When Every Day Is Valentine’s Day: How Threat Actors Prey on Lonely Hearts
Love in the time of threat actors
Theoretically, there isn’t anything wrong with Valentine’s Day. But let’s just say it like it is: Nobody likes Valentine’s Day, a guileless push for capital, like Halloween for the heart.
To be fair, some people do, but we feel it’s safe to say that most people, single or otherwise, view the “holiday” as an overwhelming 24-hour period during which love is expected to be shown, manifested, proven. But what of the other 364 days? What about the pull of the heart throughout the entire year?
Those days—including Valentine’s Day—are for the romance scammers.
Romance fraud: The high cost of love and lust
Cybercrime fraud schemes are commonly aimed at love, dating, romance, sex, and other matters of the heart, body, mind, and soul; for threat actors, hearts are meant to be broken, leveraged for gain.
In 2020, romance and confidence scams ranked in the top 10 recorded complaints from the FBI’s Internet Crime Complaint Center (IC3), with 23,751 recorded victims. Victim losses for romance scams exceeded $600 million—second only to Business Email Compromise / Email Account Compromise (BEC/EAC).
Whoever said you couldn’t put a price on love?
What is a BEC scam and what damage can it do?
As we’ve detailed before, BEC scams typically begin when a threat actor sends a victim an email—asking for a large sum of money to be sent to a foreign account—that appears as though it were sent by an executive who works at the same organization as the victim. In the context of Valentine’s day, sometimes the premise of these emails is romance: a BEC attacker may fool their “lovers” by asking them to open an account for them, and fund it. In any instance, money given is likely money lost.
Believe it or not, the way to someone’s heart is also a potential path into the heart of an organization: its data and assets. Unlike malware, BEC scams are tougher to pin on a single entity, such as a threat actor group that infects an organization’s system with malware.
Organization’s should invest in educating their employees in how to spot—and report—BEC scams, which can significantly harm a company in multiple ways.
Furthermore, as we’ll detail below, organizations should invest in a threat intelligence tool that enables them to monitor the latest attack techniques, educate their employees, and make us all safer by better defending both our computers and our people against cyber threats. (Also, accessing someone else’s account isn’t nice—like surreptitiously reading a text or an email on a partner’s phone.)
Read more: BEC: All We Need is Love and Mules
ILOVEYOU, YOULOVEME
The May 2000 ILOVEYOU virus was a tangible reminder that the heart is an enormous infection vector. Also known as the “Love Bug,” or “Love Letter for you,” the malware hid as an attachment in an email with the subject line ILOVEYOU. Upon opening the attached “love note,” the malware proceeded to spread through the victim’s computer, overwriting files, and spreading the love by infecting the victim’s contacts.
The Love Bug is known as one of the most destructive cyber attacks in history, causing billions of dollars worth of damage.
Common romance-themed TTPs
Dating fraud: Looking for love in all the wrong places
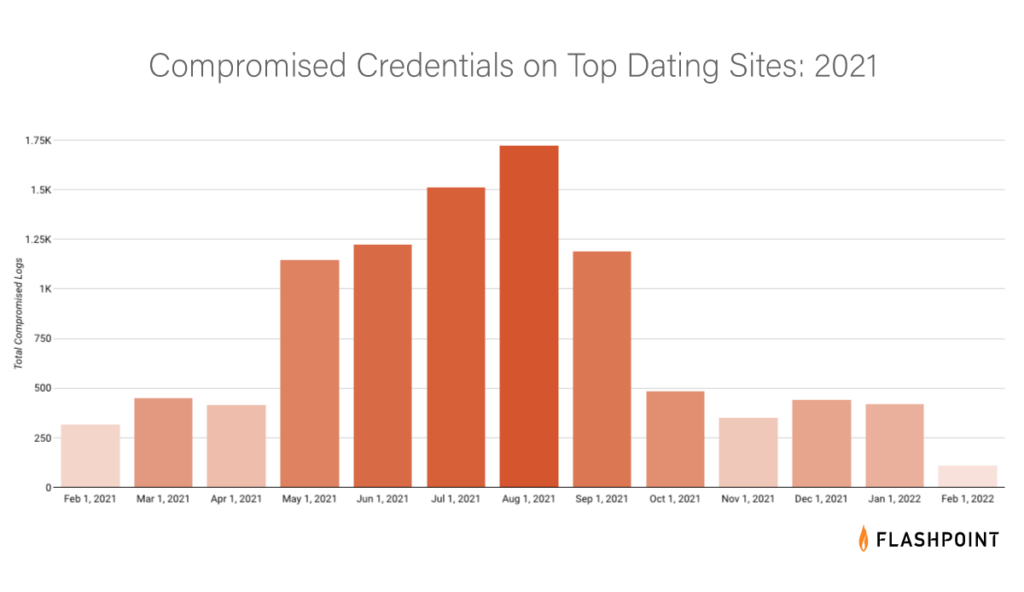
In 2015, attackers breached the extramarital affairs website Ashley Madison, leaking details from the user accounts. This is typically understood as one of the larger breaches of user information from a dating website.
In Flashpoint’s Compromised Credential Monitoring (CCM) solution, analysts identified a large number of accounts that were compromised through dating websites. The credentials appear to be predominantly sourced from breaches of dating sites, or victims whose credentials for dating sites had been captured by common strains of commoditized infostealer malware.
Plenty of phish
A look through your spam folder should indicate how much “love” (or “lust” rather) are continuing to be used in phishing lures. Thankfully, spam filters have gotten a lot better at catching these types of attacks, and users have (ideally, fingers-crossed) gotten better at recognizing these types of attacks.
It is easy to ignore phishing emails, since they are typically accompanied by spelling errors, weird email addresses, and services that do not interest us. But what about when the threat actor is sliding into your DMs with a seemingly realistic profile, and an attractive image to boot.
Related reading: BEC Campaigns Target Organizations Across Sectors Using Credential Phishing
What is catfishing? Love bombing for gain
Catfishing is a type of social engineering attack where a threat actor may pose as someone else, typically through a collection of stolen images and a semi-compelling backstory. The fraud will typically include a barrage of compliments and proclamations undying adoration—dubbed “love bombs”— culminating in a request for money. The catfish aims to hook the victim before asking for a loan, or an advancement payment to cover some unforeseen cost.
What is eWhoring? Explicit picture packs
Other less glorious forms of this attack may involve requesting money for sexual or gratitutious images while involved in a virtual sexual encounter (formerly known as “cybersex” or just “cyber”). Threat actors will typically sell packs of images that are being used in sexual encounters, dubbed “eWhoring.”
While these image packs can be used as part of a catfish scam, typical eWhoring skips the courting phase and goes straight to payment. These images are sourced (or coerced) through social engineering, consensual eWhores, non-consensually through “revenge porn,” or customization from images stolen from existing websites.
On a related note, leaked or brute-forced credentials from pornography sites comprise a large portion of cracked accounts for sale on illicit communities. If the victim is re-using their password, then it could potentially expose both their personal or professional log.
Detect, prioritize, and mitigate cyber risks with Flashpoint
Never miss a development across illicit communities and protect your assets, stakeholders, and infrastructure by identifying emerging vulnerabilities, security incidents, and ransomware attacks. Sign up for a free trial and see Flashpoint’s extensive collections platform, deep web chatter, and dark web monitoring tools in action.
The post When Every Day Is Valentine’s Day: How Threat Actors Prey on Lonely Hearts appeared first on Flashpoint.
*** This is a Security Bloggers Network syndicated blog from Blog – Flashpoint authored by Jonathan Zalman. Read the original post at: https://www.flashpoint-intel.com/blog/valentines-day-scams-and-threats/





