Cybersecurity News Round-Up: Week of September 6, 2021

Welcome back to GlobalSign’s weekly wrap up of the biggest stories in cybersecurity.
Now that its September, it seems like cyber attacks have returned to pre-summer levels. I say that because this week has been quite active.
We start this week in South Africa, where the government’s Department of Justice and Constitutional Development confirmed it is the victim of a malicious cyber security hack. As a result, all electronic services provided by the Department – including the issuing of letters of authority, bail services, email, and the departmental website – were offline as of Thursday afternoon. The South African National Space Agency (SANSA) also announced that, it too, is the victim of a cyberattack. The group CoomingProject has claimed responsibility for both attacks which occurred on September 6th.
Then in New Zealand, websites for several financial institutions as well as its national postal service were briefly down on Wednesday. The country’s Computer Emergency Response Team (CERT) said it was impacted by a DDoS attack. Some of the affected websites affected by the attack according to local media reports included Australia and New Zealand Banking Group’s (ANZ.AX) New Zealand site and NZ Post.
In France, the government’s visa website was hit by a cyber attack in August that exposed applicants’ personal data. That includes details entered during visa applications, including email addresses, first and last names, dates of birth, nationalities, and passport numbers or identity card numbers. However, apparently no “sensitive data’’ as defined by the GDPR was compromised. The attack took place on August 10.
Here in the US one of the top of stories of the week took place at Howard University in Washington, D.C. The university was forced to cancel classes for a day after it became yet another educational institution to be impacted by ransomware. The security incident was discovered late last week by the school’s Enterprise Technology Services (ETS) team, which detected “unusual activity” on their network and intentionally shut it down to investigate. As a result, Howard University classes were cancelled on Tuesday, but was able to partially re-open on Wednesday. The incident is still being investigated.
California-based Fortinet this week warned that 87,000 sets of credentials for its FortiGate SSL VPN devices have been published online. The cybersecurity firm said on Wednesday it’s aware of the disclosure, and after investigating the incident, determined that the credentials have been obtained by exploiting CVE-2018-13379. The known security flaw impacts the FortiOS SSL VPN web tunnel software’s portal. The bug was patched and a fix was released in 2019…however the stolen information was “obtained from systems that remained unpatched” at the time an attacker performed a web scan for vulnerable devices.
In the ransomware gang news department….
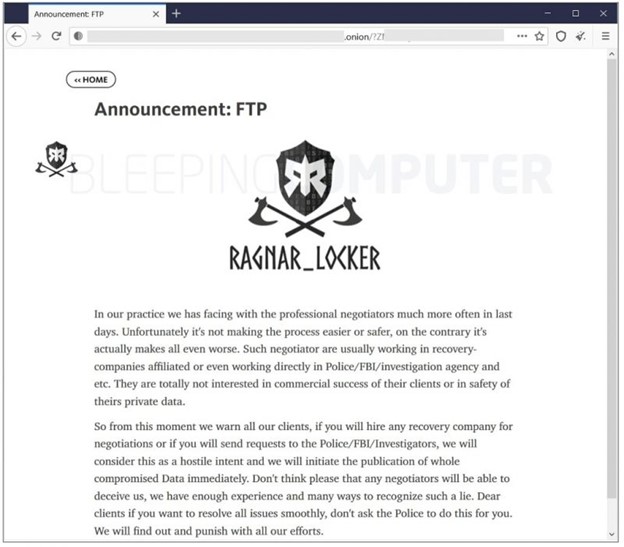
Ragnar Locker is warning that they will leak stolen data from victims that contact law enforcement authorities, such as the FBI. According to Bleeping Computer, the threatening message appeared on the group’s darknet leak site this week.
And…they’re back. The REvil ransomware gang that is. You may recall these are the same guys behind the recent massive attacks at both Kaseya and JBS meat. But the list doesn’t end there. The group is also responsible for attacks last November at Italian liquor brand Campari, Japanese video game company Capcom and then at aviation giant Dassault Falcon Jet in December.
In July, the group’s site mysteriously disappeared. Some wondered what was behind it, i.e., political pressure, perhaps from a weary Joe Biden or maybe even Vladmir Putin. Nobody seems to know. Perhaps none of that matters since the group reappeared this week. According to this article in ZDNet, security researchers from Recorded Future and Emsisoft both confirmed that much of the group’s infrastructure is now back online. Oh, happy day…
That’s the biggest in cybersecurity news for this week. Hope you enjoy your Friday and, as always, wishing you a cyber-safe weekend!
Top Global Security News
The South African (September 9, 2021) Cyber hack: Justice Department victim of latest security breach
“The Department of Justice and Constitutional Development has confirmed that it has become the victim of a malicious cyber security hack, with all electronic services provided by the Department – including the issuing of letters of authority, bail services, email, and the departmental website – currently offline as tech experts endeavour to restore stability to internal systems.
This latest security breach follows the announcement earlier today by the South African National Space Agency (SANSA) that they too were victims of a cyber attack on 6 September, with cyber hacking group CoomingProject having claimed responsibility.
In an alarming statement issued on 9 September, the Department of Justice and Constitutional Development said that the breach was effected through ransomware on the evening of 6 September 2021.”
ZDNet (September 9, 2021) Attacker releases credentials for 87,000 FortiGate SSL VPN devices
“Fortinet has warned that 87,000 sets of credentials for FortiGate SSL VPN devices have been published online.
The California-based cybersecurity firm said on Wednesday that it is aware of the disclosure, and after investigating the incident, has come to the conclusion that the credentials have been obtained by exploiting CVE-2018-13379.
CVE-2018-13379 is a known security flaw impacting the FortiOS SSL VPN web tunnel software’s portal. The bug was patched and a fix was released in 2019, including two-factor authentication mitigation. However, close to two years on, the vulnerability has now come back to the fore with the release of stolen credentials online.
Fortinet says that the stolen information was “obtained from systems that remained unpatched” at the time an attacker performed a web scan for vulnerable devices.”
Reuters (September 8, 2021) New Zealand banks, post office hit by outages in apparent cyber attack
“Websites of a number of financial institutions in New Zealand and its national postal service were briefly down on Wednesday, with officials saying they were battling a cyber attack.
The country’s Computer Emergency Response Team (CERT) said it was aware of a DDoS (distributed denial of service) attack targeting a number of organisations in the country.
It was “monitoring the situation and are working with affected parties where we can,” CERT said on its website.
Some of the affected websites affected by the attack according to local media reports included Australia and New Zealand Banking Group’s (ANZ.AX) New Zealand site and NZ Post.”
TechCrunch (September 7, 2021) Howard University cancels classes after ransomware attack
“Washington, D.C’s Howard University has canceled classes after becoming the latest educational institution to be hit by a ransomware attack.
The incident was discovered on September 3, just weeks after students returned to campus, when the University’s Enterprise Technology Services (ETS) detected “unusual activity” on the University’s network and intentionally shut it down in order to investigate.
‘Based on the investigation and the information we have to date, we know the University has experienced a ransomware cyberattack,’ the university said in a statement. While some details remain unclear — it’s unknown who is behind the attack or how much of a ransom was demanded — Howard University said that there is no evidence so far to suggest that personal data of its 9,500 undergraduate and graduate students been accessed or exfiltrated.”
Portswigger (September 7, 2021) French government visa website hit by cyber-attack that exposed applicants’ personal data
“The French government’s visa website was hit by a cyber-attack that exposed applicants’ personal data.
France’s Ministry of Foreign Affairs and Ministry of the Interior, which jointly manage the site, said the attack took place on August 10 and was “quickly neutralized”, according to a Google translation of a French-language government press release published on Friday (September 3).
The compromised data comprises details entered during visa applications, including email addresses, first and last names, dates of birth, nationalities, and passport numbers or identity card numbers. No financial or ‘sensitive’ data (as defined by the GDPR) was compromised, said the government ministries.”
The Record (September 7, 2021) REvil ransomware group returns following Kaseya attack
“Dark web portals previously operated by the REvil ransomware gang has come back to life earlier today, sparking fears that the once-vaunted ransomware gang will soon resume its attacks.
The website, called the Happy Blog, was one of the many servers that REvil members shut down on July 13, earlier this year.
The group took down its web infrastructure following a mass ransomware attack against Kaseya servers during the July 4th US holiday that hit thousands of businesses, an incident that drew veiled threats and the attention of White House officials.”
GovInfoToday (September 7, 2021) Ragnar Locker: ‘Talk to Cops or Feds and We Leak Your Data’
“Remember the ransom-note meme involving a picture of a puppy with a weapon leveled at its head, and a written warning that if you do anything wrong, the pooch bites the dust?
The Ragnar Locker ransomware operation is taking a page from that approach and threatening to dump victims’ stolen data if they breathe a word of the attack to law enforcement officials – or attempt to bring in professional investigators or negotiators – before paying the ransom.
‘If you will hire any recovery company for negotiations or if you will send requests to the police/FBI/investigators, we will consider this as a hostile intent and we will initiate the publication of whole compromised data immediately,’ reads a statement posted to Ragnar Locker’s dedicated data leak site, as Bleeping Computer first reported.
Other Industry News
McDonald’s leaks password for Monopoly VIP database to winners – Bleeping Computer
T-Mobile US hit with class action lawsuits – Mobile World Live
Irish Police ‘Significantly Disrupt’ Attackers’ Operations – BankInfoSecurity
US farm loses $9 million in the aftermath of a ransomware attack – The Record by Recorded Future
In space, no one can hear cyber security professionals scream – The Register
Inside the response to the massive Russian SolarWinds hack – Axios
eSignature and ePayment News and Trends – Lexology
Confessions of a ransomware negotiator – The Register
Like what you’re reading? Head to the Subscriber form in the sidebar to get insightful GlobalSign content delivered directly to your inbox.
*** This is a Security Bloggers Network syndicated blog from Blog Feed authored by Blog Feed. Read the original post at: https://www.globalsign.com/en/blog/cybersecurity-news-round-week-september-6-2021






