Palo Alto Networks Unfurls OT Security Service
At the Mobile World Congress event, Palo Alto Networks today launched a service for securing operation technology (OT) assets that is based on the same core technologies it relies on to secure IT environments.
Xu Zou, vice president for network security as Palo Alto Networks, said the Zero Trust OT Security service will also make it simpler for OT and IT teams to effectively collaborate as the overall size of the attack surface that needs to be defended within many organizations continues to expand.
Palo Alto Networks previously added offerings based on its firewalls and secure access service edge (SASE) platform for securing endpoints in vertical industries such as health care. The latest addition to the portfolio is designed to be applied more broadly, said Zou.
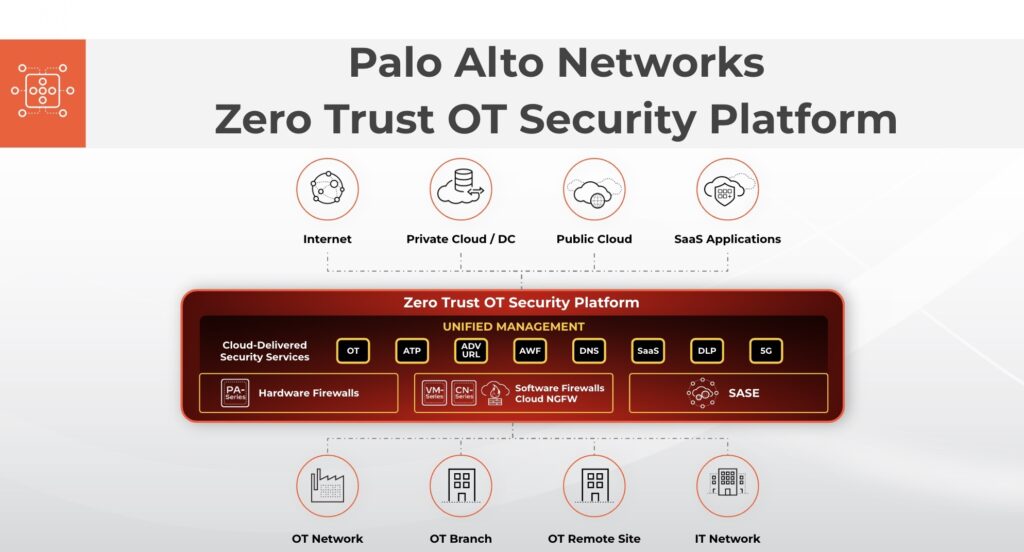
At the core of the Palo Alto Networks OT service are next-generation firewalls embedded within the company’s SASE service and an internet-of-things (IoT) security and management platform that it gained with the acquisition of ZingBox in 2019. The service recognizes hundreds of unique OT device profiles and more than 1,000 OT/industrial control system (ICS) applications and has hundreds of unique OT threat signatures. Palo Alto Networks also employs a security engine infused with machine learning algorithms, application fingerprinting tools and crowdsourced telemetry data.
That approach enables a zero-trust IT environment to be created with a single click to microsegment networks and enforce least-privilege access policies across both 4G and 5G networks, noted Zou.
As more OT platforms are connected to the Internet, they are being increasingly targeted by cybercriminals who are looking for way to exfiltrate data and create backdoors through which malware can then be laterally spread through an organization. Unfortunately, many OT teams lack the expertise required to secure those platforms, so they are increasingly looking to internal IT teams for assistance. The Zero Trust OT Security service provides a framework for fostering that collaboration because many organizations already rely on Palo Alto Networks to secure their IT environments, noted Zou.
At the same time, cybersecurity teams gain access to a centralized cloud platform through which security policies can be applied across what is rapidly becoming a highly distributed computing environment. That’s critical as organizations continue to struggle with finding and retaining cybersecurity personnel, especially the limited number that might have any OT security experience.
It’s also apparent that many of these platforms are in places that are not readily accessible so relying more on some type of service to secure them is all but inevitable for most organizations. The issue now is determining to what degree internal cybersecurity teams want to co-manage that task versus relying completely on some type of managed service.
Regardless of the approach, OT security is only going to become more challenging in the months ahead. Many of the OT security decisions that organizations make are likely to reverberate for years to come. In many cases, the better part of valor may be to opt for an approach that provides as much flexibility as possible in terms of who might be responsible for managing and securing OT environments both today and into the future.