Law enforcement pressure forces ransomware groups to refine tactics in Q4 2021
Table of Contents
When the history books on ransomware are written, 2021 will be viewed as a red-letter year in the evolution of the fight against cyber extortion. Although there are no silver bullets in this fight, it DOES feel like a number of positive developments have aggregated noticeable pressure on the rise of ransomware attacks. As discussed on prior write-ups, we attribute this to the confluence of four factors:
-
The Biden Administration’s executive orders to implement zero trust are hardening US government agencies security and the vendors that support them.
-
The pipeline incident of last spring is still seared into the minds of enterprise CEO’s and has driven a renewed push for better security and better incident preparedness.
-
The cyber insurance renewals process is structurally mandating better security and continuity in order to maintain policies. These three factors have raised awareness and hardened corporate environments, making attacks more expensive for ransomware actors to carry out.
-
The fourth factor has likely caused the biggest change to the ransomware landscape. A number of dramatic law enforcement takedowns, seizures and arrests spiked in Q3 and Q4, and the momentum carried through in 2022. Most notable was the arrest by the FSB of alleged members of REvil. This was an unprecedented action for the Russian government to take and has surely increased the risk profile of being a ransomware affiliate. This decreases the addressable market of cyber criminals willing and able to execute these attacks, as not all of them are willing to risk jail time or western extradition for the money they earn.
These four factors combined mean that the cost and risk of executing ransomware attacks are up, and if this trend continues we expect to see the aggregate volume of attacks begin to decrease.
Average Ransom Amount up Sharply in Q4 2021
Average Ransom Payment
$322,168
+130% from Q3 2021
Median Ransom Payment
$117,116
+63% from Q3 2021

Average and median ransom payments increased dramatically during Q4, but we believe this change was driven by a subtle tactical shift by Ransomware-as-a-Service (RaaS) operations that reflected the increasing costs and risks previously described. The tactical shift involves a deliberate attempt to extort companies that are large enough to pay a ‘big game’ ransom amount but small enough to keep attack operating costs and resulting media and Law Enforcement attention low.
The proportion of companies attacked in the 1,000 to 10,000 employee count size increased from 8% in Q3 to 14% in Q4. The average ransom payment in just this employee bucket was well north of one million dollars, which dragged the Q4 average and median amounts higher. We expect this trend to continue as RaaS operations seek to evade the attention of Law Enforcement while still growing their operations. During a rare interview, when asked about the wisdom of the pipeline attack, a LockBit2.0 affiliate was quoted saying:
“You can hit the jackpot once, but provoke such a geopolitical conflict that you will be quickly found. It is better to quietly receive stable small sums from mid-sized companies…”
This tactic is supported by the subtle but noticeable shift in the size of victims and the effort by RaaS groups to avoid attention from Law Enforcement.
84% of Ransomware Attacks Included Data Exfiltration
Data exfiltration remains a popular tactic among the majority of RaaS groups and affiliates. RaaS affiliates expect exfiltrated data to act as further motivation for victims to pay a ransom, however we routinely see reasons why data exfiltration is not a compelling reason to pay a cyber extortion demand. Some examples we witnessed in Q4 provide proof of why paying to suppress news of a leak remains a bad strategy for victims of data theft extortion:
-
Lockbit: The loose affiliate structure of Lockbit has resulted in a tangible lack of consistency in how stolen data is handled. Lockbit affiliates rarely provide tangible proof of data exfiltration and often fail to provide any proof of deletion of logs of stolen data if paid. All the more reason not to pay them!
-
Conti: The Conti group is extremely large, and the level of organizational miscommunications that occur is evident. During Q4, victims of Conti had their data posted to the Conti leak site despite paying for that NOT to occur. We also witnessed data posted by accident multiple times.
-
Hive: This group has had multiple affiliates defect and take copies of the stolen data with them. The defecting affiliates than attempt to extort the victim a second time or offer to subvert their own organization to destroy the stolen data. Regardless of what is actually happening, the instability of this RaaS operation’s affiliates demonstrates that safe custody, secure deletion, and non-proliferation of stolen data are not deliverables that should be counted on, let alone paid for.
-
Karakurt: On multiple occasions, this group provided victims ‘proof’ of exfiltration files that belonged to a completely different company. This lack of care and hygiene demonstrates that safe custody of stolen data is not a concern of threat actors.
The Most Common Ransomware Variants in Q4 2021
| Rank | Ransomware Type | Market Share % | Change in Ranking from Q3 2021 |
|---|---|---|---|
| 1 | Conti V2 | 19.4% | – |
| 2 | LockBit 2.0 | 16.3% | +2 |
| 3 | Hive | 9.2% | +5 |
| 4 | Mespinoza | 4.1% | -2 |
| 5 | Zeppelin | 3.6% | +1 |
| 5 | BlackMatter | 3.6% | +4 |
| 6 | Karakurt | 3.1% | New in Top Variants |
| 6 | Suncrypt | 3.1% | +2 |
| 6 | AvosLocker | 3.1% | New in Top Variants |
Top 10: Market Share of the Ransomware attacks
The most active RaaS groups continue to be responsible for the majority of ransomware attacks. The Ransomware-as-a-Service model is likely to continue its evolution in 2022, with pressure from Law Enforcement being a major driver of RaaS ‘innovation’. While all RaaS operations need to recruit affiliates, we expect groups to become more reserved in their public messaging and more careful about what companies they target. The lessons learned from the pipeline attack and the recent FSB arrests are likely to keep some of the more vibrant displays of public bravado in check. The increase of law enforcement takedowns, seizures, and arrests in 2021 provided ample evidence that the world’s law enforcement agencies are stepping up their efforts. We expect RaaS operations to try and mitigate the size of the targets on their back to the extent possible.
MITRE ATT&CK Tactics Observed in Ransomware Attacks in Q4 2021
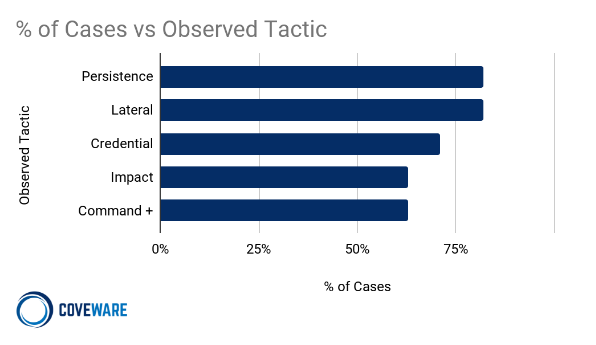
In addition to statistics about threat actor behavior, Coveware aggregates data about the cyber criminals’ tactics, techniques and procedures (TTPs) leading up to the ransomware deployment. These TTPs are collected first hand by Coveware and mapped to the MITRE ATT&CK framework for standardization. The top 5 MITRE TTPs in Q4 were (note we exclude Impact TA0040 from this list as some form of impact is observed on all attacks):
-
Persistence (TA0003): 82% of ransomware attacks had persistence TTPs observed, an increase of 34% points from Q3. Persistence TTPs allow adversaries to keep access to systems despite system restarts, credential changes, or other interruptions that could disrupt their access. Techniques used for persistence include any access, action, or configuration changes that let them maintain their foothold on systems, such as replacing or hijacking legitimate code or adding startup code. The most common sub tactics being: Scheduled Task/Job (T1053) observed in 31% of cases and Create Account (T1136), observed in 39% of cases. Scheduled tasks were leveraged by a handful of groups including Conti, Suncrypt, and Lockbit2.0. The tactic allows malware to remain on the network and continuously run after the initial deployment.
-
Lateral Movement (TA0008): 82% of ransomware attacks involve lateral movement with the most common types being Remote Services (T1021) observed in 39% of cases, Exploitation of Remote Services (T1210) observed in 38% of cases, and Lateral Tool Transfer (T1570) observed in 23% of cases. Lateral Movement consists of techniques used to enter and control remote systems on a network. The primary objective of broad ransomware deployment requires exploring the network to identify and control critical systems. Adversaries might install their own remote access tools to accomplish Lateral Movement or use legitimate credentials with native network and operating system tools, which may be stealthier.
-
Credential Access (TA0006): 71% of ransomware cases observed Credential Access tactics via either Brute Forcing (T1110) observed 78% of the time or OS Credential Dumping (T1003) observed 22% of the time. Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include keylogging or credential dumping. Using legitimate credentials can give threat actors access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.
-
Command and Control (TA0011): 63% of ransomware attacks observed some form of Command and Control with Remote Access Software (T1219) being the most common tactic. This tactic consists of techniques that adversaries may use to communicate with systems under their control within a victim network. Adversaries commonly attempt to mimic normal, expected traffic to avoid detection. There are many ways an adversary can establish command and control with various levels of stealth depending on the victim’s network structure and defenses. Ransomware threat actors are regularly using legitimate remote access software to maintain an interactive session on victim systems. The most common legitimate services observed were AnyDesk, TeamViewer, LogMeIn and TightVNC.
-
Collection (TA0009): Collection tactics were observed on 61% of cases, with Archive Collected Data (T1560) being the most common. Collection consists of techniques adversaries may use to gather information that are relevant to the adversary’s objectives. Frequently, the next goal after collecting data is to steal (exfiltrate) the data. Common target sources include various drive types, browsers, audio, video, and email. Common collection methods include capturing screenshots and keyboard input.
The Most Common Ransomware Initial Ingress Vectors in Q4 2021

While abusing weakly configured RDP connections and malicious phishing emails remain a ubiquitous threat, software vulnerabilities have been an increasingly exploited vector by ransomware actors. We attribute the growth to the increased specialization and segmentation of the cyber extortion ecosystem. Network access brokers have become a threat actor segment that focuses solely in ingress and will often specialize in certain types of broadly installed appliances or software. This specialization allows them to not only exploit these vulnerabilities quickly, but to capitalize on unique skill sets and knowledge they may have developed. The mass harvesting of credentials post exploit is then monetized further downstream to ransomware groups. Patterns in ransomware groups, and specific ingress CVE’s, are often a function of where ransomware groups shop for access vs. any specialty they may have themselves. The top 3 CVE’s we observed being exploited during ransomware attacks in Q3 were:
CVE-2021-34473 and CVE-2021-26855: The top 2 most exploited vulnerabilities were Microsoft Exchange vulnerabilities that allowed for remote code execution (RCE) by an attacker.
CVE-2018-13379: The third most common vulnerability observed was an issue with Fortinet firewall appliances that allows unauthenticated attackers to download system files via special HTTP resource requests.
The Most Common Industries Impacted by Ransomware in Q4 2021

Ransomware continues to be a crime of opportunism, not specific targets. We do expect RaaS operations to attempt to be more selective in their attacks so as to avoid disrupting some systemically important companies and thus drawing the ire and attention of Law enforcement. That being said, we have not seen these groups demonstrate the actual ability to understand and underwrite what companies are systemically important and which companies are not.
Ransomware Victim Size in Q4 2021
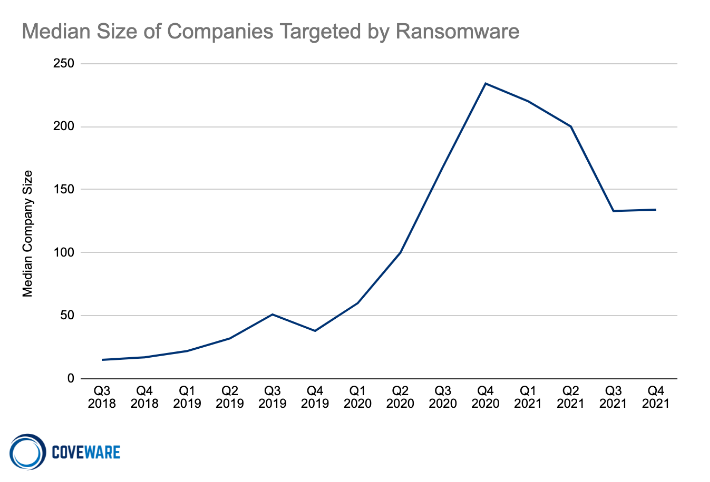
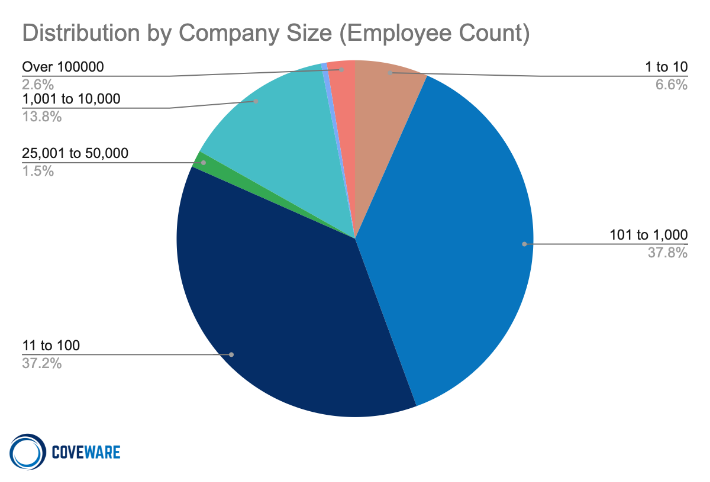
The median victim size in Q4 2021 remained relatively flat, with about 133 employees. The average employee counts, though, in Q4 was 8,650, demonstrating the dramatic skew in the distribution curve. Although medium and large organizations continue to be impacted, ransomware remains a small business problem with 82% of attacks impacting organizations with less than one thousand employees.
While subtle, the largest shift in Q4 was within the mid-market, where companies with 1,000 to 10,000 employees jumped from 8% of attacks to 14% of attacks.
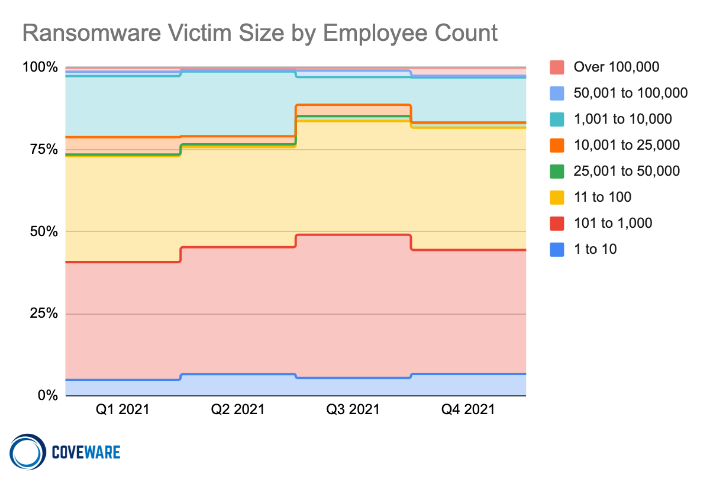
We expect the focus on mid-market companies to continue as RaaS operations target companies large enough to attempt a large ransom demand, but small enough to not attract too much attention from Law Enforcement.
Cost of Ransomware Business Interruption
The average case duration in Q4 2021 was 20 Days (-9% from Q3 2021). This decrease is attributable to an increase in the number of companies that were able to recover from backups, which is ALWAYS faster than attempting to decrypt data with a threat actor decryptor. The cost of business interruption remains the most serious cost to organizations that are impacted by ransomware.
*** This is a Security Bloggers Network syndicated blog from Blog | Latest Ransomware News and Trends | Coveware authored by Bill Siegel. Read the original post at: https://www.coveware.com/blog/2022/2/2/law-enforcement-pressure-forces-ransomware-groups-to-refine-tactics-in-q4-2021




