Home » Cybersecurity » Threats & Breaches » Vulnerabilities » Fixing a vulnerability? Make sure your GitHub isn’t showing too much
Fixing a vulnerability? Make sure your GitHub isn’t showing too much
obfuscated secrets and a $326M crypto hack: are your GitHub commits revealing too much?
When committing software projects to GitHub it remains crucial to ensure that secrets like your private tokens, API keys, and passwords are not accidentally committed to open source repositories as well.
The second aspect of practicing open source hygiene and secrets management is to ensure your GitHub commits don’t reveal too much—for example, details about a critical security vulnerability that is yet to be fixed.
This isn’t malware—just obfuscated secrets
Last week, my friend and data scientist Cody Nash, one of the great minds behind Sonatype’s automated malware detection system, steered my attention towards something suspicious detected by our bots, and rightfully so.
The package ‘infoooze’ touts itself as an OSINT based tool, and otherwise shows no signs of foul play. and yet it triggered an alarm on our system:
The reason you ask? A mysterious “src/secret.js” file that’s heavily obfuscated lurking in the package. The file continues to exist in the latest version of ‘infoooze’ on both GitHub and npm:
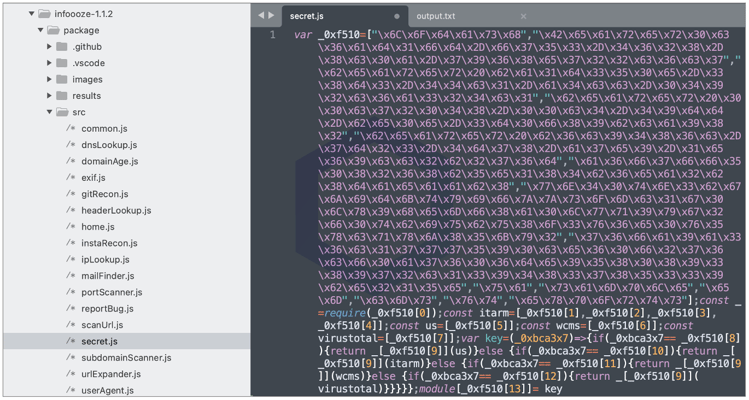
Although JS minification and obfuscation can be used by legitimate packages, time and time again we have seen obfuscation like the one shown above leveraged especially by malicious actors to hide malware in their npm packages.
The OSINT package ‘infoooze’ however retrieves information from intelligence platforms like VirusTotal, and deobfuscating the JS makes it clear that the file, quite literally as its name implies, stores the “secret” keys for the VirusTotal API that the package queries.
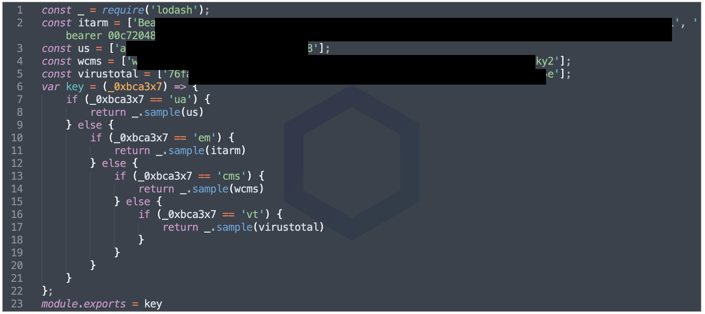
This attempt to achieve security by obscurity falls short as anyone who can decode the scrambled JavaScript can easily retrieve API keys and now use it to make VirusTotal lookups on behalf of the project developers.
Sonatype notified the developer of ‘infoooze’ well in advance (Read more...)
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Ax Sharma. Read the original post at: https://blog.sonatype.com/leaky-secrets-a-326m-crypto-hack-do-your-github-commits-reveal-too-much





