Software Supply Chain Attacks: Clear and Present Danger
More than a year after the SolarWinds Sunburst attack and most companies are still exposed to software supply chain attacks.
In a study conducted by Argon Security at Aqua Security, it was found that the majority of companies didn’t implement software supply chain security measures and that most organizations are still at risk.
“Unfortunately, most security teams lack the resources, budget and knowledge to deal with supply chain attacks,” said Eran Orzel, head of Argon’s sales and customer teams. “Implementing strong security over the software supply chain takes time and organizations need to prioritize this now to be able to secure their process and application against the next attack wave.”
In the modern world, one of the hottest targets for cyberattacks are software development supply chains. When attackers launch a supply chain attack, they are throwing a wide net that could affect thousands of companies in a single attack. These attacks also have a big economic impact on the customer-vendor relationships of targeted companies that depend on their cloud security vendors and are trusting the software updates of their software vendors.
Closing the Gaps
The Argon study identified three primary areas of risk affecting software supply chain security posture. Closing these security gaps should be a top priority.
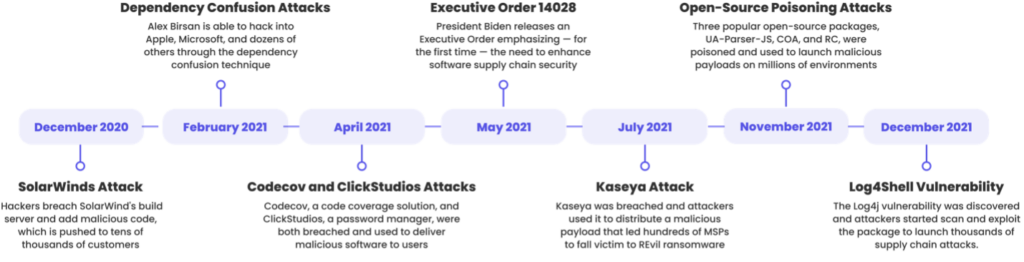
1. Vulnerable Packages: There are two attacks vectors that leverage open source packages. The first is exploiting existing vulnerabilities discovered in open source packages and leveraging them to execute the attack. (Example: The recent Log4j cyberattacks.) The second vector, package poisoning, is more proactive; the attacker takes control of a popular package/public repository and injects malicious code into the open source packages. Developers or pipeline tools then add it as part of the application build process. (Example: us-parser-js package poisoning.)
2. Compromised Pipeline Tools: Attackers can take advantage of privileged access, misconfigurations and vulnerabilities in the CI/CD pipeline infrastructure and get access to development processes to launch their attacks. A compromised tool can expose an application’s source code, enable attackers to manipulate code during the build process and add vulnerabilities to the application (e.g., SolarWinds).
3. Code/Artifact Integrity: Upload of bad code to source code repositories directly impacts the artifact quality and security posture. Common issues that were found in most customer environments were sensitive data in code (secrets), code quality and security issues, infrastructure-as-code issues, container image vulnerabilities and misconfigurations.
Attackers operating in this space are increasingly exploiting weaknesses in the process of developing and deploying software and trying to sabotage it, from code theft to code and process manipulation. Looking at the sharp increase in the number of attacks and the damage they inflicted, current efforts and standard security products cannot block such attacks. Organizations must take a proactive and more modern approach to protect the integrity of their software supply chain process and the security posture of their applications.
Enterprise challenges in securing the software supply chain in 2022 will remain high. The main challenges for AppSec teams, according to security leaders, revolve around:
- Lack of resources, with most AppSec teams understaffed and overloaded without a way to close this gap.
- Insufficient collaboration and coordination with development teams, which is required to implement effective security as part of the software development process.
- Gaps in supply chain security knowledge and expertise, which are required to enable a holistic security program over their development processes and CI/CD pipelines.
- Most companies use traditional security tools that are not designed to address the complexity and dynamic nature of the software supply chain and provide limited capabilities.
Protecting the Software Supply Chain is Possible
Security and DevOps teams need to collaborate in building their software supply chain security strategy and implement automated security within the development process. By adopting new security paradigms and solutions that are designed to secure the software development process against this new wave of sophisticated attacks, organizations can close these security gaps and prevent supply chain attacks.