Palo Alto Networks Issues BRc4 Attack Simulation Tool Warning
The Unit 42 research arm of Palo Alto Networks this week reported a Brute Ratel C4 (BRc4) adversarial attack simulation tool is being used by cyberattackers to evade detection.
Peter Renals, principal threat researcher for Unit 42, said BRc4 is being used as an alternative to the Cobalt Strike penetration testing tool that many cybercriminals have coopted to launch attacks. The main difference is that BRc4 is designed to avoid detection by endpoint detection and response (EDR) and antivirus (AV) tools, he noted.
BRc4 was originally created by Chetan Nayak, a security engineer based in India, to provide cybersecurity teams with a penetration testing tool; the entity that maintains BRc4 today claimed there are 480 users of the tool. It is currently priced at $2,500 per user and $2,250 per renewal, and Renals said the number of cybercriminal entities willing to license BRc4 may be limited due to its cost.
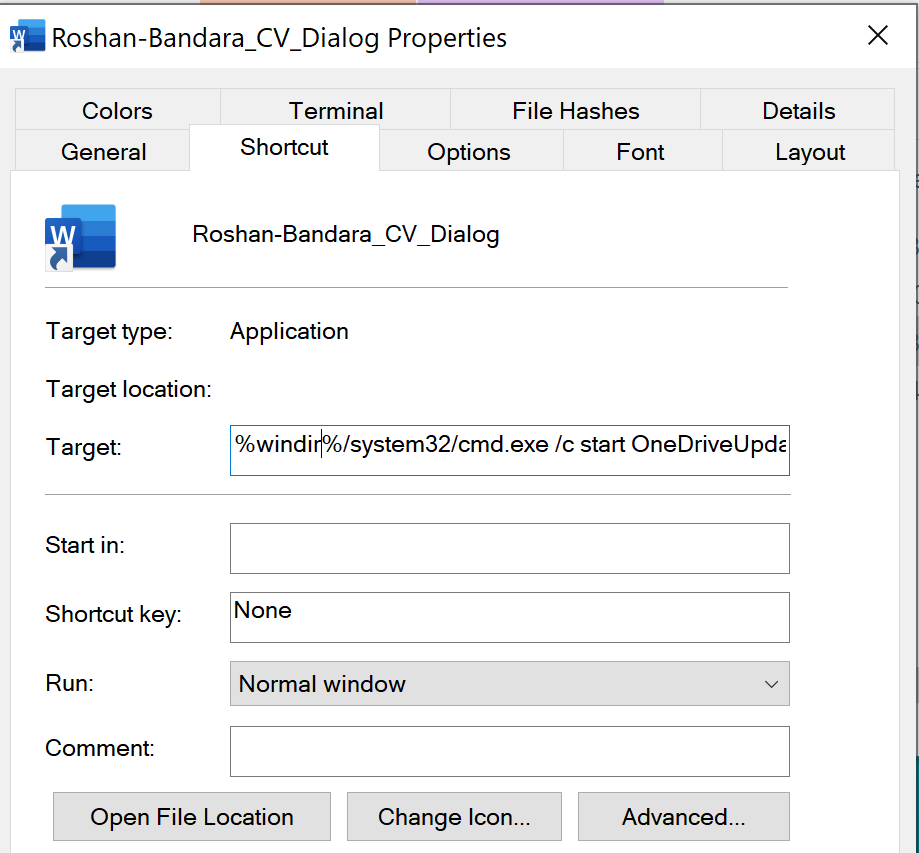
Like other penetration testing tools, BRc4 can be used for both good and for malicious purposes. Unit 42 reported it has thus far identified a total of 41 malicious IP addresses and nine BRc4 samples impacting four organizations. One sample called home to an Amazon Web Services (AWS) IP address located in the United States over port 443. The X.509 certificate on the listening port, however, was configured to impersonate Microsoft with an organization name of “Microsoft” and organization unit of “Security.”
Unit 42 also noted the sample was packaged with a Windows shortcut (LNK) file, a malicious payload dynamic load library (DLL) and a legitimate copy of Microsoft OneDrive Updater. Attempts to execute the benign application resulted in the loading of the malicious payload as a dependency through a technique known as DLL search order hijacking.
Those packaging techniques are consistent with previous malware samples attributed to the cybercriminal gang known as APT29, Unit 42 researchers added.
Renals said it’s apparent that some cybercriminal gangs are making use of more advanced penetration and attack simulation tools that previously were only available to nation-states. It’s still early days as far as the use of BRc4 is concerned, but cybersecurity teams should expect to see many more sophisticated attacks that leverage BRc4 in the months ahead, he added. In fact, cybersecurity teams should immediately start scanning for indicators of compromise involving BRc4, noted Renals.
It’s not clear how long it might take for cybersecurity vendors to be able to identify BRc4 but, in the short term, it would appear that manual effort is required to detect its presence. That may not be what chronically short-staffed cybersecurity teams want to hear, but the fact is they are locked in an arms race. It would appear that cybercriminal gangs have a new weapon in their arsenal—one that cybersecurity teams can’t counter without specifically scanning for it. Hopefully, one day soon, cybersecurity vendors impacted by BRc4 can automatically detect it.