Fighting in Ukraine Raises Prospect of US Cyberattacks
Russian hackers are known as some of the world’s best, and the increase in tensions between the United States and Russia since the invasion of Ukraine has raised the prospect that Russian hackers may target U.S. citizens and organizations with cyberattacks. Our company, INKY Technology, provides cloud-based anti-phishing defense-in-depth to protect against email attacks. While we can’t read our customers’ email, they do report to us through our user interface, and we are in a unique position to see a flow of reports large enough to analyze for trends.
Thus, when Russian soldiers rolled over the borders in Ukraine and the U.S. government started providing aid and support to the Ukrainian side, we expected to see a rise in Russia-based phishing attacks. Most of the time—upward of 90% by some estimates—a major cyberattack is kicked off by a successful phishing exploit. Email—being the lowest common denominator of communications on the internet and designed to allow people who don’t know each other to get in touch—is the weakest link. Well, humans using email are the weakest link, so phishing attacks are crafted to impersonate a trusted entity in an attempt to gain access to organizational networks. Effectively, employees let the bad guys in.
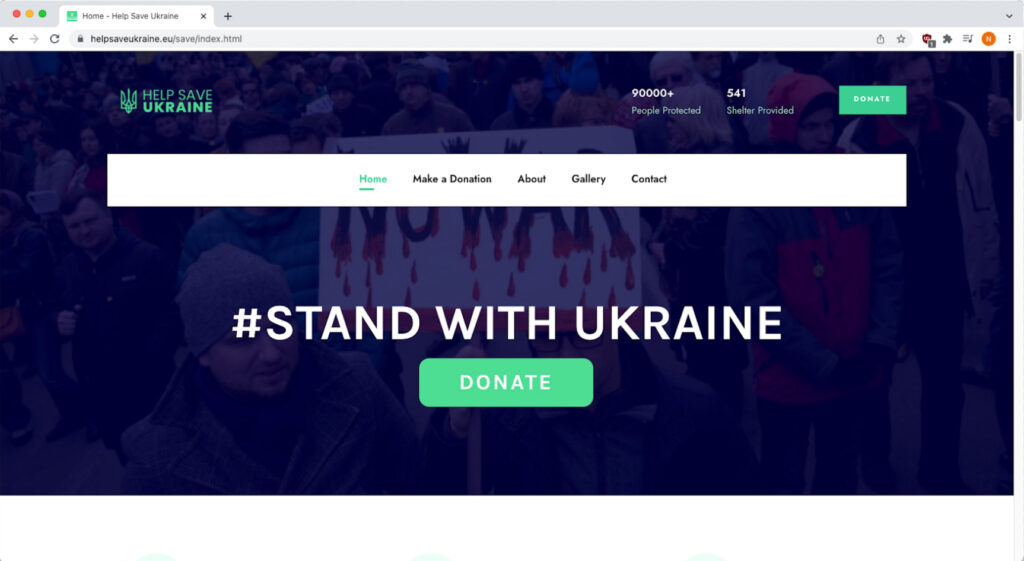
At first, we noticed no increase in traffic from Russian servers, just the usual run-of-the-mill ‘Russian Bride’ spam. Then, an email campaign showed up that impersonated Ukraine president Volodymyr Zelenskyy and asked for donations in cryptocurrency to help the Ukrainian cause. To evade geographic filters, these emails were sent from U.S.-based virtual private servers. With just-slightly-off capitalization and punctuation, the simple text could easily have been created by a non-native-English speaker. Our analysis showed that the various cryptocurrency addresses were real, the donation website had a .eu domain and a slick front page but was rather thin on the supporting pages. This lure came in through several different email vectors, and, at the time of writing, no one had yet been fooled into sending cryptocurrency into the ether, surely never to be seen again.
Since then, we have seen one or two reports involving supposed sales of ‘Support Ukraine’ t-shirt pitches in a fake shop scam with a credential-harvesting payload. We have also detected bad actors posing as Ukrainian victims to solicit donations or investment partnerships.
But, in general, the Russian hacker squad has thus far held off on unleashing a major flood of cyberattacks led by phishing probes. That could change if the United States gets more seriously involved in active warfare on Ukraine’s side. We know the Russians have the capabilities, but we don’t know why they are showing restraint.
During World War II, the German army treated populations in the West very differently from those in the East. They fully expected to exterminate the Slavs and other peoples to the east and take over their farmland, factories and infrastructure. But some generals hedged their bets in the west, just in case they lost the war. By behaving in a seemingly rational way with the French, Belgians, Dutch and British, they left themselves a hidey-hole just in case they needed it. As it turned out, they did and were better treated themselves as a result.
It seems pretty clear that this is Putin’s war and that the Russian people are at least somewhat reluctant participants if they’re aware of what’s going on at all. The general population in Russia may view the west as a potential refuge and don’t want to mess up relationships there unnecessarily. This, perhaps, could explain the restraint shown thus far with regard to cyberattacks. On the other hand, the Russian attackers may simply be awaiting Putin’s order. Time will tell.
Meanwhile, it’s in everyone’s interest here in the United States to harden their installations against such attacks. Such defense will come in handy even if the attack flow never rises above the usual commercial forays, which are always in season.