Harnessing Virtues of the PAM Triad for Robust Digital Security

In the ever-evolving realm of cybersecurity, two key players stand firm to safeguard organizational assets: Privileged Access Management (PAM) and Multi-Factor Authentication (MFA). These aren’t just fancy tech terms, but crucial shields that protect your digital domain. Let’s break them down into simpler terms before we dive into how our Excalibur PAM embodies these principles to offer a fortified defense.
PAM is all about who gets the keys to the kingdom. It helps manage and monitor privileged user access, ensuring that only the right people get high-level permissions and that their actions are watched over. Think of it as a vigilant gatekeeper, letting in only the trusted, and keeping a close eye on them.
On the other hand, we have MFA, depicted as a vigilant guard standing at the gates, demanding multiple proofs of identity before granting entry. It’s like having a guard that requires a secret password, a trusted emblem, and a unique trait before allowing passage.
Combining the vigilant gatekeeper (PAM) and the meticulous guard (MFA) creates a robust defense line. This duo significantly minimizes the risk of unauthorized access, forming a strong barrier against a multitude of cyber threats.
As we draw the curtains on our medieval allegory, let’s transition into the modern-day technical fortress that is our Excalibur PAM. In today’s post, we will begin by taking a brief tour of how Excalibur PAM encapsulates the core components of PAM and MFA to bolster security. As we delve deeper into our upcoming posts, we’ll transition from the castle’s battlements to the blueprint, unveiling the overall design that constructs this digital stronghold. This exploration will pave the way to understanding the state-of-the-art mechanisms that stand guard over your organizational assets, ensuring a secure and resilient operational environment.
What is PAM?
In the context of Information Technology, the term privilege refers to the level of authority granted to a user account or process. This authority allows one to override certain security restrictions and perform actions such as system shutdowns, loading device drivers, configuring networks or systems, and more. The misuse or abuse of such privilege, whether accidental or malicious, poses a significant security risk for organizations.
The assignment of privileges can vary across different systems and may be based on role-specific attributes or other factors such as seniority or time of day. Privileged accounts, often known as superuser accounts, are typically used for administrative purposes. In Unix/Linux systems, these accounts are often referred to as “root” accounts, while in Windows systems, they’re called “administrator” accounts. With a wide range of authority, these accounts can execute commands and have unrestricted access to files, directories, and resources.
Given their extensive authority, privileged accounts are particularly attractive targets for external attackers. Seizing these credentials grants intruders rapid access to organizations’ most critical systems and sensitive data and once acquired they allow hackers to morph into “insiders,” easily masking their tracks while navigating through the compromised IT environment.
This scenario highlights the serious security risks associated with privileged accounts, emphasizing that effective governance is key to enhancing cybersecurity. It’s crucial for IT and security teams to have tight control over access to these privileged accounts, credentials, and secrets to mitigate risks and reduce vulnerabilities. In this ongoing battle, PAM solutions play a critical role, reducing risk by improving visibility and control over privileged account credentials, isolating privileged sessions, and auditing privileged activities. This proactive approach fosters a more secure digital environment, strengthening defenses against potential security breaches.
In the remaining sections of this blog post, we will introduce the key advantages of PAM and explain how these advantages are not only implemented but significantly enhanced in Excalibur, leading the way toward a stronger cybersecurity posture for your organization.
Advantages of implementing PAM
While PAM solutions may vary in their approaches, at a minimum, they should enhance cybersecurity and provide protection against cyber-attacks in the following ways:
Reduce Attack Surface and Damage
The potential for cybercriminal attacks diminishes significantly when most employees, processes, and apps lack access to the sensitive data targeted by criminals. A hacked laptop belonging to a junior employee presents minimal value to a cybercriminal, with the damage confined to the data accessible by that employee. Through PAM, attackers are compelled to target privileged accounts to achieve a substantial illicit gain.
In Excalibur, the principles of privileged access management and zero-trust seamlessly blend, as there’s no necessity to trust the client since nothing is installed on it, with all access being facilitated via a browser. This arrangement prevents the client machine from accessing the internal network, thereby inhibiting the spread of viruses, malware, ransomware, and the like.
The distinctive shift brought about by Excalibur lies in its security perspective, implemented through a twofold approach.
On one hand, even if a single Excalibur component is fully compromised, the overall system functionality remains intact. This resilience is achieved through a distributed storage of credentials using an XOR random scheme, which ensures the protection of data at rest, alongside a distributed Public Key Infrastructure (PKI) scheme that enables the verification of the authenticity of each action and event in a decentralized manner. Every action requires signature and verification by multiple distinct components, which means that even if the Excalibur Server were to be entirely compromised, an attacker would be unable to gain access to any Client or impersonate any Token (you can check here for more details).
On the other hand, the connection to the internal (protected) network is done via a Tunnel Resolver Component (or TRESK). TRESK is one of the core components of Excalibur which allows access to any target inside the Intranet with almost zero infrastructure or policy (re)configuration.
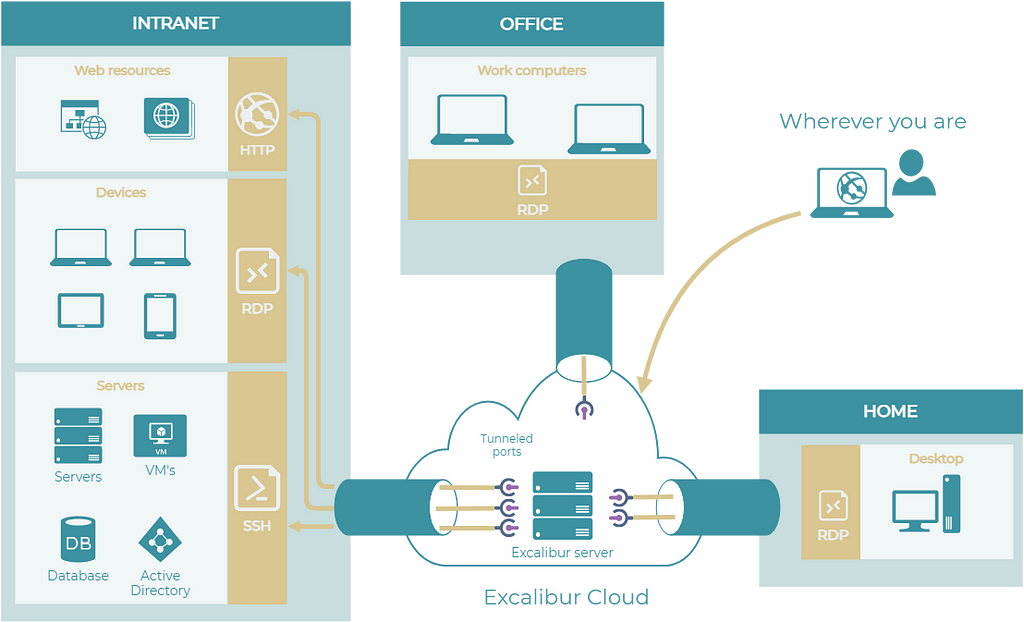
TRESK is composed of several components situated both in the cloud and on the customer’s premises. In the cloud resides the TRESK server, while on-premises houses the TRESK virtual machine (or TRESK-VM) and client (or TRESK-Client). The TRESK-Server serves as an endpoint for initiating SSH tunnels by TRESK-VM or TRESK-Client, managing necessary actions for successful SSH tunnel establishment, such as creating temporary users with the corresponding public/private key pair authentication. Conversely, the TRESK-VM facilitates access to target systems from the TRESK-Server side, as these targets are typically unreachable from the cloud environment.
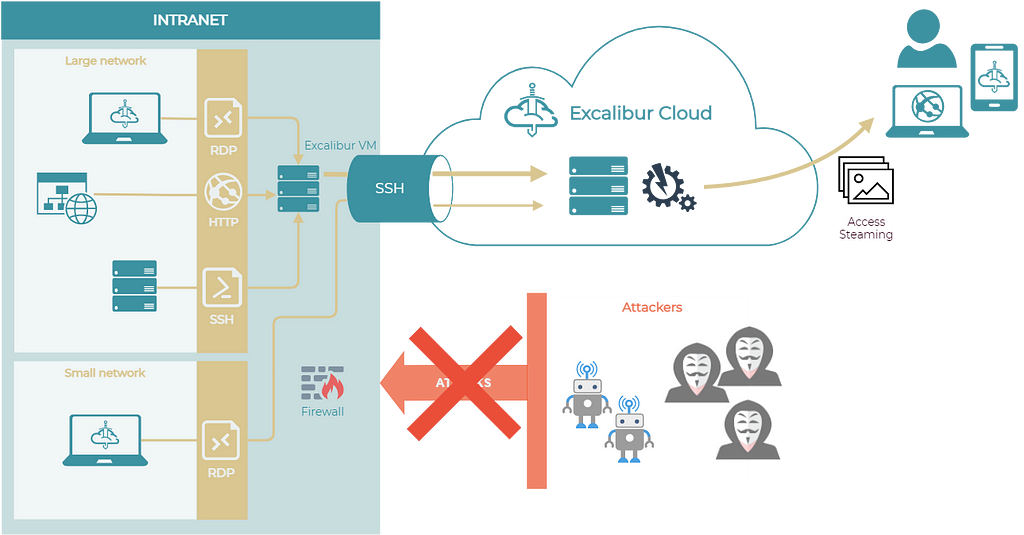
Our TRESK component has been designed to entirely eliminate any direct access to the protected resources. “Direct access” is the foremost and most perilous entry point into a system as it allows attackers to exploit known or unknown vulnerabilities of all exposed services. By narrowing down the access to the internal network to only one method, we almost entirely eradicate such a problem. Unlike alternative solutions employing overlay networks like P2P, which still provide direct access and consequently do not resolve issues of exploitation, ransomware, and similar attacks enabled by direct access, TRESK meticulously addresses these security concerns. You can read more about our TRESK approach in this whitepaper.
Password Protection
Even if a malicious actor manages to infiltrate a system, employing password vaults adds a layer of protection by securely storing encrypted usernames and passwords. Many PAM systems come with features such as automatic password generation, routine password updates, and credential verification procedures. These functionalities ensure that passwords remain dynamic and monitored, minimizing the chances of misuse. Consequently, if a cybercriminal acquires privileged credentials, their capability to exploit the compromised account is significantly curtailed. Notably, the malicious actor is prevented from altering their own or others’ passwords to enact ransomware-like scenarios, or from leaking and/or sharing these passwords, thanks to the secure containment and controlled access provided by the password vaults.
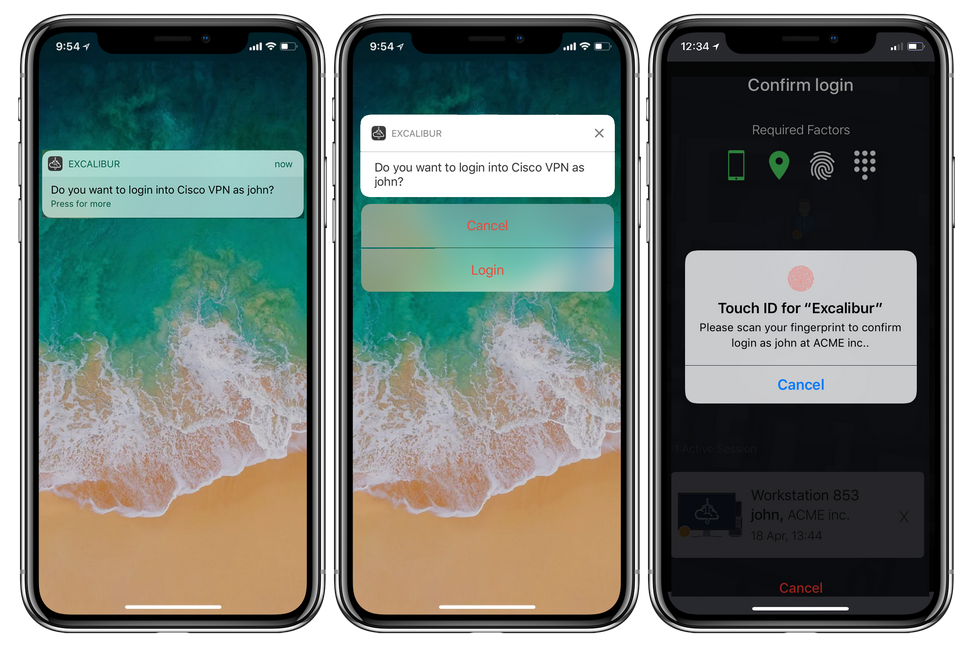
Excalibur not only encompasses the aforementioned features but advances well beyond them with a core innovation: thwarting all attacks on credentials by automatically generating a new password at each login. In the Excalibur user flow, the traditional password entry is bypassed; users no longer need to know or enter a password. Instead, a random string is generated in the background and seamlessly integrated into the login process by Excalibur. Moreover, with Excalibur’s passwordless approach, user authentication adheres to a zero-trust model. Access is closely tied to a user’s smartphone (representing an ownership factor), location such as a branch office (location factor), a Personal Identification Number (PIN) code (knowledge factor), and ideally, a form of biometry like on-device biometric sensors or facial recognition via a front-facing camera. Thus, even if a malicious user manages to log into the system, there’s no avenue for them to steal or leak credentials for future access.
For a scheme of this nature to function seamlessly, where user interaction is minimized and automation is central, compatibility is crucial. Excalibur is designed to support all major platforms and authentication protocols, ensuring a smooth integration across a broad spectrum of systems. However, there might be instances where legacy applications necessitate custom integration. To address such scenarios and facilitate a gradual rollout, Excalibur offers the feature of displaying a randomly generated one-time password (OTP) post successful authentication on demand. This provision ensures that even if there are systems not yet supported by Excalibur, users can simply copy a displayed OTP for access, which will be altered post-use. Given the transient nature of the OTP, any attempt to steal it becomes futile, maintaining the security integrity of the system. Here you can find more information about all the ways in which we use OTP within Excalibur.
Track & Monitor Privileged Activity
Having traversed the realms of minimizing attack vectors and fortifying password protection, we now steer our focus toward the equally pivotal domain of tracking and monitoring privileged activities. Central to most PAM systems is the vigilant oversight of all privileged access and actions, with logs maintained to meet audit and compliance standards. This monitoring and recording capability amplifies cybersecurity by identifying abnormal access patterns or unforeseen privilege escalations. For instance, log records could expose suspicious activities, like a privileged SSH connection initiating from a distant location at an unusual hour like 3 AM.
Excalibur PAM distinguishes itself by offering controlled access to a vast array of services, servers, and applications, courtesy of its support for a broad range of protocols. These applications are accessible through any web browser supporting HTML5, extending this accessibility even to mobile web browsers.
The cornerstone of Excalibur PAM’s access control is the whitelist approach, which, from a security viewpoint, stands superior to blacklisting. Whitelisting permits only predefined, authorized entities to access the resources, establishing a default-deny security posture. This proactively ensures that only known, trusted entities gain access, contrasting with blacklisting’s default-allow posture which could potentially allow unknown threats to slip through. Clients are barred from direct access to the protected resources; access is channeled solely through Excalibur PAM, following a robust multi-factor authentication, as illustrated in the Excalibur Dashboard below.
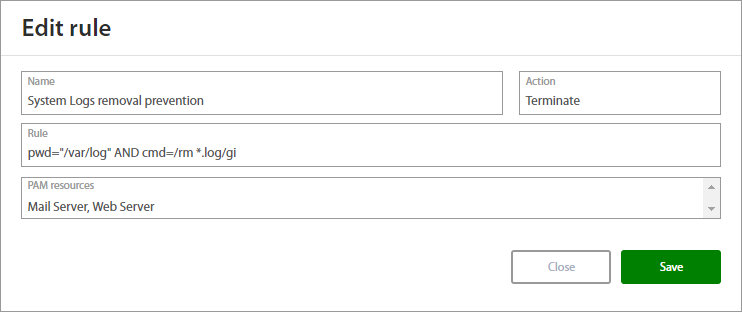
Beyond monitoring, and as shown above, Excalibur PAM extends its expertise to reacting to anomalies by terminating them in a seamless and automatic manner (you can get more information about Excalibur anomaly detection here). It’s not merely a passive observer but an active responder to potential security threats. Administrators have the latitude to define the responsive action — be it session termination, notification, or other predefined actions, ensuring an adept reaction to any irregularities.
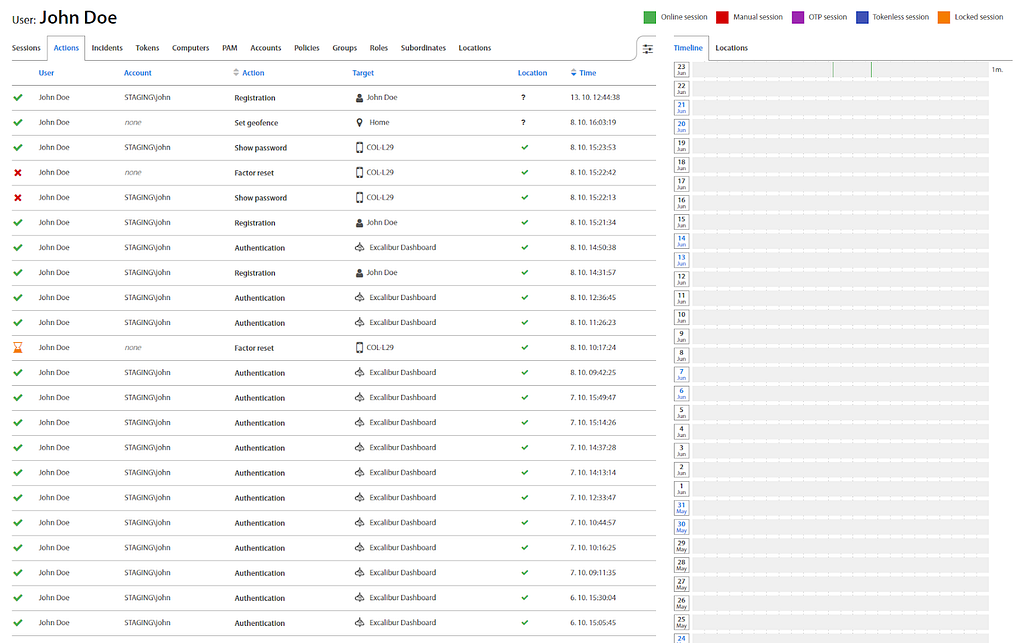
In the Excalibur PAM ecosystem, all sessions are deemed “privileged” and are recorded by default. Every action undertaken by the user is cryptographically signed to verify its authenticity from the authenticated user. This setup ensures a continuous correspondence of every user action, as each action and PAM session is documented and cryptographically verified, aligning with the strongly multi-factor authenticated identity (see picture below for an example and the Excalibur documentation to see all the factors that can be used), thereby eliminating any room for access delegation or impersonation.
The Excalibur Dashboard serves as the conduit for users to access enterprise resources allocated to them via PAM, review their activity, scrutinize the security policy assigned to them, and manage their temporary or home locations. Administrators are granted full access to all sections of the Excalibur Dashboard, empowering them to orchestrate and manage all facets of its functionality, ensuring a seamless and coherent operational experience. An example of a dashboard panel with all the recent activities from users can be seen in the below screenshot.
In conclusion
In this blog post, we have embarked on an exploration of three fundamental properties of PAM such as attack vector reduction, password protection, and monitoring of privileged activities, among others. We have showcased how these core properties have been meticulously implemented and, in some instances, enhanced in Excalibur. However, we have only provided an overview of these implementations without delving into the intricate implementation details. For a deeper understanding and technical insights into how Excalibur embodies these PAM properties, you can read more on the online Excalibur documentation. This narrative serves as a primer to grasp the robust security framework Excalibur offers, paving the way for a fortified cybersecurity posture.
*** This is a Security Bloggers Network syndicated blog from Stories by Excalibur on Medium authored by Excalibur. Read the original post at: https://medium.com/@xclbr/harnessing-virtues-of-the-pam-triad-for-robust-digital-security-e817ed73c2b5?source=rss-c33ef172a8fe------2



