Lapsus$ Group Exposes Internal Threats Are Also External Threats
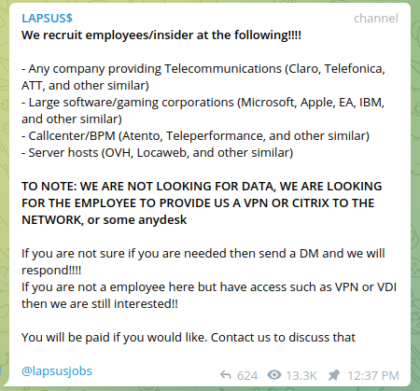 The threat actor known as Lapsus$ Group has recently made the news for targeting and succeeding in their efforts to compromise both Microsoft and Okta. The goal of the attack was to execute what is called a “double-extortion” attack, which exfiltrates data and threatens the organization to expose the data unless a ransom is paid, all the while selling the data privately. This attack also exposed Lapsus$ Group of brazenly attempting to “publicly” recruit employees of their targets to assist them in gaining access to internal networks.
The threat actor known as Lapsus$ Group has recently made the news for targeting and succeeding in their efforts to compromise both Microsoft and Okta. The goal of the attack was to execute what is called a “double-extortion” attack, which exfiltrates data and threatens the organization to expose the data unless a ransom is paid, all the while selling the data privately. This attack also exposed Lapsus$ Group of brazenly attempting to “publicly” recruit employees of their targets to assist them in gaining access to internal networks.
While this isn’t the first time this has occurred, it has typically been done by nation state groups attempting to get access to government employees or contractors. This bold move by a threat actor group has shown organizations that insider threats can rapidly turn into external threats. Security teams must have programs in place to detect, validate, and respond jointly. It also shows that cloud environments are ripe for threat actor groups to target as they are often considered less secure. This is due to lift and shift approaches by vendors to support cloud environments versus purpose-built solutions that can span across any infrastructure.
However, the start of the compromise begins with the changes in today’s workforce and “The Great Resignation” as worker loyalty drops, and employees change job changes more frequently.
Insider Threats Have Increased Dramatically
According to the most recent 2022 Cost of Insider Threats Global Report, Insider Threats cost organizations $15.4 Million annually, up 34% from 2020. Insider attacks are often the most costly information security incidents to any organization. Whether the style of your organization is to discuss and work these issues out in the open, or to handle them in a more confidential manner, there is a critical need to detect insider threats early, identify external exposures and accelerate your response time to identified incidents.
Privileged access is called “privileged” for a reason. However, if the “privileged” are compromised then external threat actors now have privileged access to the same set of resources making it extraordinarily difficult to detect and stop attacks. So how do we identify insider risk, that has the potential to turn into an insider threat and subsequently an external attack?
How to Deal with Insider Risk
In cybersecurity, early detection directly affects your ability to respond to and deal with security incidents. Therefore, it’s imperative that you can immediately detect patterns of behavior that point to indicators of risk.
You may have a collection of security tools in place to protect your organization from known external threats. You may have terabytes or petabytes of log information, but struggle to make sense of it. Maybe you use a SIEM to collect and analyze security events. But how well are these traditional security tools helping you find non rule-based or non signature-based cyber threats, such as the malicious insider?
Traditional cybersecurity tools cannot understand the nuances of changes in user behaviors, privileged access misuse, data exfiltration, communicating externally or even opening doors for external threat actors.
Behavior Analytics Detects Malicious Insider Activity
What’s needed is a new way to examine the vast amount of user behavior in large environments to uncover suspicious activities. User and Entity Behavior Analytics (UEBA) can provide the insight and level of intelligence required to discover, investigate, and remediate real security incidents.
These efforts can be accelerated by working with HR teams and associated applications and infrastructure through a well-designed process for handling insider risk and potential threats. In addition, bringing in identity monitoring and analytics for understanding user access privileges and entitlements is critical to identifying suspicious or malicious activity.
Being able to understand insider risk and risky behaviors before the actual insider threat activity occurs is critical in getting ahead of the situation and preventing data theft, loss, extortion or even ransomware – the latter of which the Lapsus$ group has been engaged in.
Gurucul offers an advanced UEBA solution delivered via machine learning algorithms, investigative tools and scalable big data. Hadoop backends provide the analytical power and security risk intelligence required to protect your organization. In addition, we have pioneered working with identity access management solutions to understand user identity information for monitoring and threat detection purposes through advanced identity analytics. Coupled with our ability to ingest any sort of identity, endpoint, application, network, cloud and IoT information and interpret that data for insider threat risk and activity means that Gurucul is at the forefront of helping security teams with a significant gap in their overall security program.
Attend The Webinar
To learn more about how Gurucul can help you implement or improve your insider threat program and align it with external threat detection programs please attend our webinar. You can get ahead of attacks like those enacted by the Lapsus$ Group.
Upcoming Webinar: Best Practices for Implementing an Insider Threat Program
Date / Time: Thursday, April 14, 2022 at 11:00 AM PDT
The post Lapsus$ Group Exposes Internal Threats Are Also External Threats appeared first on Gurucul.
*** This is a Security Bloggers Network syndicated blog from Gurucul Blog | Security Analytics | Machine Learning Models on Big Data authored by Sanjay Raja. Read the original post at: https://gurucul.com/blog/lapsus-group-exposes-internal-threats-are-also-external-threats




