Out-of-band application security with Intelligent Orchestration
Intelligent Orchestration enables security and development teams to implement coordinated DevSecOps workflows with minimal friction.
Application security (AppSec) adds an extra layer to software development. The more the process is automated and the more tools are integrated into the continuous delivery/continuous deployment (CI/CD) pipeline, the more challenges organizations face in securing software security from end to end (false positives, noise, etc.).
Most organizations recognize the need to secure their software development, but there is a real fear that AppSec will slow down the process. And it can, when not implemented effectively. But it doesn’t have to. It’s possible to automate the initiation and management of out-of-band AppSec activities—those that can’t be run in a pipeline, either because they take too long or because they require human intervention. But using policy-as-code, it’s possible to run the tests you need (both automated and out-of-band) when you need them, and filter the results so you get only those that matter to your organization.
Security testing
There are no security methodologies that find all possible defects or vulnerabilities. A complete security program requires overlapping tests and processes. There are several security testing activities that can and should be applied to applications in development. One type of testing identifies flaws in the software, and another type of testing identifies defects.
Identifying flaws
Two common out-of-band testing tools used to identify flaws in the application architecture are
- Architecture risk analysis: This is a time-consuming process that finds weaknesses in the architecture that would allow attacks to be successful. It is performed early in the software development life cycle (SDLC), when it is easier to find and remediate security issues.
- Threat modeling: This identifies the types of agents that threaten the architecture, software components, security controls, assets, and trust boundaries. This type of testing looks at a system from the perspective of a hacker to identify what damage it’s possible to do.
Identifying defects
There are automated and out-of-band testing techniques to identify the weaknesses and defects (such as session management, denial of service, API abuse, insecure use of cryptography, business logic issues, and poor coding practices) that make software vulnerable. Because it examines the code base, static analysis, for example, can automatically identify vulnerabilities like buffer overflows, SQL injection, and cross-site scripting. But it is not useful for identifying business logic issues, which requires an out-of-band review of the code.
Automated, inline solutions that run without any human intervention include
- Static application security testing (SAST) analyzes source code before it is compiled to find security vulnerabilities.
- Dynamic application security testing (DAST) examines an application while it’s running, with no access or visibility into the source program.
- Software composition analysis (SCA) is an automated process that identifies the open source and other third-party software in a codebase, to evaluate security, license compliance, and code quality.
- Risk based security testing ensures that quality assurance processes focus on security tasks and identifying and assessing vulnerabilities and weaknesses.
Out-of-band testing tools include
- Code review is a human looking at source code, line by line, to find vulnerabilities, test business logic, and see if the code is properly implemented.
- Penetration testing simulates attacks on a system in an attempt to gain access to sensitive data, with the purpose of determining whether a system is secure.
Intelligent Orchestration
With the complexities of modern applications, security testing requires multiple activities and resources at different phases of the pipeline—planning, coding, building, testing, prerelease, deployment, and operations. The answer is implementing continuous security in parallel to the development pipeline. Intelligent Orchestration by Synopsys isolates security tests in a dedicated pipeline that integrates easily into existing pipelines with a couple of API calls, and then runs in parallel and connects tools to the security pipeline, whether they run on premises or in the cloud.
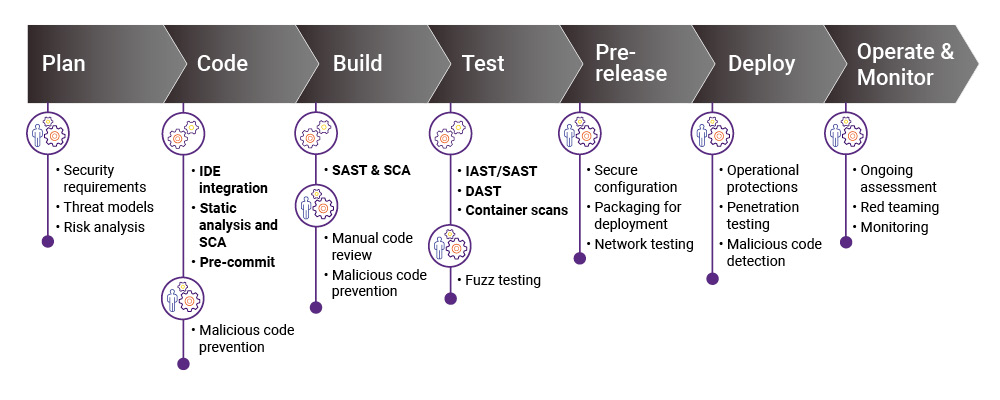
This integrated solution includes security checkpoints at strategic places in the CI/CD pipeline that halt development when critical vulnerabilities are found. You define the rules, based on your business policies and processes, such as the business-critical nature of the application, data classification, and the significance of the activity detected. The solution translates that into a risk score to filter and prioritize activities. When an issue reaches the predetermined threshold, based activity you define as significant (i.e., code change, compliance requirements, scheduling), Intelligent Orchestration triggers the next action and determines which combination of inline and out-of-band testing to run.
For example, testing tools can always find something wrong in an application, even minor code changes or low-priority defects with low-risk scores and that are not necessary to address immediately or at all. By prioritizing results, Intelligent Orchestration will generate only the testing results you have specified are important, which saves time and resources, and prevents the team from being overloaded with minor vulnerabilities.
Intelligent Orchestration is designed to keep the development and business teams informed as well. Teams get only the results and insights they truly care about and can act on. This can include details about the vulnerability, the tools necessary to address it, and the depth of the analysis needed to mitigate this particular risk.
SDLC security at scale
Delivering the right information to the right teams so they get results they care about and can act on saves time and resources and minimizes vulnerability overload. Intelligent Orchestration makes it easy to build security into DevOps pipelines without compromising development or distracting your developers from what matters most.
Learn more about the challenges development and security teams face, and explore strategies to minimize risk without impeding development velocity in this white paper from Enterprise Strategy Group: Cracking the Code of DevSecOps.
![]()
*** This is a Security Bloggers Network syndicated blog from Application Security Blog authored by Meera Rao. Read the original post at: https://www.synopsys.com/blogs/software-security/out-of-band-appsec-intelligent-orchestration/







