“Web Skimming Attacks – Digital Hacking Techniques for Payment Card”
Introduction
A recent notion, Web Skimming attacks, which have been around for a while, was introduced with the rise in cyber threats. After the Magecart attack on British Attacks in 2018, they were created. In mitigation efforts, GDPR violations fines, and other payoffs related to this Magecart assault, the corporations spent $1 B. Web skimmers and Magecart scripts are being strategically inserted by cybercriminals to be appended to Javascript libraries as graphics, logos, and favicons.
Are you aware that they are most frequently found on e-commerce, banking, finance, healthcare, travel, and other service platforms, which is a big concern? Yet, we must be familiar with the notion of Web skimming attacks before delving into its specifics. The CISOs and CIOs are reevaluating their security strategies due to this incident. So let’s investigate this global phenomenon in more detail.
Web Skimming Attacks
Web skimming attacks, also known as digital skimming attacks, are described as hacking techniques in which the attacker compromises the payment or checkout pages of the websites by injecting malware through third-party apps that are used by the website. By manipulating unsecured and infected client-side web applications, they attack the digital industry.
Web skimming attacks are a rising source of worry for both consumers and organizations. As these hazards are directly related to sensitive data, it is crucial to be aware of them.
The well-known hacking gang called “Magecart” is known for its use of web-scraping assaults. Even though the e-commerce industry and other payment sectors that collect customer billing information are growing, the Magecart attacks are typically overlooked in the field of security.
How do Web Skimming Attacks work?
Let’s walk into the process of Web Skimming attacks or rather see how these web skimming attacks work. Below is the step-by-step guide to show how Web Skimming Attacks work.
- Gain Access – Under this, the attackers access the websites in the first and most crucial phase. In order to achieve this, they can either breach into the server or infrastructure and install a skimmer there, or they can identify the weak points in your third-party providers.
- Data Collection – In order to avoid detection, dangerous code is typically hidden behind seemingly innocent-looking other code. Skimmers always employ some form of JavaScript that listens to and gathers private data.
- By Pass Sensitive information – After the hackers have obtained critical information through your website, they are prepared to transfer it to their own servers.
“An incident involving British Airlines in 2018 resulted in the compromising over 380,000 credit card details, including names, addresses, bank card information, and CVV codes for 5,000 customers.“
Few Attacks Exploited
- Java Script Injection Attacks – This involves inserting malicious code into a website’s JavaScript code, which can be used to steal sensitive information, such as login credentials and credit card details.
- Drive-By Skimming Attacks – These occur when a user visits a website that has been compromised with malicious code, which then captures their data as they enter it into the website’s form fields.
- Sideloading and chain-loading Attacks – It involves using legitimate software or plugins to introduce malware onto a user’s device, which can then be used to capture sensitive information.
- Trusted cloud-hosted skimming Attacks – They occur when attackers gain access to cloud-based services, such as web hosting or content delivery networks, and use them to inject malicious code into websites.
- Public Wi-Fi Skimming Attacks – Public Wi-Fi skimming attacks take advantage of unsecured public Wi-Fi networks to intercept and steal data being transmitted between a user’s device and the internet.
- E-commerce Skimming Attacks – E-commerce skimming attacks target online stores, with attackers injecting malicious code into the checkout pages to steal credit card details and personal information.
- Self-cleaning and Stealth Data Skimming Attacks – They are designed to be difficult to detect, with the malicious code automatically removing itself after stealing data or hiding its presence on the website.
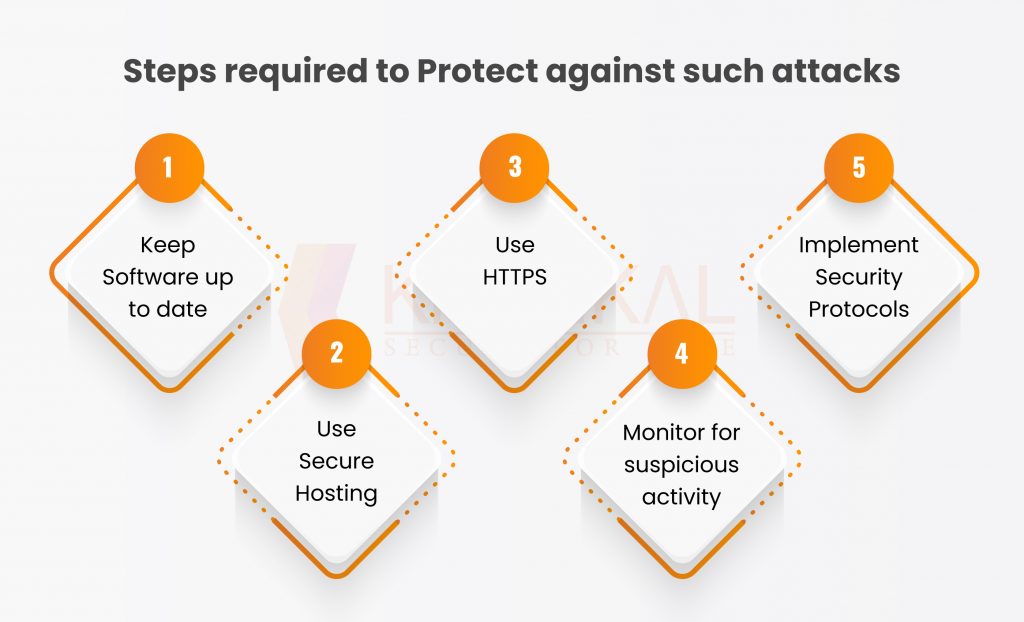
Steps required to Protect against such attacks
To protect against web skimming attacks, website owners should take the following steps:
- Keep Software up to date: Regularly update the software and plugins used on the website to address any known vulnerabilities.
- Use Secure Hosting: Choose a secure hosting provider that provides encryption and other security measures to protect against attacks.
- Use HTTPS: Use HTTPS to encrypt the data transmitted between the customer’s browser and the website.
- Monitor for suspicious activity: Regularly monitor the website for any suspicious activity, such as changes to the code or unusual traffic patterns.
- Implement Security Protocols: Implement security protocols such as two-factor authentication and limit access to sensitive areas of the website.
By taking these steps, website owners can help protect their customers from the devastating effects of web skimming attacks. It’s important to stay vigilant and up to date on the latest threats to ensure that your website is secure.
Safeguarding your Payment through Kratikal
Attacks on e-commerce websites known as “web skimming” are on the rise and pose a serious risk to both businesses and customers. Businesses can lower the risk of web skimming attacks and safeguard sensitive client data by adhering to the best practices described above. Also, organizations should periodically assess and upgrade their security procedures to stay on top of the threats because web skimming attacks are continuously changing.
To protect an organization’s IT infrastructure, Kratikal, a CERT-In-empanelled provider of cyber security solutions, offers a full range of VAPT services, including Network Penetration Testing, Application Penetration Testing, Cloud Penetration Testing, and many others. Kratikal provides security auditing services for Compliance in addition to testing services.
Please don’t hesitate to get in touch with us if you’re interested in hardening your anti-skimming defenses and automating your client side security operations. For more information, look at Kratikal’s VAPT and Compliances services.

The post “Web Skimming Attacks – Digital Hacking Techniques for Payment Card” appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Deepti Sachdeva. Read the original post at: https://kratikal.com/blog/web-skimming-attacks-digital-hacking-techniques-for-payment-card/




