How to Use Dynamic Enforcement to Prevent Bots From Abusing MFA
Dynamic enforcement refers to adaptive challenges that interact with risky users in the ‘gray’ area to stop automated attacks and resurrect good users, if any. Combining dynamic enforcement with their existing risk engines, businesses can prevent bots and automated scripts from abusing the costly MFA flows
Cybercrime is a ‘profit-making business’ with attacks not only growing in volumes and sophistication but also becoming increasingly unpredictable and difficult to detect. Digital accounts are now aplenty, so is the availability of consumer information – thanks to numerous and frequent incidents of data breach. Leveraging the expertise and support from the cybercrime ecosystem and using easily available commoditized tools, attackers are having a field day, taking advantage of the enormous opportunities to attack.
A peep into the business of cybercrime
At Arkose Labs, we have seen a significant jump in the volumes of attacks. What is even more baffling is the sophistication of tools and techniques that attackers have come to use. The ‘business’ of cybercrime is run like any other SaaS enterprise, complete with marketplaces where one can easily find commoditized tools to launch a targeted attack at scale.
The availability of cloud infrastructure is an added advantage to the attackers much like it is for digital businesses. However, unlike these businesses, attackers need not worry about integrating platforms – they are already connected to a thriving cybercrime ecosystem. They work as a distributed team, albeit with no accountability. For every attack that gets detected or reported, there are several others where these attackers escape unpunished.
Another intriguing observation from our network is the type of audiences. They are spread across geographies and demographics. They use a variety of devices across platforms that go well beyond the web or mobile to televisions, consoles, gaming devices, and more. This overall visibility into the attack types, targets, tools, and the underlying motivation gives us important insights into developing a fraud defense solution that actually works.
MFA is effective, but also has downsides
An effective solution to prevent bots is pretty much available in the form of a second factor, which is often used in MFA (multi-factor authentication). A consumer receives an SMS or OTP on the phone, email, or an associated app, and uses it for authentication. Increasingly, businesses are integrating MFA into their authentication mechanisms and even consumers are becoming comfortable using it, especially for high-value transactions. However, what looks like a straightforward process of sending an additional code to a user, who then uses it for authentication, is after all not that simple.
MFA has its own downsides. It requires businesses to make significant investments to deliver codes via SMS, OTP, email, and so forth. They may incur anywhere between $15 and $25 to manage the process when a customer calls up for non-receipt of the passcode. Plus, businesses have to deal with varied levels of user savviness – there are many users who may need assistance using those codes.
Then there are code delivery challenges – the user may be in a region where the code doesn’t get delivered or takes too long to deliver. In the latter case, the validity of the passcode may expire by the time it’s delivered. In the meantime, the user may initiate another request for a code. The user inputs the expired code which doesn’t work, leading to an ensuing chaos and consumer frustration.
Using RBA to overcome MFA-related challenges
To tide over the challenges and ascertain the need for an MFA flow for a user, many businesses are trying to implement risk-based authentication (RBA). While RBA can be useful in warding off simple script attacks, it is not enough for complex attacks. Attackers are using sophisticated tools and leveraging headless browsers to launch attacks that are becoming increasingly imperceptible.
This is where RBA-based risk decisioning leads to a trade-off between precision and recall as the risk score does not qualify clearly as ‘trust’ or ‘mistrust’, leading to a growing gray area. Should a fraud team decide to implement stricter authentication, it may catch a little bit of additional fraud, but lack of operational support for a higher rate of challenges may prevent it from addressing additional customer queries across multiple service channels.
Furthermore, the RBA-only process lacks a real-time challenge response feedback loop that can inform the decision engine whether the user passed the MFA or not. In the absence of this feedback, the risk engine cannot adapt and policies remain unchanged.
Businesses, therefore, need a different approach that not only allows them to deal with this growing gray area, but also saves them from using the MFA flow.
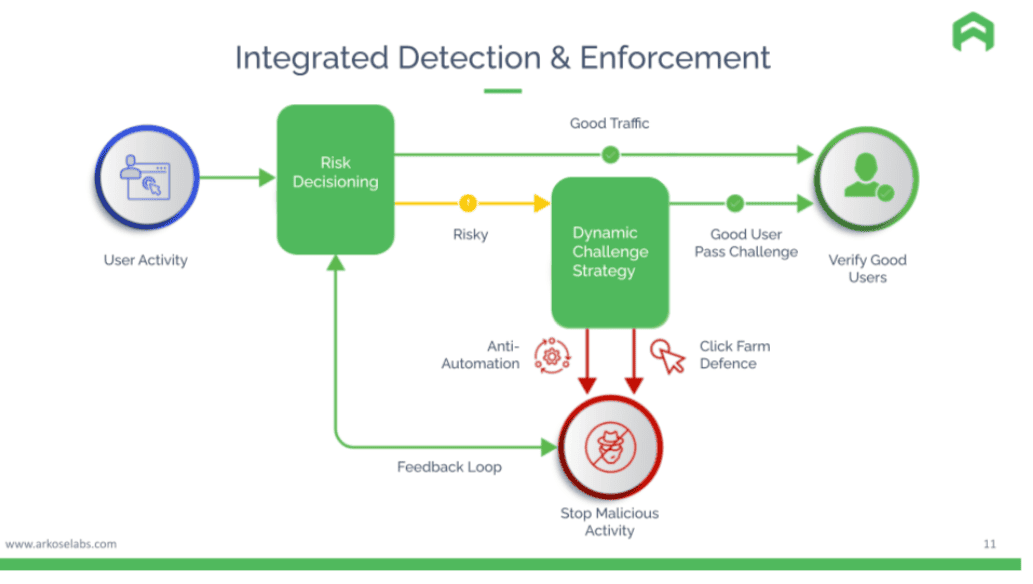
Integrate dynamic enforcement with existing risk decisioning
Arkose Labs proposes an integrated approach where an existing risk-based authentication solution – a pure bot-mitigation solution, combination of bot-mitigation, device ID behavior and analytics, or even a homegrown decision engine – is integrated with dynamic enforcement challenges. These challenges continuously sift through the risky traffic in the gray area to detect bots, stop automated attacks, and resurrect good users, if any.
The output of the challenge – whether the user successfully solved it or not – is fed back into the risk engine, which enables it to continuously learn and update the detection rules. The performance of these rules determines their automatic promotion or demotion in the primary policy. It also helps businesses filter out automated and bot-driven traffic, regardless of the sophistication of the attacker – preventing the need for a downstream MFA flow.
Attackers put up a tough fight
Attackers don’t give up that easily though; they try to defeat the challenges using three key techniques as described below:
- Generic machine learning: To solve common object-type challenges – such as pick a bridge or pick a dog – using ML models trained on publicly available image data.
- Perceptual hashing: To compare images on various parameters such as pixels, dimensions, and the like to find the same images.
- Solvers: Possibly the most sophisticated technique, attackers build solvers specific to the puzzles they are trying to break.
To prevent attackers from solving them at scale, it is essential to make these challenges resilient to the common solving techniques.
Make enforcement challenges resilient to solvers
Some of the features that can help make enforcement challenges resilient include building interactivity, adding randomization such as background lighting, transformation or rotation of the image, and adding variety.
Arkose Labs has built an arsenal of enforcement challenges that employs a combination of these approaches. Not only do we offer hundreds of possible variations of these puzzles, but also ensure easy deployment with the ability to change them during a session, possibly within milliseconds or seconds.
Our challenges comply with global standards, support multiple global languages, and include accessibility features. This makes it easy to deploy them across geographical regions and consumers of varied abilities can use them. Furthermore, we custom-build our challenges to blend in with the branding of the partner business, which adds to the overall user experience and increases good user throughput.
Using Arkose Labs dynamic enforcement challenges in conjunction with an existing risk decisioning at the onboarding or log in levels, can help businesses prevent bots and automated scripts from abusing their costly MFA flows.
To learn more about our proprietary, adaptive step-up enforcement challenges, book a demo now.
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Himanshu Bari. Read the original post at: https://www.arkoselabs.com/blog/how-to-use-dynamic-enforcement-to-prevent-bots-from-abusing-mfa/