enough to avoid detection, particularly if something runs at kernel level. Ultimately, it’s probably cheaper and quicker to use existing tooling.
From an attacker’s perspective, using already existing tools and features makes the defender’s job inherently more difficult. Picking out the malicious use of built-in tools versus the authorized use of tools by the system administrator can be somewhat like looking for a needle in a haystack.
Unveiling the Complexity of Stealth Cyberthreats
The challenge is further complicated by the hackers’ ability to infiltrate U.S. infrastructure with remarkable stealth, exploiting vulnerabilities and utilizing the organization’s own tools against it. This level of sophistication not only highlights the potential for significant disruptions and damage but also brings to light the considerable obstacles in detecting and mitigating such threats. The use of LotL techniques enables the prolonged presence of these adversaries within target environments, and this combined with their skillful exploitation of tools and vulnerabilities, magnifies the complexity of defending against these cyberthreats. As a result, organizations are forced into a continuous cycle of adapting and enhancing their cybersecurity strategies to protect their critical assets and infrastructure effectively.
This escalating situation has profound implications for cybersecurity practices. The adept use of stealth tactics by hackers, particularly through LotL attacks, presents significant challenges in detecting and responding to malicious activities within network environments. Traditional security measures often struggle to identify such techniques, which are fundamentally designed to evade detection. Furthermore, the immense volume and diversity of data generated in complex networks can overwhelm security teams, complicating efforts to sift through information and pinpoint suspicious activities. Additionally, network fragmentation and the potential for insider threats or credential abuse introduce further complexities, creating blind spots that make it difficult to differentiate between legitimate and unauthorized activities.
Strategize a Proactive Cybersecurity Defense Against LotL Attacks
In response to these challenges, organizations should review their threat detection and incident response (TDIR) strategy. The prevalence of LotL attacks necessitates maturing already existing defense strategies and leveraging automation, machine learning, and behavioral analytics, to enhance their TDIR capabilities. By adopting such forward-thinking strategies, organizations can anticipate and adapt to emerging threats, as well as gain the upper hand against adversaries, improving their ability to detect and neutralize threats in real-time.
Key to protecting against LotL attacks are six foundational actions that serve to fortify defenses, improve detection capabilities, and streamline incident response mechanisms. Each of these six actions play a crucial role in building a robust cybersecurity framework capable of withstanding bad actors:
- Prioritize Visibility: Organizations must prioritize the implementation and ongoing improvement of a comprehensive TDIR process. This strategy ensures comprehensive visibility across the entire digital landscape of an organization, encompassing network traffic, endpoint behavior, and user activity. By actively monitoring these facets, security teams can detect anomalies that deviate from normal operations, which are often indicative of LotL attacks. Enhanced visibility aids in the early detection of such threats and enables a more nuanced understanding of the organization’s security posture, facilitating the identification of attacks early in the kill chain, and enabling timely response.
- Enable Comprehensive Logging: The intricacy of LotL attacks also necessitates the establishment of granular logging mechanisms. These mechanisms are designed to meticulously track the usage of LotL tools, including those embedded within operating systems like PowerShell scripting. By enabling extended logging features, organizations can gather detailed insights into the execution patterns and command sequences of these tools, offering a clearer picture of potentially malicious activities. This level of logging provides a rich dataset from which security teams can identify unusual patterns, supporting the swift identification and mitigation of threats posed by sophisticated attackers.
- Leverage Advanced Tools: Deploying advanced endpoint monitoring tools is also an essential step. These tools offer deep visibility into the granular activities occurring on endpoints, extending beyond simple log analysis to include behavioral analytics and anomaly detection. Such tools are instrumental in identifying and responding to suspicious behavior that could signal ongoing LotL activity. Leveraging the capabilities of advanced endpoint monitoring empowers security teams to stay ahead of attackers, safeguarding the organization’s assets against threats.
- Leverage User & Entity Behavioral Analytics: These tools can analyze and create a baseline of typical user and entity activities over a time period, providing a basis for surfacing deviations from normal behavior. This provides a valuable additional dimension of visibility enabling deviations in behavior to be correlated with other indicators of compromise.
- Continual Review of Detections: Cybersecurity is not a point in time project, but rather an ongoing journey of reducing risk. Fine tuning of detection capabilities based on environment and risk appetite is an important element of protecting against ever evolving threats and increasingly stealthy tactics.
- Adopt Zero Trust Architecture: Moving towards a Zero Trust security model can be a game-changer in combating LotL and other sophisticated cyberattacks. In a zero-trust architecture, no entity, whether inside or outside the network, is automatically trusted. Instead, every access request is thoroughly verified before granting access. This approach minimizes the attack surface by enforcing strict access controls and segmenting networks, thereby limiting the movement of an attacker within the system.
Adapting to the Digital Landscape
The imperative need for a proactive cybersecurity stance is critical, as it involves safeguarding critical infrastructure and protecting sensitive data from the clutches of state-sponsored and other sophisticated cyber adversaries. Organizations must strive to stay one step ahead by integrating advanced detection tools and strategies, such as prioritizing visibility, enhancing logging practices, and embracing a zero-trust architecture. These measures enable improved detection and response to stealth attacks, ensuring the resilience and protection of vital assets against the cunning maneuvers of global cyberthreat actors. Ultimately, the key to resilience in the digital battlefield lies in the ability to anticipate, act decisively, and continually adapt, leveraging every technological and strategic advantage to ensure the security and integrity of our digital world.
Interested in learning more about how to combat LotL attacks? Look for upcoming blogs that will surface some techniques that you can use to reduce the size of the haystack and help find those needles. One of the interesting things with combating LotL attacks is that you can begin to see the tactics techniques, and procedures (TTPs) that a particular attacker uses. Once you can detect TTPs, it becomes a bigger challenge for the attacker to change, rather than just changing a hash value to avoid detection.
In our next blog post, we’ll take a look at Windows Scheduled Tasks through the lens of living off the land. It’s a pervasive tool in Windows Operating systems, and a favorite among threat actors.
Subscribe to our Blog Newsletter
The post What Are Living Off the Land Attacks? appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by LogRhythm. Read the original post at: https://logrhythm.com/blog/what-are-living-off-the-land-attacks/



