Best practices in WAF gateways to meet the demands of digital transformation
Every day, digital transformation is changing every organization’s threat landscape. As a result, they are facing a dilemma about where and how to deploy their application security solution. One of the most common approaches that organizations take is to deploy a reverse proxy security solution in front of their API Gateway.
Most common cloud-native architectures will have a reverse proxy as part of their environment, regardless of the security solution, whether as an API Gateway or as a side car within a service mesh solution. When operating in such environments, a security solution can leverage the existing reverse proxy capabilities which they already possess as part of their cloud architecture.
There is a catch to this approach, however. Deploying a reverse proxy security solution in front of an API Gateway cannot protect the east-west traffic, so today organizations must find an effective solution. One best-practice single approach you can take is to locate the security solution inside the cloud-native environment and leverage both the API Gateway proxy capabilities as well as the sidecar proxy capabilities in order to gain maximum coverage of all traffic.
What to look for in an ideal application security solution
First, an ideal security solution for SecOps and DevOps consumers should be as transparent as possible, fully integrated within the environment and with a minimal effect on the business, except for the protection on the business services. Second, an ideal security solution should be able to be immutable and reduce to a minimum these major side effects:
- Being a single point of failure in the critical path of the data flow
- Adding latency to the end customer experience
Solutions that are putting all their logic into their existing reverse proxy itself may become very costly to maintain.
To meet the changing threat landscape, cloud architects need flexibility. Namely, the ability to replace their cloud infrastructure when needed. For example, replacing the Ingress controller or replacing the API Gateway and facilitating a relatively smooth and easy migration of the security solution when changing the architecture (e.g., moving to service mesh).
In general, organizations migrate to a new cloud native architecture gradually, which makes the ability to transition their security solution easily critically important.
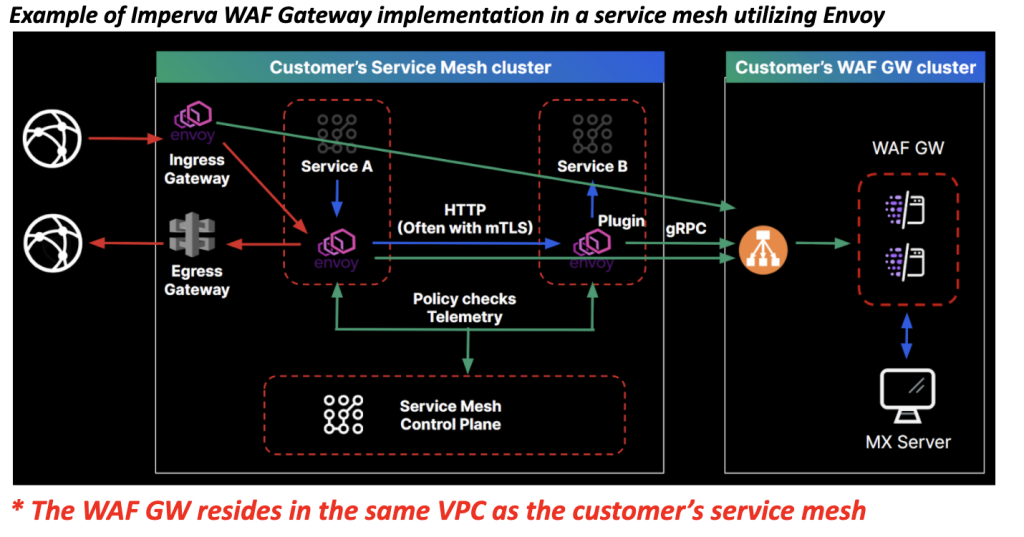
The engineers behind Imperva’s WAF Gateway have been working tirelessly to meet the changing threat landscape directly and enable organizations’ smooth digital transformation leveraging their existing security investment. You can see that in new product features and functionality development over the last few years. For many years Imperva’s WAF Gateway has been a best of breed WAF solution (recognized by Gartner and Forrester as a leader), offering essential security functionality for new environments. Until recently WAF Gateway was implemented as an external protective component on the direct route from the client to the protected upstream services. From V14.5 and on, in addition to the existing WAF Gateway implementation capabilities that can be implemented as part of the cloud native infrastructure itself by leveraging the existing reverse proxy capabilities (e.g., service mesh-based), new functionality now enables the WAF Gateway to sit outside the critical data path, reducing one proxy in the flow and providing a single unified security solution for both north-south as well as east-west communication.
With V14.5, configuring the WAF Gateway in cloud-native environments is now much easier with the ability to support a “WAAP Anywhere” configuration. This is because unlike in a reverse proxy implementation which needs to configure a reverse proxy rule for each endpoint it protects, with this new functionality the configuration is managed entirely by the service mesh control plane and propagated into the specific sidecar proxies (e.g., Envoy, NGINX) paired with the protected containers. The WAF Gateway will only need a shared listener that is unaware of the actual endpoints it protects to accept processing requests.
For Imperva application security users, V14.5 enables them to leverage the existing investment they already have made over the years in their WAF Gateway and then leverage it as the WAF for their cloud-native environment. New users can get our best of breed, full blown WAF capabilities, both for north-south as well as east-west traffic within their cloud-native environment.
The WAAP Anywhere configuration also enables existing customers who are transitioning gradually into such cloud-native environments, to leverage the WAF Gateway management for both on-premises data centers as well as their different cloud implementations.
Imperva WAF Gateway is the right technology for the challenges imposed from digital transformation
As we said, digital transformation and the threat landscape it creates is challenging the way we think about application security. The approaches we depended upon to secure our on-premises environments are simply not applicable to cloud-native architectures. V14.5 enables users to locate the security solution inside the cloud native environment and leverage both the API Gateway capabilities and the sidecar proxy capabilities to achieve maximum coverage of traffic inspection. Users get the protection of north-south traffic and security for east-west traffic within the cloud architectures offered by their WAF Gateway.
Are you ready to talk about WAAP Anywhere with an Imperva Representative? Whether an existing customer operating a legacy environment or you are “born in the cloud,” we have answers to your application security questions. Contact us today to learn more.
The post Best practices in WAF gateways to meet the demands of digital transformation appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by eyalgur. Read the original post at: https://www.imperva.com/blog/best-practices-in-waf-gateways-to-meet-the-demands-of-digital-transformation/





