Fuzzing the lighttpd Docker Image
Fuzzing the lighttpd Docker Image
·
Lighttpd is an open-source web server optimized for speed with considerations for compliance, security, and flexibility. In the past, lighttpd 1.4.15 version had a few vulnerabilities that have since been patched.
Let’s see if you can sniff out those bugs by creating a new Mayhem run for the forallsecure/tutorial/lighttpd:1.4.15 Docker image located in the Mayhem Docker registry!
Instructions:
-
Navigate to the Create New Run page.
-
Select Docker Hub as your image source and search for the
forallsecure/tutorial/lighttpdDocker repository. Select the1.4.15tagged Docker image and click Next to configure the corresponding Mayhemfile. -
Verify that the
cmdsvalue is set to/usr/local/sbin/lighttpd -D -f /usr/local/etc/lighttpd.confand that the Mayhemfile preview looks similar to the following: - Click Next until you reach the end of the create new run flow. When ready, confirm you selections and click Start Run to execute a new Mayhem run for the lighttpd Docker image! Mayhem should be able to find the defect for the lighttpd target within
90seconds.
image: index.docker.io/forallsecure/tutorial/lighttpd:1.4.15
duration: 90
project: forallsecure-tutoriallighttpd
target: '1415'
cmds:
- cmd: /usr/local/sbin/lighttpd -D -f /usr/local/etc/lighttpd.conf
network:
url: tcp://localhost:80
timeout: 2
client: falseDevelopment Speed or Code Security. Why Not Both?
Mayhem is an award-winning AI that autonomously finds new exploitable bugs and improves your test suites.
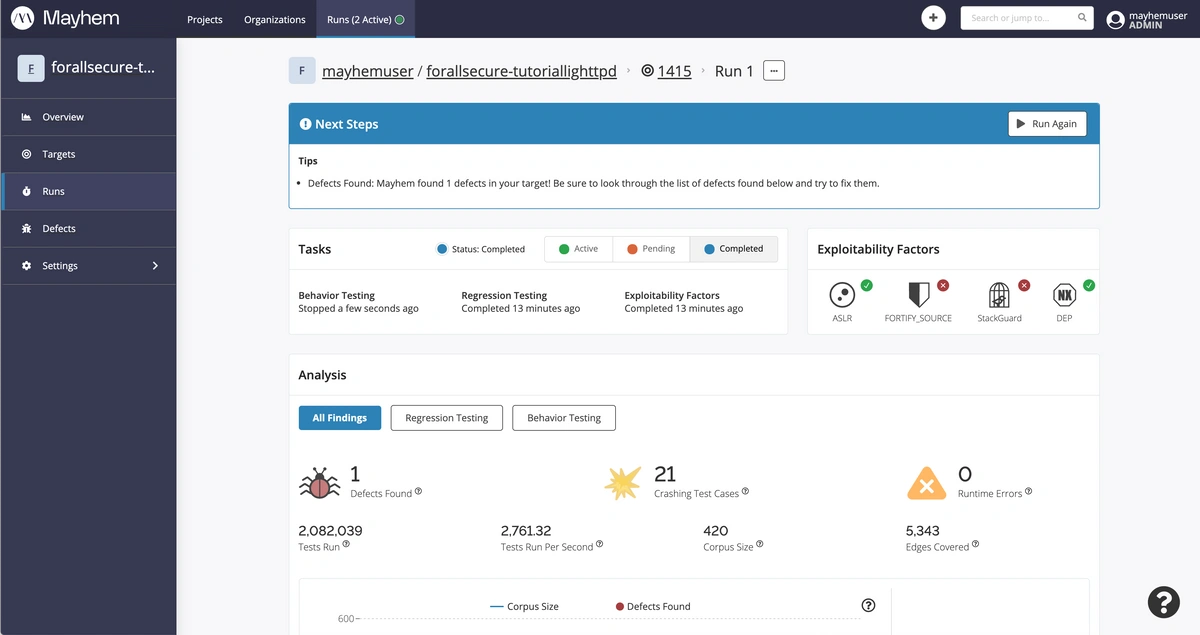
If you were able to successfully execute a Mayhem run on the forallsecure/tutorial/lighttpd:1.4.15 Docker image, you should see a Run page similar to the following:
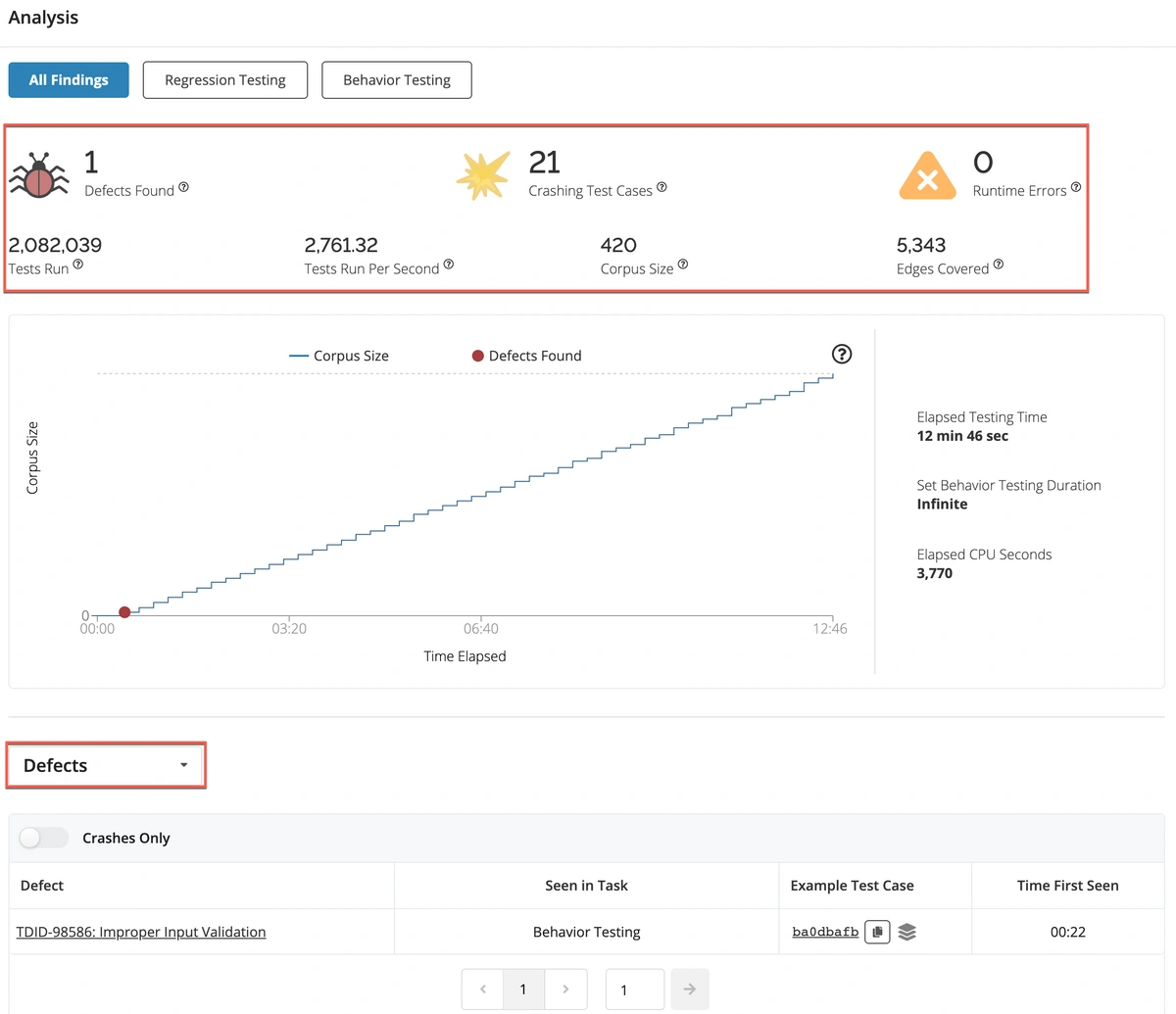
Let’s now take a closer look at what Mayhem found! Scroll down to the Analysis and Test Cases/Defects pane.
Here we can view the following metrics:
- Defects Found:
1 - Crashing Test Cases:
21 - Runtime Errors:
0 - Tests Run:
2,082,039 - Tests Run Per Second:
2,761.32 - Test Suite Size:
420 - Edges Covered:
5,343
Your Mayhem run results should look similar to but may not be exactly what is shown above. This is because when Mayhem fuzzes a target binary, the random input can result in differing levels of coverage for runs of the same target (and duration).
In addition, if we navigate to the Test Cases pane, we can see that for the 21 crashing test cases and 1 unique defect that were found, additional detail is provided for each individual test case of the test suite:
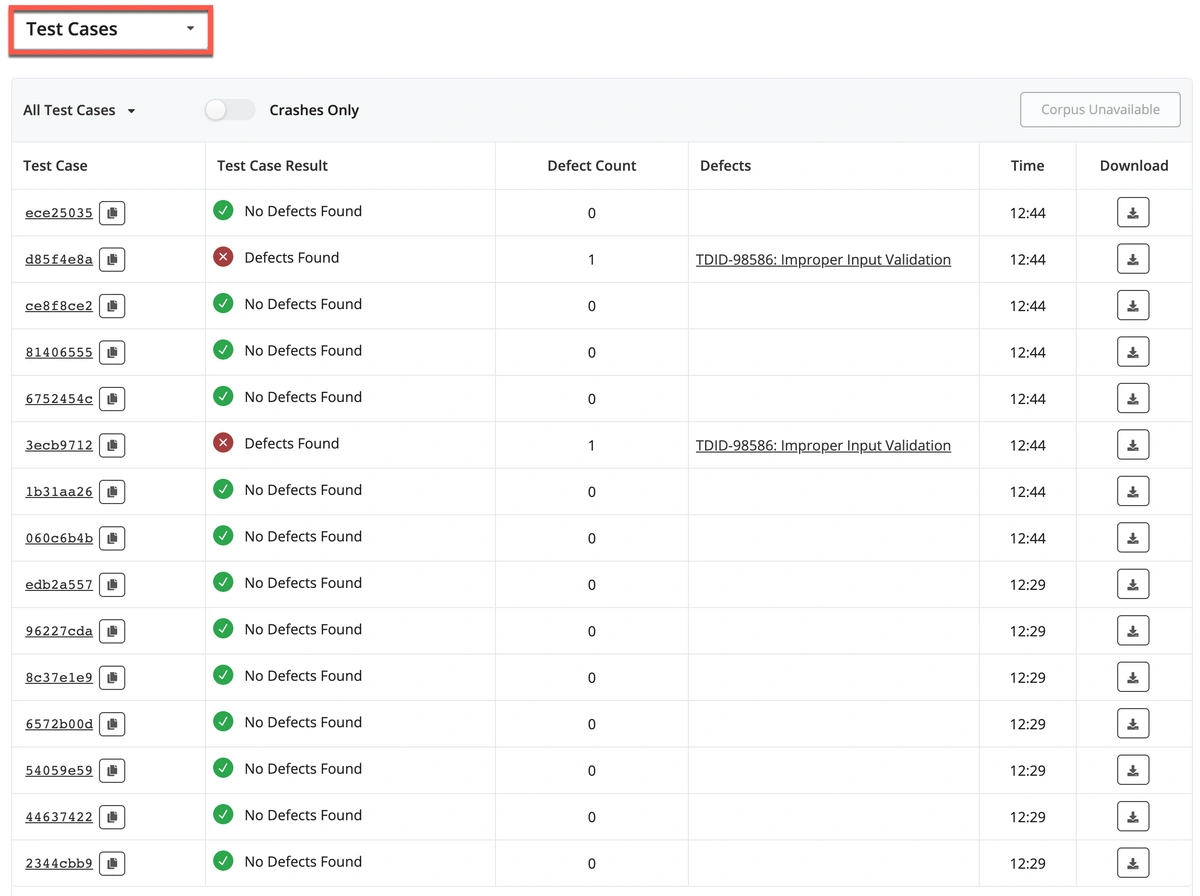
- Test Case ID: The unique identifier of the test case, accompanied by a link for further details and results of the individual test case.
- Test Case Result: The outcome of the input test case.
- Defect Count: The number of defects found per test case.
- Defects: The number of defects found as a result, and the description of the defects found.
- Time: The time of the resulting program crash during the Mayhem run.
- Download: A download button to download and save each individual test case.
And that’s it for now! Play around and see what else you can find about the resulting test cases for lighttpd and how they impacted the underlying code!
Nice job completing your first hands-on lesson!
Stay Connected
Subscribe to Updates
By submitting this form, you agree to our
Terms of Use
and acknowledge our
Privacy Statement.
*** This is a Security Bloggers Network syndicated blog from Latest blog posts authored by Editorial Staff. Read the original post at: https://forallsecure.com/blog/fuzzing-the-lighttpd-docker-image