How To Hack into a Digital Account in a Few Easy Steps
Account security should be one of the biggest priorities for digital businesses today. Whether you are currently the frequent target of attacks or not, these persistent threats ultimately affect every business. Ensuring that user accounts are protected is paramount. Failing to do so can affect revenue, user experience, customer retention, and much more. Furthermore, this is an enterprise-wide issue; account security affects many different teams including fraud, infosec, customer support, and product. However, businesses are dealing with more threats to account security than ever before. ATO attacks are rising in both frequency and severity, and the reason for that is they are generally profitable for attackers. Attackers, like anyone else, get up each day and go to work to make a living. They don’t do this for fun. They do this because it makes them money. That’s why businesses have to stay one step ahead of attackers by learning what tactics they’re using to circumvent account protections and why they’re successful.
A Rising Tsunami
ATOs now account for about 5% of all digital traffic. That is a stunningly high figure. It means that millions of account takeover attacks are happening on a daily basis at any given moment.
One reason for this is that ATOs are a good entry point for the enterprising person looking to start a career in fraud. Years of massive data breaches have made it easy to acquire combo lists of usernames and passwords. The tools to launch ATO attacks at scale are readily available and there are even YouTube tutorials on how to run them. There is no need to write code or create your own infrastructure.
A person could start simply, for example, in gaming – using ATOs to gain valuable digital goods and items other players possess. Or to redeem loyalty points from a travel website. They can later move on to attacking more high-value accounts, such as bank accounts. The basics of launching attacks are pretty much the same regardless of what industry they are targeting.
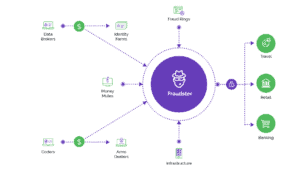
While businesses spend millions annually on cybersecurity, attackers have access to a vast ecosystem that enables them to pull off attacks relatively cheaply.
Hacking into an Account in a Few Easy Steps
So how do attackers, many of whom have little or no technical experience, successfully compromise user accounts and bypass enterprise security? It’s not as hard a process as you may think.
 Step 1. Buy Bots: Automation is the key to launching ATO attacks profitably. If an attacker can launch enough attacks at scale, only a small percentage need to be successful. There are numerous bot marketplaces where even the novice can purchase automated scripts to carry out account takeover attacks.
Step 1. Buy Bots: Automation is the key to launching ATO attacks profitably. If an attacker can launch enough attacks at scale, only a small percentage need to be successful. There are numerous bot marketplaces where even the novice can purchase automated scripts to carry out account takeover attacks.
Step 2. Acquire Combolists: Combo lists are known username and passwords for digital accounts that have been leaked and are sold in various locations. Due to years of data breaches, this information is widely available. Attackers use automation to try different combinations of these usernames and passwords until they find matches. If they need more compute power to launch massive attacks at scale, that is readily available as well. They can buy SaaS software to load combo lists and launch attacks at scale with ease. Many of these come in premium tiers that also feature customer support.
 Step 3. Proxy IPs: Proxy IPs are readily available, and enterprise plans allow fraudsters to buy hundreds of thousands for an economical price. These are vital in helping an attacker obfuscate their true identity and making bots look like they are legitimate traffic. This helps them avoid detection and carry out attacks unnoticed.
Step 3. Proxy IPs: Proxy IPs are readily available, and enterprise plans allow fraudsters to buy hundreds of thousands for an economical price. These are vital in helping an attacker obfuscate their true identity and making bots look like they are legitimate traffic. This helps them avoid detection and carry out attacks unnoticed.
Step 4: Defeat MFA (if necessary) Many accounts are protected by some form of multifactor authentication. If so, this requires an extra step for an attacker to take to compromise an account, and it is something they have become very adept at doing. One way is using a method known as SIM swapping. This is where a fraudster contacts a wireless carrier, convinces the call center rep that they are the real owner of a phone number and convinces the call center rep to switch the SIM card linked to the real user’s phone number to one in their possession. Fraudsters also use phishing or vishing tactics to bypass MFA. For example, they may send a fake –but very real-looking email– to a user purporting to be from their bank and asking for information. Or it may take them to a fake login page meant to look like the bank’s real login page.
Step 5. Monetize: Once they have successfully compromised an account, attackers have numerous ways to monetize it. They can simply drain funds from the account, if applicable. They can also resell personal information to other bad actors, or use it as a way to launder money. Often, the route of monetization changes depending on the industry they are targeting.
How Fraudsters Target and Monetize Attacks Across Industry
Financial Services/Fintech
These are typically the most valuable accounts for fraudsters to target, since they not only can directly drain funds from them, but they also contain sensitive information like social security numbers, addresses, and more. Since financial accounts are so valuable they are usually highly protected and have an additional layer of security such as 2FA. Fraudsters get around this by using tactics such as SIM swaps (we’ll get more into this later). They also use phishing campaigns; typically sending emails that look like they are from a bank, asking the recipient to click on a malicious link and log into their account to confirm their identity. The login page is actually fake and instead provides the fraudster with that user’s information.
Gaming
Gaming accounts are generally much less valuable than financial ones but also much easier to hack into, as they are less protected. Fraudsters run credential stuffing attacks at scale to break into these accounts. Attackers hack into accounts to steal digital goods and items to resell to other gamers on gray market forums; this is known as real money trading. They also use these compromised accounts to use cheats or hacks to gain advantages in-game. Typically when gaming platforms notice this they ban the offending account, but the fraudster can keep doing this over and over again with newly compromised accounts.
Travel:
With travel sites, fraudsters are generally going for loyalty points. They can look and see if there is a stored payment mechanism in the account and use that, but mostly they are looking to use loyalty points to buy hotels, airfare, car rentals, and cruises. They may book these for personal use but more often they do it to then resell on a third-party platform.
Social Media:
This is an interesting area because there is no direct dollar value from social media accounts. They don’t contain financial information or any other sort of PII. Fraudsters instead use these accounts for other reasons, such as to send spam and phishing messages to real users on the platform, to spread disinformation, or to artificially “like” other accounts they may be associated with. In some cases, fraudsters can also resell valuable accounts, such as those with only a few characters or unique names, because they are rare.
Streaming Services:
Since there is not a massive amount of money to be made on streaming accounts, here fraudsters’ goal is to launch credential stuffing attacks against streaming services at scale to gain access to as many accounts as possible and resell access to others. So if a person is paying $15/month and their account gets hacked, the fraudster might sell access to that account to any number of people for a one-time fee of a few dollars each.
How to Truly and Effectively Stop ATO Attacks
It might seem a thankless task to stop ATOs, given the tools fraudsters have at their disposal. But there is one surefire way to ensure these attacks stop, or at least that they don’t target your business. And that’s eliminating the economic incentive behind fraud attacks.
To do this, you need to focus on what fraudsters are after rather than just implementing tools and technology to block them. Work backward to figure out how they get money out of your platform and how to make that more difficult. It could be by making it more costly to buy proxies by utilizing robust IP intelligence. Or device fingerprint forcing them to invest in more software. You can trigger additional step-up measures for suspicious traffic. It’s important to not just rely on passive signals, as fraudsters can not only get around those, but it also can lead to false positives.
By making the ratio unbalanced on how much time and money fraudsters have to spend on attacks versus what they get out of them, ultimately they will move on and do something else. That’s the most effective way to stop fraud.
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Lizzie Clitheroe. Read the original post at: https://www.arkoselabs.com/blog/how-to-hack-digital-account-few-easy-steps/



