It’s Time to Adopt an “Assume-breach” Mindset
In an age where data breaches seem to be announced weekly, it’s time for companies to adopt an “assume-breach” mindset. This means assuming that your systems have already been breached and taking steps to mitigate the damage.
Yes, it may sound paranoid, but it’s better to be safe than sorry. After all, the consequences of a data breach can be severe, ranging from financial loss to reputational damage. Even if your systems are air-tight, it only takes one employee to click on a malicious email and give hackers access to your network.
Many companies are already taking steps to assume that a breach has occurred. But, before adopting this mindset, you should have a clear understanding of assume-breach security and how it works.
What Is Assume-Breach Security?
Assume-breach security is a proactive approach to cybersecurity that assumes that your systems have already been breached. This mindset shift allows you to take steps to mitigate the damage caused by a breach rather than waiting for one to happen.
It’s important to note that assume-breach security is different from traditional security. With traditional security, the focus is on preventing breaches from happening in the first place. This can be achieved through firewalls, intrusion detection systems, and anti-virus software.
While these measures are still important, they are not enough. Even the most secure systems can be breached, as we’ve seen time and time again. That’s why it’s important to have a plan in place for what to do if (or when) a breach does occur.
This is where assume-breach security comes in. By assuming that your systems have already been breached, you can take steps to mitigate the damage and protect your data.
How Does Assume-Breach Security Work?
There are three key components to assume-breach security: detection, response, and prevention.
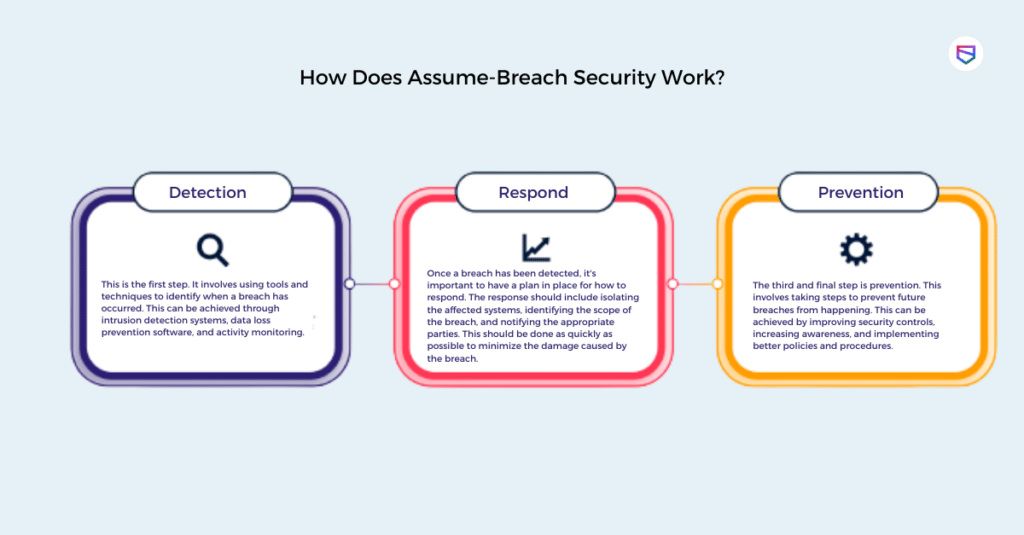
Why Is Assume-Breach Security Important?
Let’s understand how it benefits you and your organization.
1. Respond Quickly to a Breach
By assuming that a breach has already occurred, you can take steps to respond quickly. This is important because the sooner you respond to a breach, the less damage it will cause.
For example–
If you detect a breach immediately, you can isolate the affected systems and contain the damage. However, if you wait days or weeks to respond, the damage will be much greater.
2. Minimize the Damage Caused by a Breach
Assume-breach security also helps you minimize the damage caused by a breach. This is because you can take steps to prevent data loss and protect your systems.
For example-
Suppose you have a data backup system in place. You can quickly restore your systems from the backups if a breach occurs. This will minimize the damage caused by the breach and help you get back up and running as quickly as possible.
3. Improve Overall Security
Another benefit of assume-breach security is that it can help you improve overall security. This is because it forces you to think about security differently.
When you assume a breach has already occurred, you’re more likely to identify weak points in your security. This will help you make the necessary changes to improve your security posture.
4. Protect Your Business
Finally, assume-breach security can help you protect your business. This is because it allows you to take steps to prevent data loss and minimize the damage caused by a breach.
If a data breach were to occur, it could have a devastating impact on your business. By taking steps to prevent and mitigate the damage caused by a breach, you can protect your business from financial and reputational damage.
Conclusion:
The well-known computer defense tactic is known as “assume breach” is predicated on the notion that your business has already been compromised or might quickly be compromised by a determined attacker. This strategy has a lot of validity. Most businesses and organizations are straightforward to breach and hack. It doesn’t have to be this way, though.
Many extremely safe businesses that don’t experience breaches use whitelisting application control software. Find the remaining security holes in your system and close them. It’s time to adopt an “assume-breach” mindset -. to help identify and contain attackers before they can access your network and cause significant harm.
Learn how to defend your business from the most prevalent attack vectors that aim to compromise your most important assets. – Talk to our delivery head
Related Articles:
Blockchain Network is Secured! But not the apps and their Integrations
How do Cryptocurrencies Affect Cybersecurity?
The post It’s Time to Adopt an “Assume-breach” Mindset appeared first on WeSecureApp :: Simplifying Enterprise Security!.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security! authored by Mahima Jaiswal. Read the original post at: https://wesecureapp.com/blog/its-time-to-adopt-an-assume-breach-mindset/




