The History and Evolution of Ransomware Attacks

Ransomware has grown to become a potential threat for all organizations, sparing no industry or size bracket in its goal to capture files and other company assets. Where there’s data, there’s an opening for threat actors to hold this sensitive information ransom and demand payment for its release.
It’s imperative for all organizations to have a plan for how to prevent and respond to ransomware attacks. But in order to understand how to prepare today, it’s also necessary to understand how ransomware has evolved to reach its current state.
The emergence of ransomware (1989)
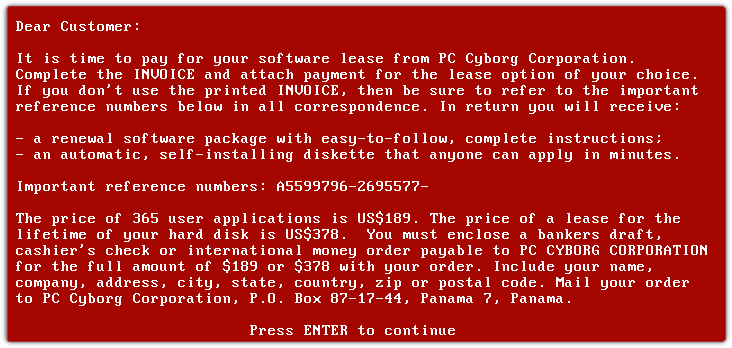
The first ransomware attack is generally regarded as the “AIDS trojan.” It is named for the 1989 World Health Organization (WHO) AIDS conference, at which biologist Joseph Popp handed out 20,000 infected floppy discs to event participants. After a user had booted up ninety times, the names of the user’s files would be encrypted and the below message would appear, asking victims to send US$189 to a PO box in Panama. The ransomware was relatively easy to remove using online decryptor tools.
The early years (2005–2009)
After this first event, no notable developments in the field of ransomware took place until 2005, when ransomware reemerged—this time using secure asymmetric encryption. The “Archiveus” trojan and “GPcode” were the most notable of these early ransomwares. GPcode attacked Windows operating systems, first using symmetric encryption and later, in 2010, using the more secure RSA-1024 to encrypt documents with specific file extensions.
The Archiveus trojan, the first ransomware to use RSA, encrypted all files in the “My Documents” folder. They could be decrypted with a thirty-digit password provided by the threat actor after the ransom was paid.
Despite the effectiveness of these encryption algorithms, early ransomware variants had relatively simple code, which allowed antivirus companies to identify and analyze them. The Archiveus password was cracked in May 2006, when it was found in the source code of the virus. Similarly, until GPcode switched to RSA, file recovery was often possible without a password, leading cybercriminals to prefer hacking, phishing, and other threat vectors.
Ransomware embraces cryptography (2009–2013)
In 2009, the “Vundo” virus emerged, which encrypted computers and sold decryptors. Vundo exploited vulnerabilities in browser plugins written in Java, or downloaded itself when users clicked on malicious email attachments. Once installed, Vundo attacked or suppressed antimalware programs such as Windows Defender and Malwarebytes.
Shortly after, in 2010, the “WinLock” trojan emerged. Ten cybercriminals in Moscow used the software to lock victims’ computers and to display pornography until the victims sent them roughly $10 in rubles. The group was arrested in August the same year—though the scheme first garnered US$16 million.
In 2011, the software was upgraded to pretend to be the Windows Product Activation system. The malware seemed to be requiring a reinstall of the software due to fraudulent use, and ultimately extorted data from victims.
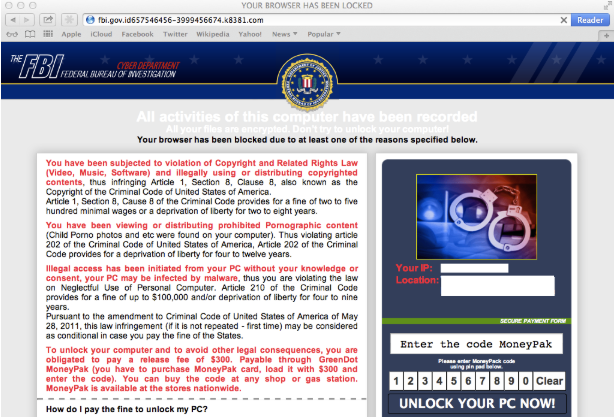
“Reveton” ransomware, which emerged in 2012, was a type of scareware that displayed messages to its victims claiming that it was US law enforcement and that the user had been detected viewing illegal pornography. In some cases, it activated the user’s camera to imply that the user had been recorded. It also demanded that the victim pay in order to avoid prosecution.
A variant of this ransomware also emerged for Mac, although it was not cryptographic. It was made up of 150 identical iframes that each had to be closed, so the browser appeared to be locked.
As more ransomware variants emerged, the number of recorded ransomware attacks increased nearly fourfold from 2011 to 2012.
Ransomware becomes dominant (2013–2016)
In the second half of 2013, “CryptoLocker” emerged. CryptoLocker was a pioneer in several ways: It was the first ransomware to be spread by botnet—in this case the “Gameover Zeus” botnet—though it also used more traditional tactics, such as phishing. Also notable was that CryptoLocker used 2048-bit RSA public and private key encryptions, rendering it especially difficult to crack. CryptoLocker was not stopped until its associated botnet, “Gameover Zeus,” was taken down in 2014.
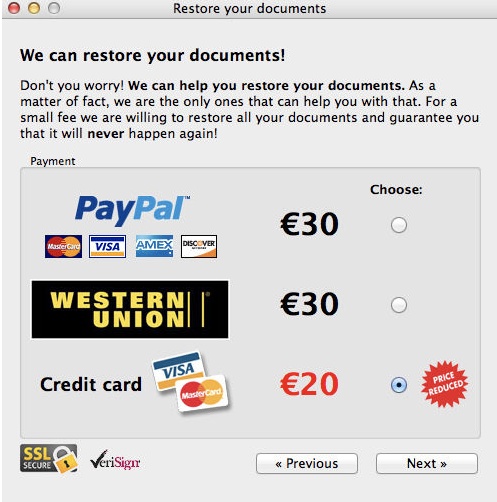
The first true ransomware for Mac, “FileCoder,” was also discovered in 2014, although it was later found to have originated as early as 2012. The malware was never finished, as, although it encrypted files and demanded payment, the only files it encrypted were its own.
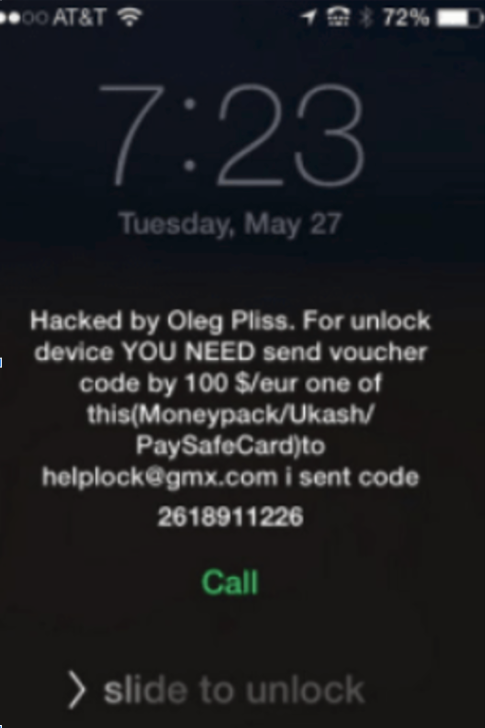
Other noncryptographic attacks on Mac infrastructure were more successful that year. 2014 also saw the “Oleg Pliss” attack, in which a threat actor used stolen Apple account credentials to log in to accounts and then used those accounts to remotely lock iPhones, using the “find my iPhone” feature. They then demanded a ransom for the phone to be unlocked.
Just as Oleg Pliss targeted iPhones, 2014 also saw the first cryptographic attack on mobile devices, with “Spyeng” targeting Android. Spyeng also sent messages to everyone in the victim’s contacts list with a download link to the ransomware.
The first successful cryptographic ransomware attack on Mac was in 2016, and was known as “KeRanger.” Tied to version 2.90 of the torrenting client Transmission, the ransomware locked a victim’s computer until 1 bitcoin (US$400 at the time) was paid to threat actors.
Another ransomware for Mac, “Patcher,” aka “filezip,” emerged in February 2017. It also infected users via torrenting, in this case by pretending to be a cracker for popular software programs such as Office 2016 or Adobe Premiere CC 2017. Notably, due to flaws in its design, Patcher could not be decrypted, whether the ransom was paid or not.
The success of CryptoLocker led to a significant increase in ransomware varieties. CryptoWall emerged as a successor to CryptoLocker, becoming known in 2014, although it had actually been circulating since at least November 2013. Spread largely through spam phishing emails, by March 2014 CryptoWall had become the leading ransomware threat. CryptoWall proved especially tenacious, and some reports suggest that by 2018 it had caused US$325 million of damage.
The emergence of RaaS (2016–2018)
By 2016 ransomware variants were becoming increasingly frequent. The first ransomware- as-a-service (RaaS) variants emerged—partnerships in which one group writes the ransomware code and collaborates with hackers, who find vulnerabilities in systems. Some of the better-known were “Ransom32” (the first ransomware to be written in JavaScript), “shark” (which was hosted on a public WordPress site and made available on the basis of an 80/20 split, distributors’ favor), and “Stampado” (which was available for just $39).
2016 also saw the emergence of the well-known “Petya” ransomware. Initially the ransomware was less successful than CryptoWall, but on June 17, 2017, a new variant emerged, dubbed “notPetya” by Kaspersky to differentiate it from the original version. It began in Ukraine and quickly spread worldwide via the “EternalBlue” Windows vulnerability discovered by the NSA. According to the White House, NotPetya was responsible for US$10 billion in damage. The governments of the United States, United Kingdom, and Australia blame Russia for the malware.

“LeakerLocker,” a mobile ransomware for Android, also emerged in 2017. Unlike more traditional ransomware, LeakerLocker did not actually encrypt any files. Embedded in malicious applications on the Play Store that requested elevated permissions, LeakerLocker displayed sample data from the user’s phone and claimed it would send the user’s entire phone contents to every person in their contacts list if a ransom was not paid.
“WannaCry” ransomware, one of the best-known crypto ransomwares, also emerged in 2017. Like notPetya, WannaCry spread via the EternalBlue exploit. After emerging in May 2017 it infected about 230,000 computers in 150 countries, causing $4 billion in damage. Although Microsoft had already released a patch for this exploit two months before the emergence of WannaCry, many users had not updated their systems, so the ransomware was able to spread.
Related Reading: Linguistic Analysis of WannaCry Ransomware Messages Suggests Chinese-Speaking Authors
The ransomware would likely have been far more damaging had it not been halted a few days after the attack began by the efforts of Marcus Hutchins, who discovered that the ransomware had a built-in “kill switch” that could be activated. Despite Hutchins’ role in stopping the global outbreak of WannaCry, he was subsequently arrested and imprisoned by the FBI for unrelated hacking charges. Several major governments attributed WannaCry to North Korea.
Ransomware and malware merge (2018-2019)
January 2018 was a watershed moment for ransomware, marking the emergence of “GandCrab.” Although GandCrab by itself was not particularly unusual, the developers continued to release more and more advanced versions and eventually integrated it with the “Vidar” information-stealing malware, producing a ransomware that both stole and locked a victim’s files. GandCrab quickly became the most popular RaaS, and the most active strain of ransomware between 2018 and 2019.

“Team Snatch,” a team of threat actors that emerged in 2018, was a partner of GandCrab, and ushered in the new trend of publishing victim data in order to extort payment. Team Snatch began to publish victim data in April 2019. Snatch was formed by threat actor “Truniger,” who operated on Exploit. On April 28, 2019, Truniger posted on Exploit that Citycomp, one of their victims, had refused to pay a ransom and would therefore have their data publicly posted.
However, GandCrab ransomware is now no longer used after the developers announced they would be retiring on June 1, 2019, and the FBI released decryption keys for the ransomware in July 2019.
Although Team Snatch disappeared in 2019 following a dispute on the Exploit forum, their actions set the stage for Maze ransomware and the rise of the leaks sites.
The rise of leak sites (2019–2020)
In November 2019, the “Maze” ransomware group leaked 700 MB worth of documents stolen from Allied Universal in an attempt to pressure them and future victims into paying the ransom. This set off a trend of ransomware groups establishing leaks sites to pressure their victims. By publishing stolen data, ransomware operators expose a victim to additional financial loss if, for example, sensitive financial data, customer personally identifiable information (PII), or trade secrets are exposed.
This additional leverage can be especially effective if a victim has backed up their data—and therefore lacks an incentive to pay extortionists for a decryption key alone. The new technique ultimately means that backing up data no longer mitigates the threat of ransomware attacks.

This new technique has vastly increased the visibility of ransomware, and appears to have increased its popularity as well. In 2020 the NetWalker group alone made over $25 million.
Since Maze ransomware began posting victim data, other ransomware groups have posted their own sites. Several of these ransomware families emerged out of prior partnerships, with “adverts” gaining experience collaborating with a ransomware group before setting up their own. The increased visibility has also led to cooperation between the ransomware groups, with Maze forming a “cartel” of ransomware groups that share tactics, techniques, and procedures (TTPs) and resources.
The “Sodinokibi” ransomware family has been another notable actor in this space. Sodinokibi emerged to fill the space that was left when the GandCrab threat actors retired. Run by the REvil collective, it has become one of the most damaging ransomware groups, with more victims posted than any provider other than Maze.
Ransomware today (2020–present)
Today, ransomware continues to threaten organizations and accounted for over $42.9 million in losses in 2021 according to the FBI’s 2021 Internet Crime Report. Beyond the headlines, it is something companies of every size and in every sector must be aware of—dedicated and well-researched protocols for what to do in the event of an attack have become a mission part of every organization’s security and defense arsenal.
Recommended Reading: Top 10 Ransomware Trends: Board Responsibilities, Tracking Ransomware, and Mitigating Risk in 2022
The rise of ransomware was a gradual process spanning more than thirty years. Its popularity was influenced both by the technologies supporting it, such as encryption methodologies and malware integration, and the technologies around it, such as Bitcoin and the anonymous Tor network, that allowed it to grow from a tool used by a single hacker or group into one run by a collective.
Although ransomware has not replaced other forms of malware per se, it has become an increasingly popular choice for threat actors as the barrier to entry becomes lower. Whereas a ransomware attack used to require years of development, cryptography, and penetration testing experience to execute, and would yield only a moderate profit, RaaS programs now proliferate on illicit and underground web forums, allowing threat actors to partner with ransomware authors easily and cheaply. Furthermore, these RaaS programs are highly developed, with user dashboards, guides, and technical support.
Finally, the payoff is getting bigger. As tools such as Cobalt Strike and Metasploit automate advanced penetration testing, and illicit communities such as Genesis Market offer increasingly advanced access to corporate networks, access to corporations is becoming more available, and ransomware demands bigger and more profitable. The integration of ransomware with data exfiltration allows for even higher ransoms, by threatening legal action for the victim corporation. For all these reasons, ransomware continues to grow in both its influence and destructive capacity.
The impact of Conti
Flashpoint analysts have observed an overall increase in the number of public victims of ransomware, which is consistent with observations made by other researchers. However, recent history shows a somewhat less clear picture. While over the last two years ransomware attacks are up across the board, in recent months, as of this publishing, they’ve fallen.
Perhaps the biggest driver for this decline has been the disbandment of Conti, a Russia-based ransomware group that is among the most well-known and damaging ransomware variants. This split has impacted its ability to execute attacks at the scale it once did, and although parts of its organizational structure remain and there have been signs of Conti activity since May, its death as a brand gives a possible cause for the lull in public victims of ransomware attacks as of late.
However, it is unclear whether Conti’s split alone can explain the drop in the number of public victims observed by Flashpoint. Ransomware operators have faced novel challenges in 2022, including:
- Conti has arguably become a “toxic” brand, due to its open sympathy for the Russian invasion of Ukraine and its alleged connections to Russian law enforcement and security institutions.
- Due to a tighter and significantly more expansive sanctions regime, organizations attacked by Conti face high legal risks if they pay the ransom, which has reportedly impacted victim cooperation.
- In general, sanctions have led to a stricter monitoring of cryptocurrency payments, which in turn has prompted a higher degree of caution from cryptocurrency exchanges and brokers.
While the shift in observed attacks demonstrates how volatile the ransomware landscape is, attacks are on an overall upward trend, consistent with reports by other researchers as well as the US government of an “increased globalized threat” of ransomware.
Other changes in the ransomware landscape
In addition to developments directly in the ransomware landscape that have impacted it, other recent global and geopolitical factors that have created a new “normal” for ransomware attacks, their statistics, and the groups who carry them out.
In particular, the COVID-19 pandemic led to an increase in cybercrime incidents over 2020 and 2021, all while increased awareness of ransomware and stronger responses of law enforcement, governments, and private businesses alike—including stricter enforcement of know-your-customer and anti-money- laundering requirements by cryptocurrency exchanges—complicated the landscape for criminals.
In 2022, geopolitical tensions and an evolving sanctions landscape have further complicated the field for ransomware operators. The changing geopolitical situation—including the elevated risk of financially-motivated cybercriminals being enlisted to help state-backed groups or otherwise encouraged to perform attacks on Western entities—has raised the overall level of awareness to cybersecurity risks, making successful attacks less likely.
Evolving tactics and behaviors
Over the past several years, Flashpoint has observed ransomware groups shifting toward greater sophistication, greater ransom amounts, escalation of extortion tactics, and the use of managed service providers (MSPs) and managed security service providers (MSSPs) as a starting point of compromise.
Analysts have also most recently observed some novel tactics that seem to be attempts to deal with Conti’s fracture and increase income. For example, Conti split into or was succeeded by several groups with different names. TTPs are also changing—traditional ransomware relies on encryption, but some newer groups are conducting only data exfiltration attacks. Some ransomware gangs have made their data openly searchable to put additional pressure on company management through clients and employees. Flashpoint assesses with moderate confidence that this downward trend in attacks is temporary and we will again observe an increased number of attacks as ransomware operators continue to adapt to the recent challenges.
Secure your organization against ransomware attacks
Your organization’s data, infrastructure, and personnel are valuable—don’t let threat actors take advantage of them. Sign up for a free trial and see firsthand how Flashpoint cybersecurity technology can help your organization access critical information and insight into ransomware actors and their tactics, techniques, and procedures (TTPs).
Begin your free trial today.
The post The History and Evolution of Ransomware Attacks appeared first on Flashpoint.
*** This is a Security Bloggers Network syndicated blog from Threat Intelligence Blog | Flashpoint authored by Drake. Read the original post at: https://flashpoint.io/blog/the-history-and-evolution-of-ransomware-attacks/






