Skimming, Shimming, and Threat Intel: The Relevance of Physical Fraud in Today’s Threat Landscape 
Skimming, Shimming, and Threat Intel: The Relevance of Physical Fraud in Today’s Threat Landscape

On June 21, 2022, a Polish national was deported from Bali after serving 3 years in prison for ATM-related crimes, namely inserting small, physical devices into ATM card slots to swipe payment card data and PIN codes, called skimming.
In the past six months, several other individuals have been arrested, sentenced or deported from the United States and abroad, including a Romanian national associated with 35 skimming incidents in Connecticut in 2017, a Cuban national that along with co-conspirators stole over $200,000, a Las Vegas man that integrated ATM skimmers into wider credit card fraud schemes, and a Miami man charged with access device fraud and money laundering conspiracy.
All of these arrests are for activities that took place between 2013 and 2017, leading us to question if ATM fraud is still relevant. The short answer is yes, but let’s see why.
That’s where the money is
Attacks on ATMs and other physical payment-related devices, like point-of-sale (POS) terminals, have long been leveraged by threat actors as a way to steal victims’ personal information either to sell or to use fraudulently. Before chip cards existed, skimming was used to intercept magnetic stripe information from credit cards as they were swiped through card readers, allowing threat actors to copy the card number, PIN, and expiration date.
Blank cards with magnetic stripes, like gift cards or hotel keys, can then have this information transferred over to them, essentially creating a copy of the victim’s card that can be used to steal funds. Alternatively, stolen card credentials can also be sold in illicit communities to be used for virtual purchases.
Fueling card fraud
Gas pumps have become particularly associated with skimming attacks, and have a reputation for being prone to having skimming devices attached to their POS terminals compared to other places. Threat actors will often target gas pumps because of their lack of human supervision, which makes it easy to install the skimmers without being caught.
ATMs and car washes are similarly prone to such attacks because of how loosely they are monitored, giving threat actors plenty of opportunity to collect victims. The FBI has provided guidance to choose gas pumps within view of the gas station attendant, or consider paying with the attendant as opposed to the pump.
Effective October 2015, US payment networks instituted a liability shift as part of an EMV chip rollout. In brief, merchants would now be responsible for fraud occurring on POS devices, ATMs, and automated fuel dispensers (AFDs) that occured because of a failure to implement EMV. The implementation of EMV in the United States was slower when compared to Europe, owing to some large credit card breaches that were observed on darknet credit card shops like Joker’s Stash.

The rollout included some exceptions. AFDs received an extension until October 1, 2017 because of the complexity of their payment systems, and associated costs with upgrading. The deadline was pushed back twice, initially to October 2020, and more recently to April 2021. Visa has reported to already observe a decrease in credit card fraud at AFDs, however motorists should remain vigilant.
The role of skimmed credit cards
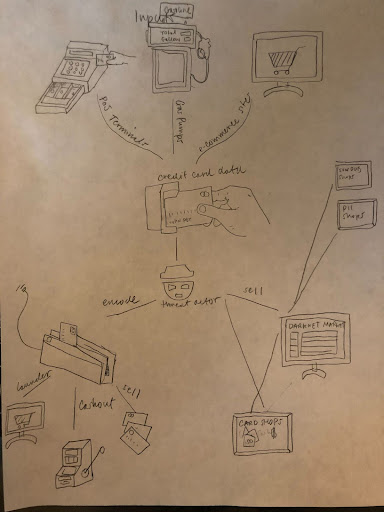
ATM-related crimes are an aspect of credit card fraud. It is typically not the end goal or objective, but typically used in a wider fraud scheme. The supply side of credit card fraud includes personally identifiable information (social security numbers, date of birth), blank credit cards, ATM cloning devices, and skimmers. Other pieces of information, like credit card holograms, may provide some credibility. The demand side includes the siphoned credit card information, hacked accounts, and stolen PII to create a fraudulent profile. Recently, two individuals were charged for selling various fraudulent identity documents on darknet marketplaces like the now shuttered AlphaBay. Recently shuttered sites like SSNDOB and WeLeakInfo also facilitated the sale of PII fueling card fraud.
Skimming online
A cursory look through chat messaging services or social media for terms like “ATM Skimming” will tell two stories. Recent images of threat actors holding stacks of cash, card cloning devices and blank credit cards show some of the accoutrement required for credit card fraud. These can be advertisements for skimmers, or skimming services. At times, fraudsters may be looking for partners to either install ATM skimmers at identified locations.

Posts from law enforcement, security researchers, and customers visually show some of the skimmers that have been identified in the wild. This may be shared as a precaution, or to demonstrate the evolution of credit card skimmers.

Defender’s dilemma
The introduction of EMV chips to credit cards presented a challenge to traditional forms of credit card fraud, marking a development in the security of POS transactions. While cards with magnetic stripes could be copied using a skimmer and fraudulent charges could be executed with easy-to-forge information, like signatures or IDs, chip cards use encrypted pins to authorize transactions. Additionally, fraudsters cannot clone cards with functioning and valid EMV chips, meaning it is easier for merchants to defend against more common methods of card fraud.
Recommended Reading: 5 Things CISOs Need to Know About Card Fraud
In response, fraudsters have turned to shimming, which is similar to skimming but allows for chip card information to be copied by inserting a shim into POS terminals. Unlike magnetic stripe cards, a new chip card cannot be created from the stolen information.
However, there are loopholes that threat actors can exploit to evade the additional security provided by chip cards. Although a functional chip card cannot be created using copied information, it can be used to create a magnetic stripe card that can be used for online purchases or at physical stores that have not upgraded to accept chip cards.
There is also a relatively new scam circulating that enables threat actors to make in-store transactions and bypass chip readers using invalid EMV chip cards. Fraudsters install fake EMV chips in credit cards and insert them into the chip reader, which then reports an error since the chip cannot be read. Since most newer terminals are also equipped to process transactions using magnetic stripes to accommodate older cards or those with malfunctioning chips, threat actors can then claim their EMV chip is broken and request to complete the transaction using the magnetic stripe.
Considerations for your threat landscape
Skimming and shimming are still ever-present threats for physical payment systems. However, as online purchases and payments take over, threat actors continue to find new ways to exploit vulnerabilities and steal victims’ PII. Fraud is becoming increasingly digital as e-skimming gains prevalence and threat actors take advantage of emerging vulnerabilities related to card-not-present (CNP) transactions.
Awareness of who threat actors are targeting, what data and information they’re after, and how they operate is key to shielding your organization from these risks and keeping your customers safe. Robust threat intelligence gives you the insight necessary to determine what steps should be taken to effectively mitigate fraud and prevent attacks that put your security and reputation at risk.
Protect your organization from card fraud
Flashpoint’s Card Fraud solutions equip security teams with the tools, dashboards, alerts, and actionable intelligence they need to proactively identify threats, prevent card fraud, and take action to combat exposure to risk. Sign up for a free trial today.
Begin your free trial today.
The post Skimming, Shimming, and Threat Intel: The Relevance of Physical Fraud in Today’s Threat Landscape  appeared first on Flashpoint.
*** This is a Security Bloggers Network syndicated blog from Threat Intelligence Blog | Flashpoint authored by Veronica Drake. Read the original post at: https://flashpoint.io/blog/skimming-shimming-and-threat-intel/





