Home » Security Bloggers Network » How Large Organizations Can Easily Scan for Log4j Vulnerabilities
How Large Organizations Can Easily Scan for Log4j Vulnerabilities
The Log4j vulnerability may not have changed everyone’s world, but it certainly provided an end of year wake up call for the entire software development world. Notably, it’s highlighted that critical systems are more than just connections and software. They are software components. As more and more customers have crucial software projects in development within their organization, these vulnerabilities are an ongoing concern.
To help find and resolve issues, Sonatype’s Nexus Lifecycle includes tools to quickly integrate with source control management (SCM) systems such as Github, GitLab, Bitbucket, etc. This integration helps avoid open source risk and maintain effective governance down the road. And, it is especially useful for enterprise organizations with an extremely large number of applications who need to find Log4j – or any vulnerability – quickly.
Rapid Onboarding
Sonatype Nexus Lifecycle customers can use Easy SCM Onboarding to connect to repositories and create Lifecycle Applications from an SCM system. See how to get started below.
Currently, Easy SCM Onboarding is designed to quickly onboard, configure, and scan up to 15 applications at a time. This enables rapid visibility into open source risks for critical applications.
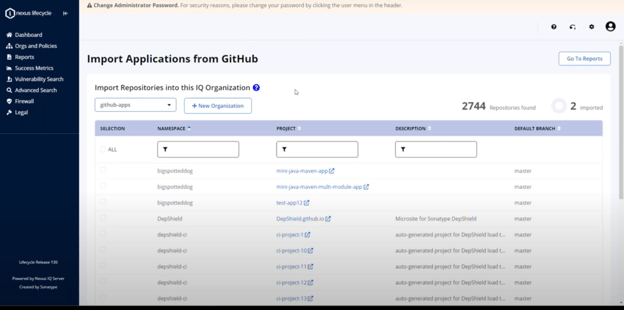
Once created, the applications are automatically scanned for issues, including problematic Log4j components.
Source Analysis
As new applications are onboarded, Instant Risk Profile feature performs source control evaluations. As the name implies, this provides immediate feedback on source code issues, as well as ongoing assessments.
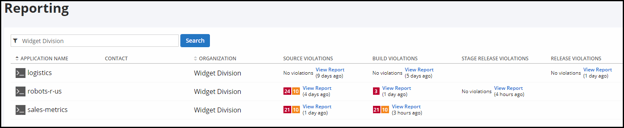
With it, teams can begin to identify vulnerabilities in direct dependencies that show up explicitly in a project’s build manifest files.
For transitive dependencies, we recommend that you integrate with our Nexus IQ CI, CLI or Maven plugins. These dependencies include those not directly found in a project’s build manifest files, but instead required by your direct dependencies,
Best Practices
Although every company is (Read more...)
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Rishav Mishra. Read the original post at: https://blog.sonatype.com/how-large-organizations-can-easily-scan-for-log4j-vulnerabilities






