Any cybersecurity professional knows your security efforts aren’t “one and done.” Cybersecurity measures are continual, as you must constantly monitor your network for breaches and threats that could harm your data and your organization.
An attacker gains access to your network. You know you need to recover from this breach as quickly as possible, but what steps do you take to detect and rebuff the attacker? Then, what comes after to ensure you can retain business continuity in the face of the breach?
This post will examine the phases of the cybersecurity lifecycle in more detail, giving you the information you need to comply with NIST standards.
Phases of the Cybersecurity Lifecycle
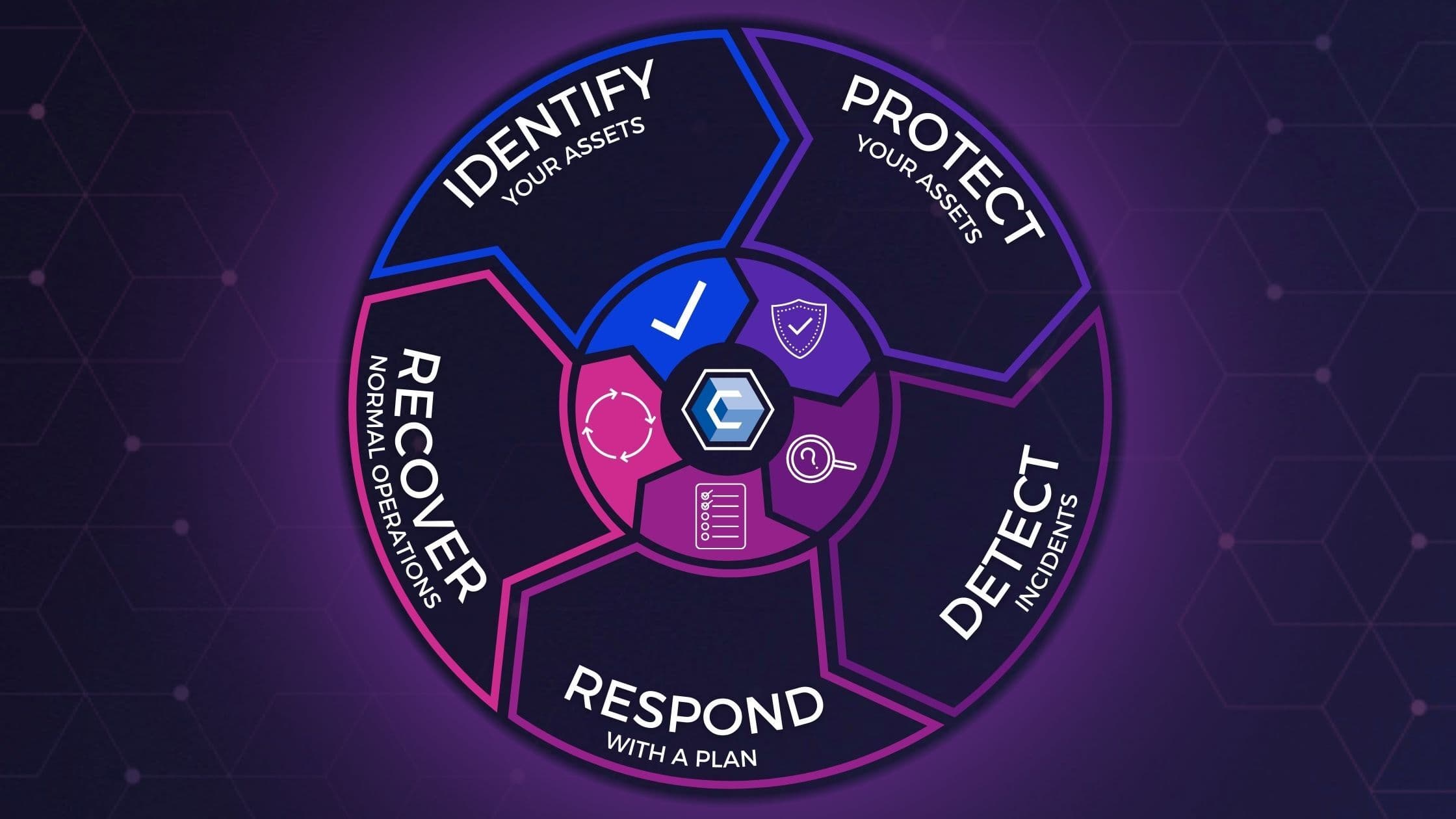
As defined by the National Insitute of Standards and Technology (NIST), the Cybersecurity Framework’s five Functions: Identify, Protect, Detect, Respond, and Recover, are built upon the components of the framework model.
Acting as (Read more...)




