Hunting Emotet Made Easy with EclecticIQ Endpoint Response

Earlier this year, EclecticIQ Analysts published this article detailing the inner workings of a newly observed Emotet variant. In November, another industry source published a report talking about the resurgence of Emotet after a hiatus. The report describes how Emotet is activated after remaining dormant to obfuscate the infection. The report also says that “Once downloaded, the malware will quietly run in the background while connecting to the Command and Control server for further instructions or to install additional payloads”. This implies that it is indeed possible for Emotet infections to exist, but to act as ‘sleeper cells’ waiting to be activated. Once again, we see similar techniques in play; i.e. embedded macros in an excel sheet as the first entry point with the final DLL payload persisting itself in a path built using the environment variable “%UserProfile%\AppData”, appended with a random string (in the registry? Please specify here). Using these tactics, also covered as T1027 in the MITRE ATT&CK Matrix, Emotet authors likely attempt to make its artefacts difficult to discover. Most EDR tools claim the ability to hunt malware, however, the discovery of sophisticated and multi-stage malware such as Emotet can be a daunting task. This is where EclecticIQ’s ER solution comes in; it enables threat hunters to carry out more sophisticated threat hunts to detect threats such as Emotet, over traditional EDRs because of their following shortcomings
-
Endpoint Detection and Response (EDRs) collect telemetry with their agents and provide the ability to alert on artefacts like files based on rules using its path. With Emotet, such rules can be complex. The path depends on the endpoint’s environment variable itself, thus making it very difficult to create a generic alert rule across a population of endpoint devices.
-
Not all EDRs provide a sophisticated and extensible query language that could simplify such a hunt.
-
Almost all EDRs collect post-installation. This implies that if there is an existing infection coupled with a lack of sophisticated investigation language, then it is near impossible for an EDR to detect Emotet and threat hunters must rely on an additional forensic tool.
Enter osquery, an open-source tool that is gaining popularity as it makes investigating an endpoint device as easy as querying a relational database by exporting different properties of the devices into tables With its sophisticated SQL syntax and ‘file‘ table, osquery provides the ability to search or investigate files on an endpoint device across a set of folders that can be expressed as regular expressions and patterns (also known as globs). However, unlike desktop search tools, osquery does not index the filesystem entries. This creates very poor performance searching with its file table as it does so with in-line directory traversal.
For simulating such a hunt, we created an environment in our lab and planted a lookalike DLL malware mimicking the techniques of Emotet and tried to hunt for it using osquery’s file table
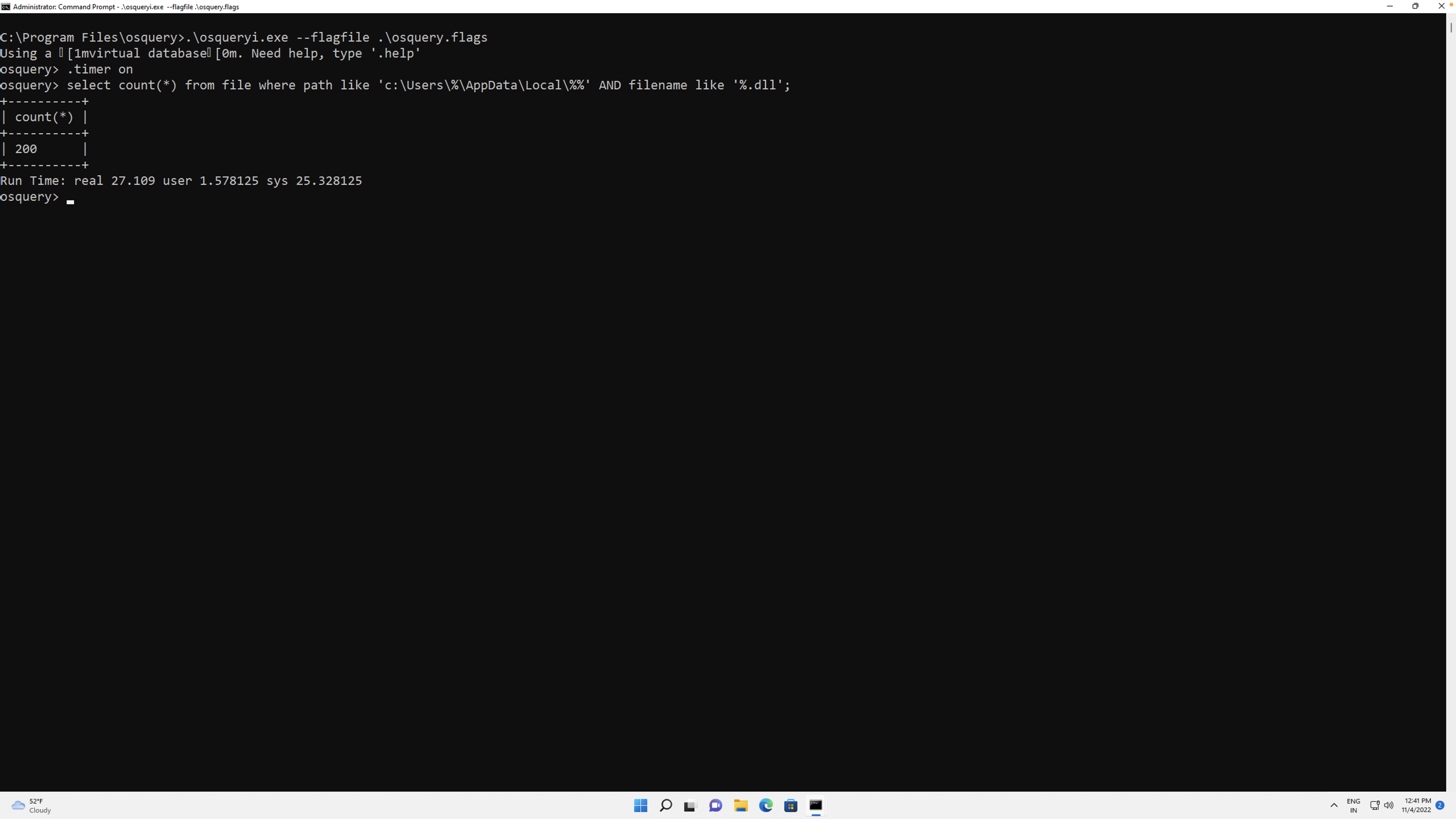
Fig 1. Searching for files using osquery’s file table
As can be seen in the Figure 1 above, osquery provides a sophisticated syntax to search across all user profiles, but the search took nearly 27 seconds to traverse a mere 200 files. On a production endpoint device, this number will be significantly higher.
In the era of Google, no user has the patience to wait for 27 seconds to get results from a search. The query takes even longer when the files to be queried are also matched against their hash values, by joining with osquery’s hash table as it performs additional hash computations of the files.
The only way this osquery syntax can be leveraged is if behind the scenes, the query was served through a table that indexes the disk.
This is one feature we added in EclecticIQ Endpoint Response 4.0. The agent shipped with EclecticIQ Endpoint Response extends osquery with its custom extension that allows leveraging osquery’s SQL to a variety of additional endpoint properties including real-time activities and an indexed filesystem. Running the similar queries on the same endpoint system, but this time against the win_disk_index table of Endpoint Response’s osquery extension, gives the following results:
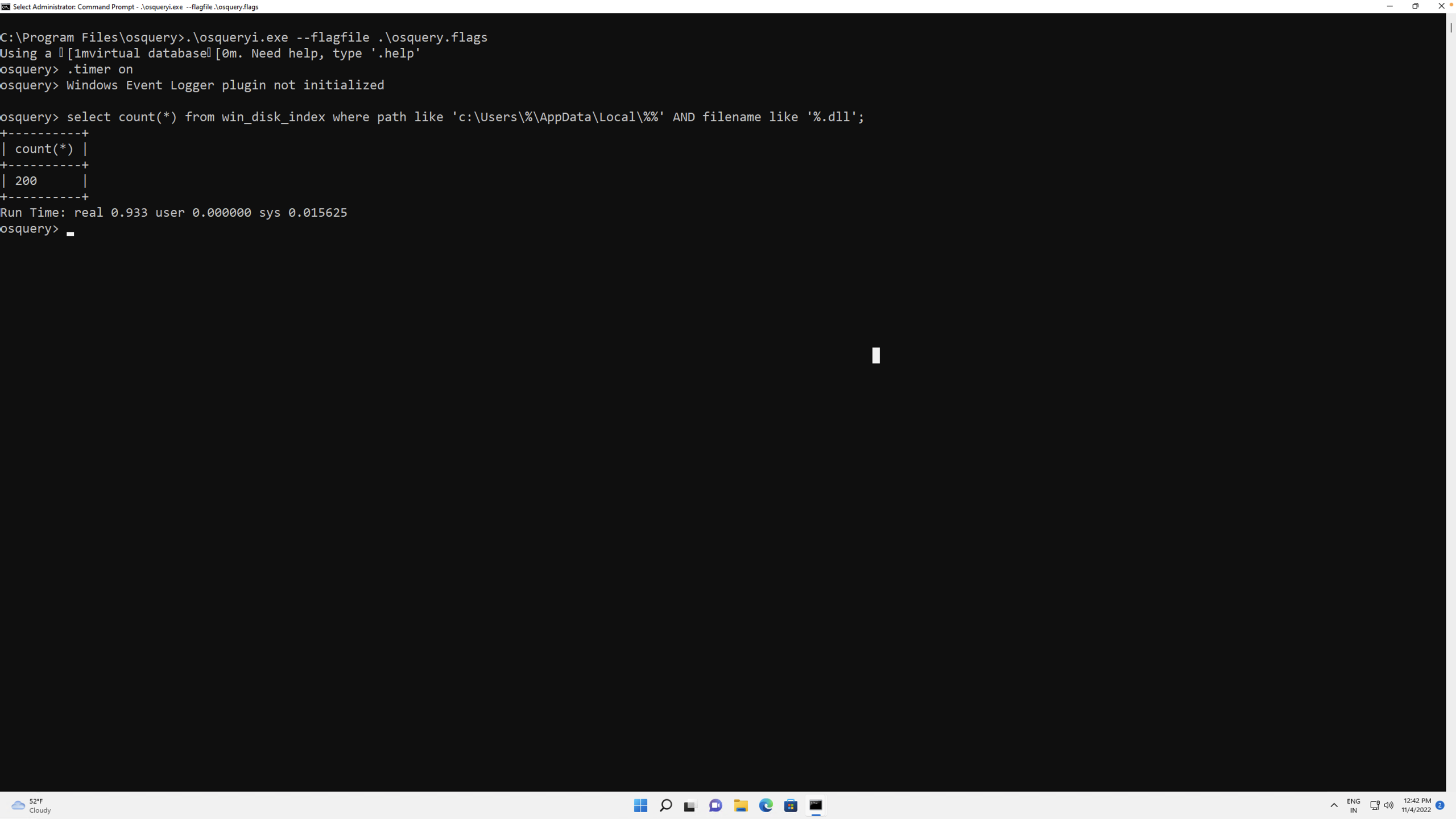
Fig 2. Searching for files using an indexed table
What was earlier taking nearly 30 seconds takes less than a second now. Even if we extend the query to join with the hash table and search for a specific hash, the answer is still returned in 2-3 seconds.
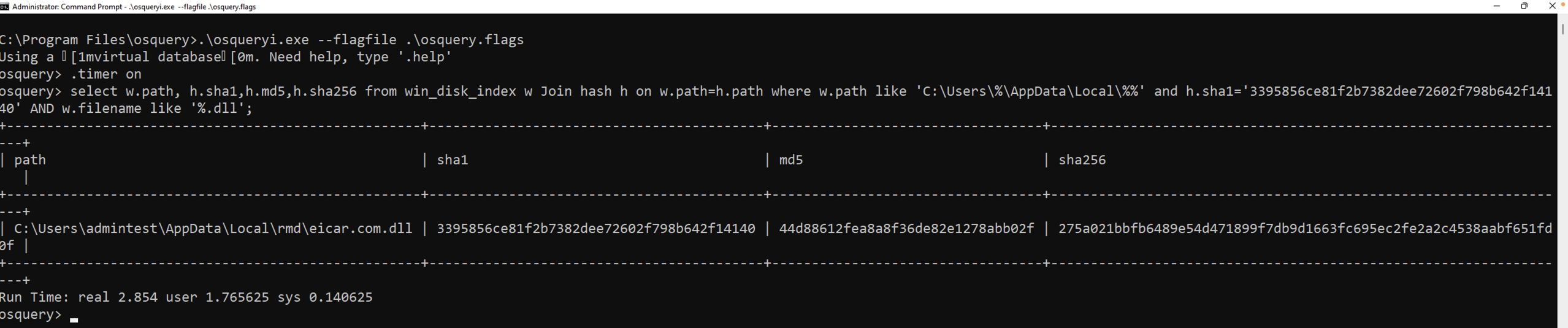
Fig 3. Searching for specific file hash in a list of files, using the indexed table
Figure 2 and 3 show the improvement in query performances when served by osquery via the table created in EclecticIQ Endpoint Response Agent. The most important improvement is to the threat hunter’s efficiency. Additional improvements to the time of the query also include the system resources -both of which are well-known precious commodities in endpoint security. The ability to timely and accurately operationalize threat intelligence is a key pillar on which the practice of threat hunting rests and it can best be achieved only on a platform that enables multiple technologies to work together in a user-friendly way as enabled by EclecticIQ Endpoint Response that combines the power of osquery’s syntax, desktop search, and real-time telemetry capture.
![]()
*** This is a Security Bloggers Network syndicated blog from EclecticIQ Blog authored by EclecticIQ Endpoint Security Team. Read the original post at: https://blog.eclecticiq.com/hunting-emotet-made-easy-with-eclecticiq-endpoint-response





