7 Cloud Security Trends That May Impact Your Cloud Security Planning
What is changing in cloud security, and how should CISOs and IT teams prepare? One way to answer these questions is to, as you surely do already, stay up to date on the industry’s analyst reports and thought leadership publications. Another way is to check out search trends, as they are great indicators of undercurrents and shifts in mindset.
This is exactly what we cover in this blog post. We looked at the leading topics in cloud security and analyzed their search volume trends over the past year (2021) and four years past (2018 – 2021). Below are seven interesting trends we discovered.
1. AWS and Azure are the Leading Cloud Providers
Among the three largest cloud providers – Amazon Web Services, Microsoft Azure and Google Cloud Platform – “AWS” and “Azure” are the two most searched for terms, while GCP lags far, far behind. This corresponds somewhat to their market share — AWS at 32%, Azure at 19% and GCP at 7% (as of Q1 2021, according to research firm Canalys).

It’s interesting to note that 2021 was the first year in which “Azure” searches exceeded “AWS” searches. This is aligned with growing Azure adoption among IT teams.
This shift to Azure could be due to many reasons, but one may well be the rapid advance of more enterprises through digital transformation and “cloudification” of their infrastructure. Since Microsoft is often the chosen suite for enterprises, the transition to Azure is a natural one, and possibly more cost-effective. Other reasons may include Azure’s capabilities, pricing and marketing.

How to prepare: Whichever cloud provider you are using, you are not married to it. It’s good to have options. Research other cloud providers and see how they might answer different needs you have. Whichever you choose to adopt, make sure you have the security details fleshed out, and especially what the cloud provider is responsible for and what you are responsible for (a.k.a. the provider’s “shared responsibility model”). Read more here for GCP security, and here for AWS security. Also, be sure your cloud security tools support a multicloud model.
2. DevOps Became Stronger Than SREs
SREs (Site Reliability Engineers) are the employees who are in charge of implementing services that support IT. They make sure systems and tools run smoothly from an operational aspect. DevOps (Developer Operations), a role somewhat similar to SREs, focus on the operations of software delivery pipelines, while making sure the pipelines are continuous and automated.
In 2019, the search volume for “DevOps” exceeded the “SRE” search volume, although “SRE” remained relatively high. This change could be due to the acceleration of cloud adoption and shift left trends, alongside development of more advanced automation technologies. As we build and deliver more software faster, there is a growing need for DevOps and explosive growth in that cloud area. This search trend may also flag the cloud expertise gap that many organizations are already aware of: not enough skilled DevOps professionals to meet demand.

It’s interesting to note that “DevSecOps” and “Cloud Architect” do not have high or increasing search volumes. These roles may be on the wane – as is rumored to be the case for DevSecOps – or the lack of strong interest may indicate that widespread cloud adoption and pursuit of such roles is yet to come.
How to prepare: On a personal-professional level, whether you are a DevOps engineer, an SRE engineer or an engineering team manager, the important thing to do is brush up on skills that cloud teams need today and in the future. Learn about and get certified in automation, CI/CD and cloud security to make yourself invaluable to your organization and of great value to the market. As an organization, focus on cloud security tools that are credibly endorsed for reducing workload through automation, simplicity and visibility.
3. “Cloud Security” is Gaining Traction in the US
The adoption of the public cloud as a means for scaling infrastructure, platforms and applications has also introduced new security concerns. Cloud misconfigurations, cloud ransomware and risky cloud cloud IAM are just some examples of potentially catastrophic cloud security risks.
As they become aware of or even experience these potential cloud security vulnerabilities, security and IT teams may be searching for information on what these risks entail and how to protect their organizations against them. At least, this is what may be surmised from the gradual uptick in search volumes of “cloud security” in the US.
It’s also interesting to see that the “cloud security” search volume trend is fairly aligned with the search volume trend for “cloud computing” (their ebbs and flows are pretty much aligned). This might indicate that whoever is looking for cloud security is also interested in cloud adoption. However, the gap in the search volume also shows that not all cloud adopters immediately think of security.

How to prepare: Cloud security should go hand in hand with cloud adoption. For every cloud computing action that you take, make sure to find out the security aspects of it, and to choose the right tools and vendors that will help secure your organization.
4. CIOs are Stronger Than Any Security Role
Despite what many of us in the cybersecurity industry might think, not everyone thinks or dreams (we’re not judging…) about security vulnerabilities. Compared to the CIO role, search volumes on security roles presented as very low.
We compared CISOs to CIOs, cloud engineers, cloud architects and security engineers:
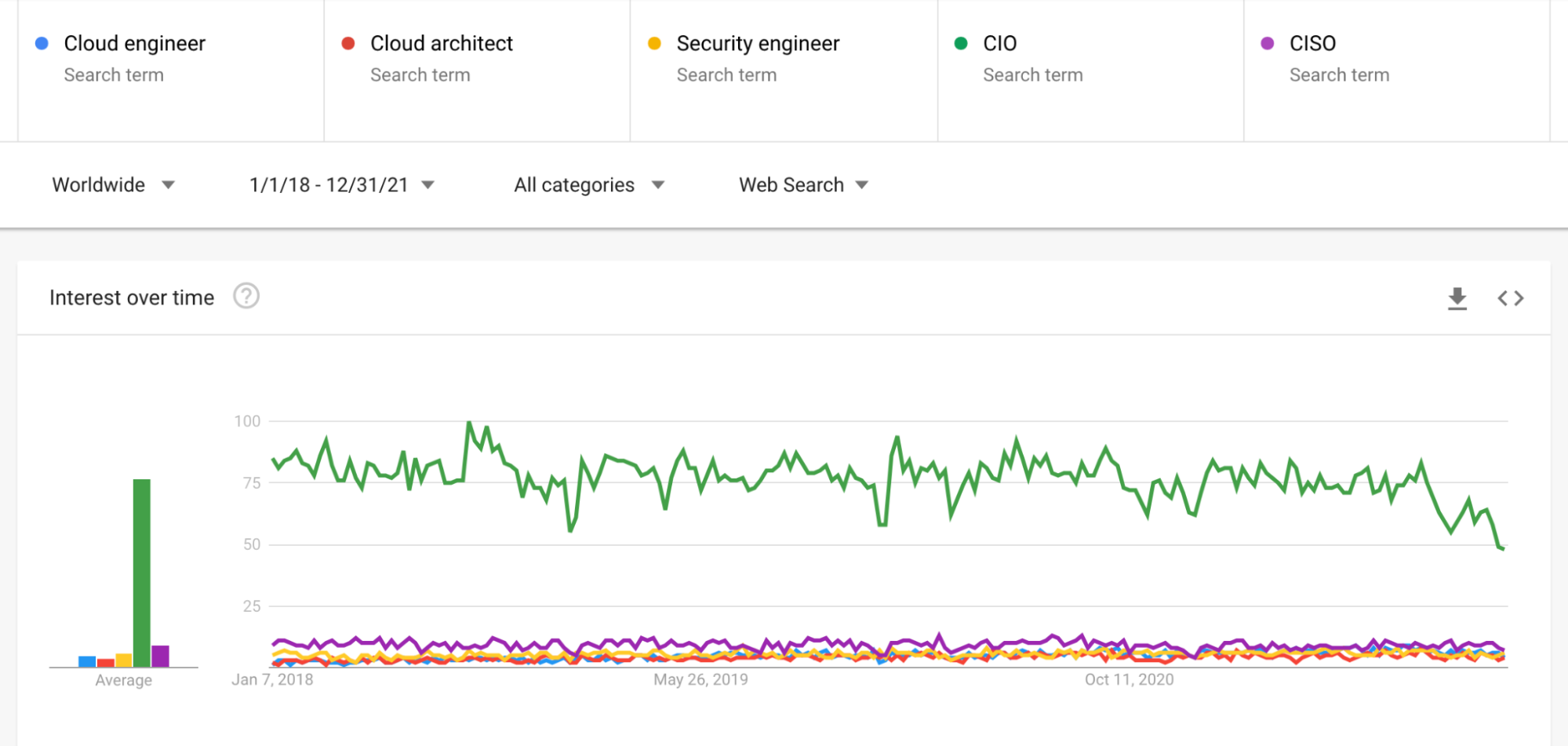
This could mean that CIOs still have more power and leverage in the enterprise, and that their impact in organizations is bigger. It could also show that while many organizations have CIOs, the security role is still emerging and not all organizations have caught up to recognize its value.
How to prepare: If you’re a security person and want to lead processes in your organization, here’s how to get started to make an impact.
5. Interest in Cloud Security is Growing
Network security is the security of legacy infrastructure, usually on-premises servers. Cloud security is the security of agile, cloud infrastructure – and includes security across cloud identities, network, data and compute resources. While interest in network security has been fairly stable over the past years, interest in cloud security is growing.
The closing of the gap is a good indicator of progress in digital transformation execution, with more companies moving to hybrid cloud or a cloud-native infrastructure. We predict that this gap will close in the upcoming year, and that in 2023 interest in cloud security will surpass network security.
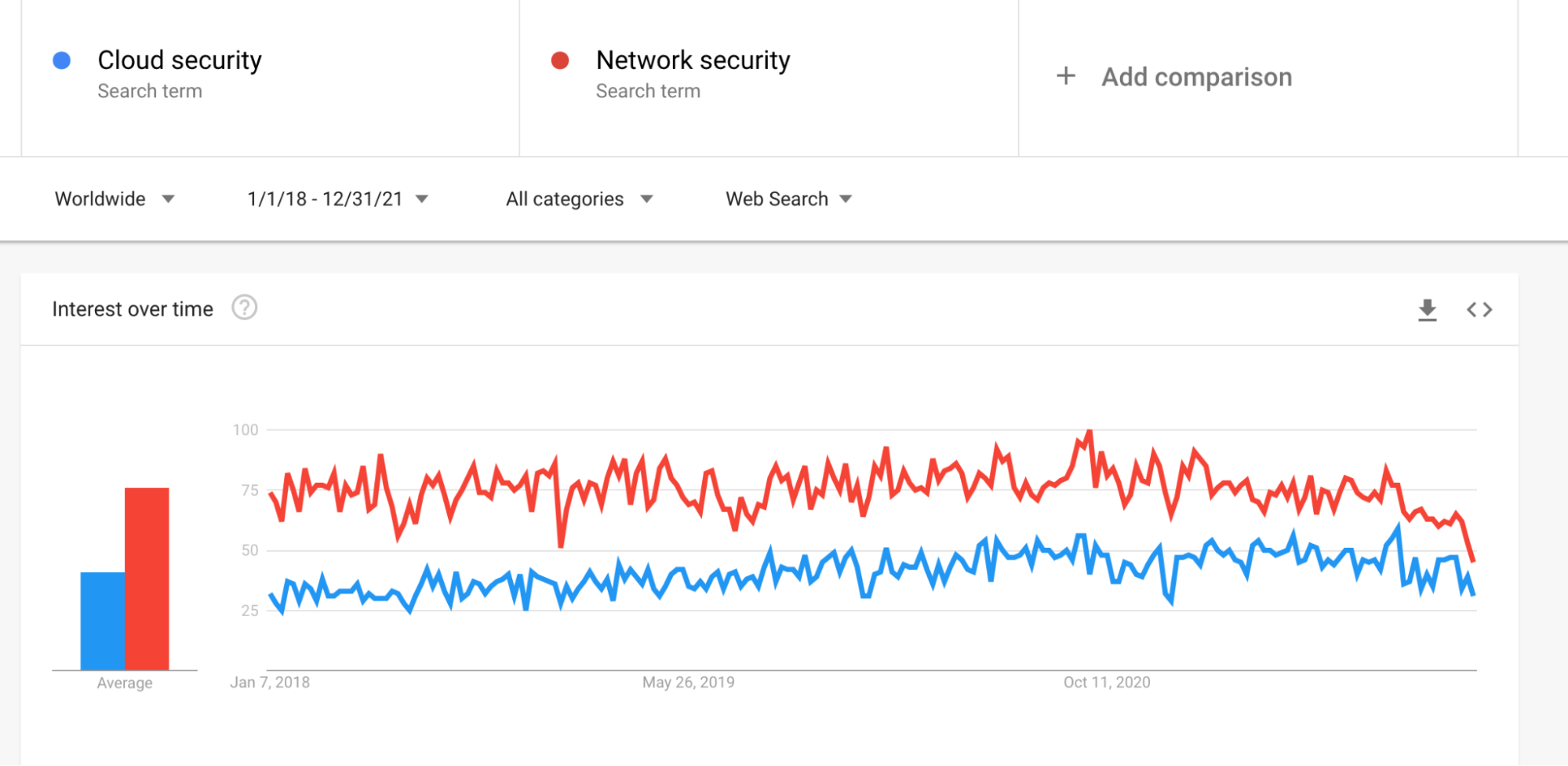
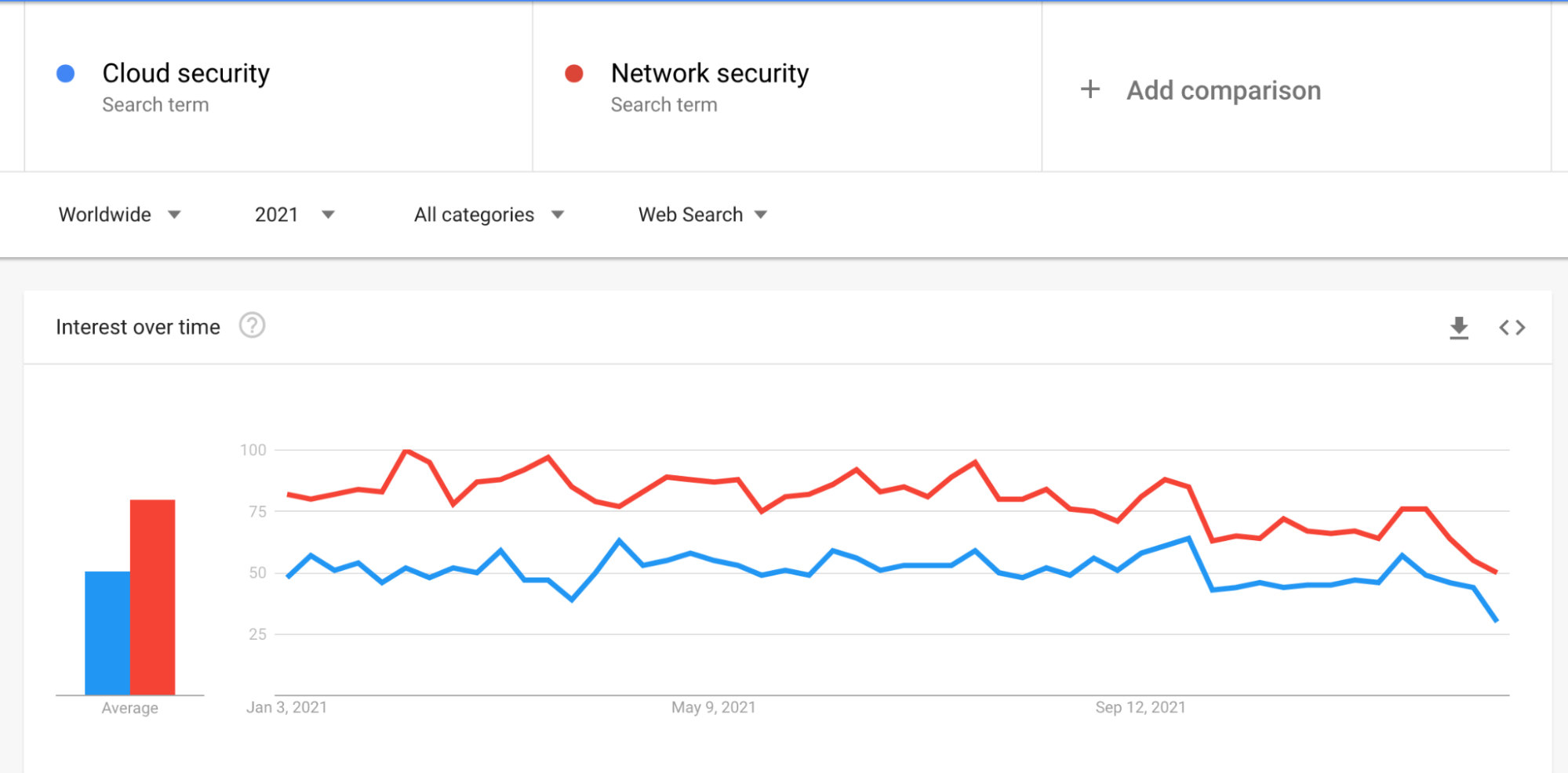
How to prepare: If you are involved with your organization’s IT infrastructure and/or shift to cloud:
- Stay on top of cloud security trends and requirements, and incorporate them in your plans and company updates.
- Introduce cloud security as an invaluable component of the business strategy.
- Keep teams close together, as IT and security are becoming more and more interlinked, and suggest processes for collaboration and removing silos.
6. CIEM is the Most Interesting Recent Gartner Cloud Category
Cloud Infrastructure Entitlements Management (CIEM) is one of the more recent Gartner cloud categories. It describes a set of technologies that monitor human and service identities, permissions, and activity, continuously analyzing risk and generating least privilege access policies.
We compared CIEM to other Gartner categories:
- Cloud Security Posture Management (CSPM) – the set of technologies that determine that cloud applications and services are securely configured.
- Cloud Workload Protection Platform (CWPP) – the set of technologies that discover and secure cloud workloads.
- Cloud-Native Application Protection Platforms (CNAPP) – a new cloud security approach defined by Gartner that emphasizes the need for unified lifecycle security as opposed to a patchwork of solutions. CNAPP solutions include CIEM, CSPM and more.
We found very high search interest in CIEM in 2001, surpassing the more familiar CSPM.
Why is this? Entitlements determine the blast radius upon a breach, making them the most urgent cloud security threat. As IT and security teams realize the difficulty of managing cloud identities, they are probably looking for a CIEM solution for help with visibility, access governance and least privilege.

How to prepare: Take the cloud IAM and identity management security burden off your plate by incorporating CIEM solutions that can provide you – and teams across security, devops and IAM – with visibility into excessive permissions, and risk prioritization and automated remediation.
7. Interest in Ransomware Grows with High Profile Attacks
The number of ransomware attacks grew in 2021, alongside demands for higher ransoms. On Google, high-profile attacks were accompanied by significantly higher search volumes. This likely suggests greater awareness and a sense of vulnerability around ransomware, prompting greater interest.
In the chart below, we can see search volumes for “ransomware” throughout 2021. It’s fairly safe to assume that the peaks from April to July are related to the huge Colonial Pipeline attack (May 2021), the JBS attack (which came to light in June 2021), the Kaseya VSA attack (July 2021) and the Kronos attack (December 2021).


How to prepare: There are multiple solutions that can help prevent ransomware attacks, each targeting different angles. From a cloud infrastructure perspective, misconfigurations could lead to exposure that is vulnerable to ransomware attacks.
Conclusion
Google Trends is a good indicator of, well, trends, and helps security professionals and stakeholders — including cloud security, IAM managers, CISOs, CIOs, cloud engineers and DevOps — keep their finger on the pulse of what is changing in the industry. We’ve highlighted here a few main trends that we spotted. Many reflect what we’re seeing in the industry and as experienced by our customers as they scale their cloud use and seek to reduce its risk.
If you have questions, or interest in other cloud security trends you’d like us to explore, feel free to contact us on Linkedin or Twitter, or drop us a line.
The post 7 Cloud Security Trends That May Impact Your Cloud Security Planning appeared first on Ermetic.
*** This is a Security Bloggers Network syndicated blog from Ermetic authored by Ermetic Team. Read the original post at: https://ermetic.com/blog/cloud/7-cloud-security-trends-that-may-impact-your-cloud-security-planning/



