Identity Governance and Administration (IGA): Is it enough?
Reading Time: 11 minutes
According to the Identity Defined Security Alliance (IDSA)’s study, ”Identity Security: A Work in Progress,” 94% of organizations experienced a data breach, and 79% were breached in the last two years. While managing identities may seem straightforward, they are the most significant risks to cloud environments. Under the hood, the cloud comprises many settings, trust relationships, and interconnected services and resources that make it a sophisticated environment to adequately secure. Unfortunately, organizations manage identities through Identity Governance and Administration (IGA) and Identity Access Management (IAM) only. Because they do not fully understand the intricacies of identity security and identity governance, they miss identity risks.

What is Identity Governance and Administration (IGA)?
Identity Governance and Administration (IGA) provides the necessary tools for identity security. The tools can help businesses automatically connect with their users. This connection means they can provide access without any hassle associated with managing these intricate processes. The IGA software is two parts: identity governance and administration.
Identity governance is the practice of managing and governing identities and their access to them within an organization. The practice encompasses everything from developing and enforcing operations around identity management to monitoring user behavior and activity. While protecting the organization against potential security exposure, identity governance helps organizations ensure that only authorized individuals have access to the systems and data they need to do their jobs.
Identity administration (IDA) includes several vital processes and primarily deals with how access to your data is controlled through proper account setup. Also, identity administration manages credentials, account provisioning, device, users, de-provisioning, and entitlement risks.
These two areas work together to mitigate exposure by providing additional functionality beyond what traditional system offerings. But are they enough to keep your environment secure?
IAM vs. IGA: What’s the difference?
While IGA and IAM work side by side —they’re not the same. An IGA platform goes beyond standard IAM systems by helping businesses to administer identities, meet compliance requirements, and audit procedures for their company’s reports. So what is the difference between IAM and IGA?
Identity and access management (IAM) is the framework that enables organizations to manage electronic or digital identities. This includes policies, programs & technologies for facilitating an organization’s IT security suite by reducing identity-related risks from outside sources who have nefarious intent regarding their users’ information within data systems and resources.
IGA combines Identity Governance and Identity Administration. It is a policy framework and set of security solutions that enable organizations to mitigate identity-related access risks within their business more effectively. Tech Target defines IGA as the ‘policy-based centralized orchestration of user identity management and access control,’ indicating the function ‘helps support enterprise IT security and regulatory compliance.’ IGA automates the creation, management, and certification of user accounts, roles, and access rights for individual users in an organization. IGA enables organizations to streamline user provisioning, password management, policy management, access governance, and access reviews within their business.
While they may sound very similar, Gartner takes care to distinguish between the function, extent, and purpose of IGA and IAM. Specifically, it notes, ‘IGA differs from IAM in that it allows organizations to not only define and enforce IAM policy but also connect IAM functions to meet audit and compliance requirements.’ This means Identity Governance and Administration have the distinct purpose of ensuring IAM policies are connected and enforced.

IGA and IAM do have one thing in common – they both miss the risk of non-people identities in the cloud. When considering identity management in an enterprise setting, you may consider your users first. But people are just one part of the equation. Non-people identities can take on many forms within the environment, and they can generally act intelligently and make decisions on behalf of traditional people identities. Think bots, serverless functions, infrastructure of code, services, and compute resources.
Every time you implement a new technology solution into your organization, you introduce a unique identity to the business, with its own set of risks. Due to digital transformation, there are far more non-person identities than person identities, which means your risk profile is increasing, often in ways and areas unknown to you. As cloud adoption accelerates, there’s been an explosion in non-people identities which IGA and IAM fail to manage.
The case of Identity Governance and Administration
As traditional provisioning solutions struggled to keep up with increasing identity demands and regulations, many organizations turned to identity management solutions to address these challenges.
Identity governance initially emerged as a new category of identity management driven by the requirements of new regulatory mandates such as the Sarbanes-Oxley Act (SOX) and the Health Insurance Portability and Accountability Act (HIPAA). Designed to improve transparency and manageability, identity governance gave organizations better visibility into identities and access privileges and better controls to detect and prevent inappropriate access or access requests.
As more and more customers deployed identity governance and provisioning solutions together, it became clear that the role, policy, and models provided by identity governance were foundational to provisioning and compliance operations. At the same time, it became transparent that organizations needed centralized visibility over both on-premises and cloud applications and data files.
As the digital world continues to evolve, so do the solutions designed to secure it. Recently Gartner emerged again, saying, “security and risk management leaders must combine traditional IAM approaches with CIEM to achieve efficient identity-first security management results.”
No doubt, every enterprise needs to know what their identities can access and what they can do with their access. Managing entitlements or permissions for your identities is an extraordinarily complex and challenging task that requires more than IGA and IAM can offer. To securely manage environments, organizations need to take a holistic approach and determine, for every identity, its effective, end-to-end permission. This approach involves evaluating the policies and access controls directly attached to the identity and mapping out what that identity can do with those permissions. This gap in effective permissions of non-person identities is where organizations get into trouble and where Cloud Infrastructure Entitlement Management (CIEM) is crucial.

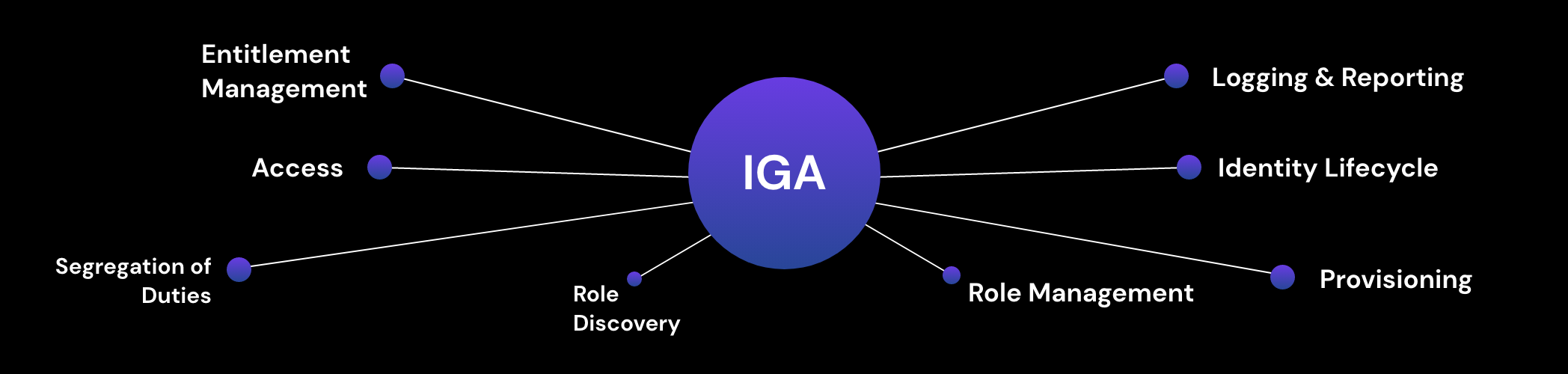
Core components of IGA
Before we explore how IGA can support you and whether it makes sense for your organization, let’s define its components:

Identity governance: Processes and policies covering segregation of duties, role management, logging, access reviews, analytics, and reporting.

Identity administration: Account and credential administration, user and device provisioning and de-provisioning, and entitlement management.
Benefits of IGA

Improve user identity lifecycle management
User management has evolved dramatically as many organizations have relaxed policies. When onboarding and offboarding, managers and IT personnel typically had direct physical access to the resources they needed to manage and change, but now that’s not necessarily the case. Therefore, you should maintain the proper level of control over users, networks, environments, and other IT resources, and this is where an IGA solution becomes integral.

Improve permissions management
Permission management uses verification for who has access to which resources and efficiently provisions and de-provision access to meet compliance and security standards. These tools can often go a level deeper and allow you to specify what actions a user can take inside of a provisioned app based on their role.

Reduce risks
An IGA solution reduces risk and improves compliance and security by managing access control in a comprehensive and streamlined manner. By using tools that streamline user identity lifecycle management, your organization is at less risk for the wrong users having access to confidential information, and you have higher visibility into what different users do and do not have access to.

Fewer errors
Less risk of human error when automated processes are in place makes it easier to improve security by reducing manual tasks and proves compliance through reports of those automated procedures.

Improve Identity security operations
Identity governance and administrations allow organizations to verify that the proper controls are in place to meet the security and privacy requirements of regulations like SOX, HIPAA, and GDPR. They provide consistent business operations for managing passwords and reviewing, requesting, and approving access, all underpinned by a standard policy, role, and risk model. With role-based access control, organizations significantly reduce the cost of compliance while managing risk and establishing repeatable practices for more consistent, auditable, and easier-to-manage access certification efforts.
Challenges of IGA

‘Users’ only focus creates chaos
After seeing how IGA solutions streamline user identity lifecycle management and reduce risk while improving compliance and security, it’s easy to see how they can help your organization scale over time. However, when scaling users, your computing power is scaling, creating massive chaos of non-person identities in your cloud. Sticking to manual processes and having little to no visibility into your IT systems doesn’t provide any good opportunities for scaling correctly. If you’re going to rise, whether it’s now or later, you need to have the processes, workflows, and automation in place before doing so successfully for both your users and pieces of compute.

Lack of visibility into entitlements
Every enterprise needs to know what their user and machine identities can access and what they can do with their access. Managing entitlements or permissions for identities must extend beyond people. Each identity’s effective, end-to-end permission should be known regardless if it is a person or non-person identity. IGA focuses only on the person’s identity, which can leave massive blind spots. Can it take on or assume another identity? If it can, it now takes on the permissions of that identity. What can it do with these new permissions? If we looked only at the first level request, we would be blind to everything else. This is where organizations get into trouble and where Cloud Infrastructure Entitlement Management (CIEM) is crucial.

Lack of enforcement on IAM controls
Efficient access to resources is provided to employees; as your organization grows, it’s quick and easy to provision and de-provision access to resources en masse, rather than dealing with each machine individually. However, this efficiency creates chaos as you have non-people identities created without visibility into who or what has access to them. This increased risk will create a compliance and security headache.
Does your org need more than an IGA Solution?
As traditional provisioning solutions struggled to keep up with increasing identity demands and regulations, many organizations turned to identity management (IDM) solutions to address these challenges. The digital landscape was evolving rapidly as the introduction of software-as-a-service (SaaS) applications, and digital solutions began sweeping through the enterprise landscape. The transition to these technologies means that internal user identities are now used to access new external cloud-based applications and systems outside the enterprise network. The result was a tangled web of access to internal and external systems, a disorganized mass of accounts for the workforce, consumers, and partners, and varying access levels across multiple environments.
Because of these new and ever-growing challenges, identity management solutions do not meet compliance regulations to ensure user access is reviewed, allowed, and/or revoked periodically. As a result, organizations would manually create and check user access certifications via spreadsheets distributed by email to business line managers annually or biannually for review and approval. Yet, with the exploding number of internal and external user identities, systems, and cloud applications, this process was no longer a scalable or viable option. A new approach was needed, with pressure mounting on organizations to achieve regulatory compliance.
Now an approach with both person and non-person identities is possible.
What to look for in an IGA solution?
Identity governance and administration solutions help businesses with the lifecycle management of their user identities. Specifically, an identity governance and administration solution works with IAM tools to:

Manage passwords: Tools like password managers and single sign-on prevent your users from using the same weak passwords across applications, protecting your organization from a potential breach.

Automate workflows: You can create automated workflows for processes like onboarding and offboarding users, providing specific roles with different levels of access, and approving user access to applications and systems.

Manage permissions: Businesses can streamline the review and verification of user access to various apps and resources and automatically provision and de-provision access permissions at the user and application levels. Furthermore, they can specify and verify the actions users can carry out in various applications and define and manage access through user roles.

Ensure compliance: With logging, reporting, and analytics functionalities, organizations can remain compliant with industry-specific and general data-focused regulations. These tools can also help identify potential optimization opportunities or risks.

Scale your organization: Centralized policies for identity management help streamline processes across various applications—whether on-premises or on the cloud. This allows your own developers to focus on the work they do best, enhancing your custom application and organically growing your customer audience.
Together, these components work together to enhance how you manage person identities.
What to look for in a CIEM solution?
Today, CIEM solutions are required as part of a next-generation solution to address the challenges of identities across cloud environments. Cloud infrastructure entitlements managers should implement the following security best practices.

Account and Entitlements Discovery – Inventory all identities and entitlements and appropriately classify them in real-time. This adjusts for the dynamic nature of cloud environments and the ephemeral properties of cloud resources.

Multicloud Entitlements Reconciliation: econciles accounts and entitlements and identifies which ones are unique per cloud and which ones are shared, using a uniform model to manage simply.

Entitlements Enumeration: Based on discovery information, entitlements can be reported, queried, audited, and managed by the type of entitlement, permissions, and user. This allows for the pivoting of information to meet objectives and the management identities and entitlements-based classification.

Entitlements Optimization: Based on the real-time discovery and operational usage of entitlements, the solution classifies over-provisioning and identities, which can then be optimized for least privileged access.

Monitoring Entitlements: Real-time discovery also allows the identification of any changes in identities and entitlements, thus alerting and detecting inappropriate changes that could be a liability for the environment, processes, and data.

Entitlements Remediation: Based on all the available data, recommends and, in most cases, fully automates the removal of identities and associated entitlements that violate established policies or require remediation to enforce least privilege principles.
FAQ
Identity governance is critical to any security strategy for large, international organizations and every enterprise organization. Organizations need to strengthen access controls to their sensitive data regardless of their size or industry. Irrespective of whether a business needs to comply with regulations, it is imperative that they protect their person identities, non-person identities, and privileges to ensure they have effective access controls.
Most enterprise cloud security platforms make it easy for you to stay compliant, whether HIPAA, SOX, PCI, or an internal regulation, giving you visibility and access control to data for every identity. We recommend using tools with out-of-the-box compliance controls and a platform that will apply predictive analytics to monitor and identify unusual access behavior continuously.
Streamline Identity Governance and Administration with Sonrai Dig
With organizations accelerating workloads to the cloud, Sonrai Security can help you mitigate cloud risk related to overly permissioned identities. Sonrai can help your organization work towards the least privileged model. Sonrai Security provides actionable visibility to cloud identity and entitlement exposures so organizations can take corrective action. The solution makes identifying and reducing risk simple by offering trust relationship visualizations for cloud identities, roles, permissions, and resources. With Sonrai, security teams see excess permissions that areleveraged to create kill chains and attack paths, move laterally, and maintain persistence within the public cloud environment.

*** This is a Security Bloggers Network syndicated blog from Sonrai | Enterprise Cloud Security Platform authored by Kelly Speiser. Read the original post at: https://sonraisecurity.com/blog/identity-governance-administration/





