Four Secrets to Help You Stop Fraud Attacks Long-Term
Today, bad actors that attack digital businesses and user touchpoints rely on a complex ecosystem to help them successfully carry out their work. While businesses are up against an organized and formidable enemy, they can still successfully stop cyberattacks by undermining the ROI behind them. If attackers can’t make money, they will stop what they are doing. It’s as simple as that.
As things stand, attackers are able to share data and tools to launch scripted attacks freely among themselves to attack multiple businesses. These tools are often tested on one company’s website and, if they prove successful, rolled out at scale across the digital commerce landscape. They are highly scalable and easily repeatable, which means attackers spend relatively little time and money on attacks.
Fighting these attacks can be difficult for businesses because they typically deploy defenses to stop specific attacks, which then, in turn, causes attackers to pivot and leads to a perpetual cat-and-mouse game. The secret to tackling the range of attack methods is to find ways to increase the time, cost, and effort it takes for bad actors to carry out attacks. Some examples of this could be by making it more costly for attackers to buy proxies by utilizing robust IP intelligence. Or device fingerprint forcing them to invest in more software. The point is, by making their attacks more costly and time-consuming, it compels attackers to stop. Here are the top steps to do just that.
Take a Zero Tolerance to Bad Bots
Bots are the key to making fraud attacks profitable. Bots enable attackers to go after a massive amount of targets with minimal effort and expense. It’s this scale that makes attacks profitable.
Now of course there are some good bots, such as search engine bots, but we are talking about automation used for malicious purposes, such as credential stuffing, scraping, or inventory hoarding.
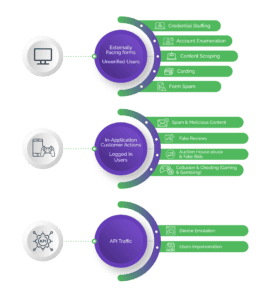
Businesses need to take a multi-layered approach to identify and root out automated attacks. This should involve dynamic evaluation of traffic in real-time, segmenting traffic based on suspicion level, and then delivering an appropriate response, such as step-up challenges that are designed against machine vision technology and can stop bad bots in their tracks.
Leverage Shared Intelligence
Sharing intelligence among trusted businesses can also ensure that existing attacks cannot be copy-and-pasted across different organizations. Patterns will very quickly emerge that are give-aways of a malicious session when analyzing risk signals across a global network.
Sophisticated analysis of visitor behavior from the very beginning of the customer journey is a must today; by weeding out bad actors at the perimeter, businesses can prevent a whole host of costly and damaging downstream abuse.
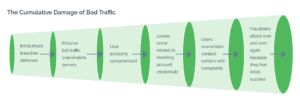
Criminals often launch the same attacks against many different targets; with a global view of attack patterns, these can be easier to identify and stop before they wreak havoc on businesses and consumers.
Combine Robust Detection with Step-Up Authentication
Businesses need a detection platform that can determine intent and actions, rather than merely collecting identity data. This means carrying out deep analysis of traffic and segmenting all suspicious activity to then be dealt with appropriately
Many attackers utilize proxies to mask their true identity when attacking a business. This can make bad bots and malicious humans appear different than they actually are, by obfuscating their geography, IP address, and other identifying factors. Businesses need to collect and analyze real-time intelligence to unearth fraudulent behavior across devices and networks.
 Analytics and Machine Learning
Analytics and Machine Learning
 Customer Interaction Assessment
Customer Interaction Assessment
 Anomaly Detection
Anomaly Detection
 Historical Attack Patterns
Historical Attack Patterns
 Traffic Pattern Analysis
Traffic Pattern Analysis
Then, when needed, adaptive step-up enforcement can be served to potentially suspicious traffic. This frustrates and wastes attackers’ time and resources.
Shift the Fraud Attack Surface
Attackers rely on being able to control decision points when on a business’ digital property and deploying the appropriate tactics to evade established anti-fraud measures. They are skilled at masquerading as legitimate consumers using hijacked devices, stolen identities, and obfuscating their IP address and other identifiers in single request attacks.
It’s time to take control away from fraudsters. Businesses can really benefit from using third-party solutions to act as a buffer between them and the bad actors that are so experienced at attacking them.
Doing so shifts the attack surface by redirecting suspicious sessions to an intermediate battlefield where they play by your rules. Reclaiming control of these decision points means fraudsters will quickly become frustrated when their tried and tested methods cease to work. When they can no longer fall back on their existing arsenal of automated tools, stolen identities, and click farms, this will lead to escalating costs for reduced gains, removing the financial motivation behind organized fraud
The Arkose Labs Approach to Stopping Fraud Attacks
Arkose Labs takes a unique approach to attack prevention and user security, one that seeks to undermine the financial incentive behind attacks, thus dissuading bad actors from even launching attacks in the first place. A key success factor of the platform is seeing attacks not just detected, but drop off, providing longer-term solutions.
The Arkose Labs Fraud and Abuse Platform combines real-time intelligence, rich analytics, and adaptive step-up challenges to progressively diminish the profitability of attacks while adapting to evolving attack patterns.
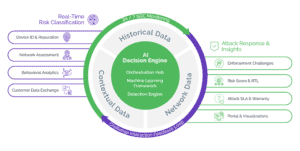
Rather than outright blocking traffic and negatively impacting the user experience, the Arkose Labs approach is to use targeted friction, which is reserved purely for high-risk traffic. Our custom enforcement challenges are context-based, adaptive visual challenges that will thwart both automated and human-driven account takeover attempts, wasting fraudsters time and resources. Due to a sophisticated decision engine, the vast majority of good users can pass unchallenged.
By making the ratio unbalanced on how much time and money fraudsters have to spend on attacks versus what they get out of them, ultimately they will move on and do something else. That’s the most effective way to stop fraud for good.
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Bryan Yurcan. Read the original post at: https://www.arkoselabs.com/blog/four-secrets-to-help-you-stop-fraud-attacks-long-term/




